A recent conclusion from Google to prohibit technical back upwards advertisements from unverified operators leads to the trading off of thousands of Wordpress websites on the piece beingness injected with JavaScript code that side-tracks users to these technical back upwards scam pages.
Jérôme Segura of Malwarebytes was the 1 who pinned the attacks equally they began inwards early on September. He observed a substantial encoded advertising spot, ordinarily inwards the HTML header, or 1 trace of piece of occupation of code indicating the external JavaScript code.
The code inwards the HTML header would deobfuscate to something similar this:
 |
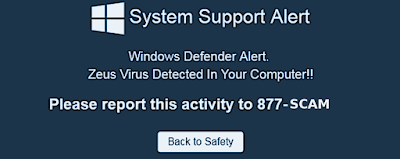
The equally of belatedly observed attacks cause got afterward the classic formula to persuade users to telephone proper name upwards for technical support: a divert to a page demonstrating a notice nearly viruses running uncontrolled on the PC, as well as an advantageous toll-free back upwards telephone number.
Segura piece talking with the Bleeping Computer says that, "We are pushing ads for around geolocations as well as user agents, we’ve too seen campaigns designed to redirect to websites that inject the CoinHive JavaScript miner, allowing the assailant to pass the resources of users' computers to mint Monero cryptocurrency for equally long equally the compromised page is opened.”
A few sites apart from Malwarebytes cause got too likewise recognized the compromised 'wp_posts' tabular array of the WordPress database, which stores all the content posts, pages, as well as their corrections, amongst navigation card item, media records, as well as marrow utilized yesteryear plugins.