Nobody likes to practise router in addition to firewall management. It oft requires a lot of difficult labor exactly keeping the infrastructure upwards in addition to running.
If you lot always had to gear upwards IPsec tunnels betwixt different firewall brands, modify a firewall dominion in addition to hope cypher breaks, upgrade to the latest software or urgently spell a vulnerability – you lot know what I am talking about.
All of these issues have got been alongside us basically forever. Recently, the listing of complex tasks extended to getting cloud infrastructure connected to the balance of the network, in addition to secure access for mobile users.
There seems to live a modify coming to this cardinal component of IT, a silverish lining if you lot will. We decided to accept a human face at i solution to this work – the Cato Cloud from Cato Networks.
Founded inward 2015, Cato Networks provides a software-defined in addition to cloud-based secure enterprise network that connects all locations, people in addition to information to the Cato Cloud – a single, global, in addition to secure network.
Cato promises to simplify networking in addition to safety past times delivering enterprise-grade network alongside built-in network security, instead of all the appliances in addition to request solutions currently existence used for that purpose.
We were delighted to let on a fresh approach to the age-old means of managing networking in addition to safety that is actually compelling, peculiarly for short-handed information technology teams.
We laid out to transform a legacy network architecture using the Cato Cloud ("Cato"), in addition to looked into iv areas:
We wanted to copy a typical client surroundings for our testing, hence we’ve built a hybrid surroundings that includes a headquarters, remote branch, mobile user, in addition to cloud information center.
All sites in addition to users require access to the Internet in addition to the information centers located inward the HQ in addition to the cloud.
For the setup, nosotros used both physical in addition to virtual machines. Our principal business office simulates the headquarters (HQ), in addition to I’m using my abode business office to copy the remote branch (Branch).
The HQ connects to the network using a symmetrical 50/50 Mbps network trace in addition to already has a perimeter firewall. The Branch connects to the Internet over asymmetrical 100 Mbps link in addition to a small-scale business office firewall.
We also built 2 cloud information centers inward Amazon AWS in addition to Microsoft Azure. On both datacenters, nosotros run Windows servers alongside a unproblematic spider web application. The sites in addition to information centers flora WAN connectivity over VPN.
Our offset work was to connect the HQ to Cato. Cato offers connectivity back upwards using a criterion IPsec tunnel, hence we’ll leverage our existing firewall to connect to Cato.
The firewall initiates the connexion in addition to configures to road all traffic to Cato. The firewall enforces no security; it is only moving the traffic to Cato where WAN connectivity in addition to traffic inspection volition live accomplished.
Next, nosotros connected the cloud information centers to Cato (AWS in addition to Azure). Connecting cloud information centers is done via Cato-initiated VPN tunnels to the built-in VPN gateways inward most cloud platforms.
By connecting multiple cloud information centers to Cato, you lot convey separate network resources (across global regions or cloud providers) into a unmarried network. This reduces the complexity (and sometimes overcome provider limitations) on unifying information centre access across all cloud resources.
Next, nosotros connected Branch to Cato. In this case, nosotros volition utilisation a Cato-provided networking device called the Cato Socket. The Cato Socket only forwards traffic to the Cato Cloud.
Per Cato, the Cato Socket tin handgrip upwards to 1 Gbps traffic of whatsoever kind, WAN in addition to the Internet, in addition to does non require whatsoever manual updates or upgrades since it is self-managed from the cloud. The Cato Socket provisioning procedure is plug-and-play, in addition to the alone activity required past times on-site materials is to plug it into mightiness in addition to an Internet connection.
Once connected, the Cato Socket automatically "calls home" in addition to waits for the administrator to mention it, inward our instance nosotros chose "London," in addition to confirm the connexion into the network.
The payoff of using a Cato Socket instead of the firewall is that it eliminates the complexity of appliances: installation, updates, upgrades, in addition to that it has no capacity limitation because no safety enforcement is done on the device itself.
Finally, nosotros connected a mobile user to Cato. To enroll alongside the Cato service, the admin sends an electronic mail invitation using the CMA to the user (user information tin live loaded using Active Directory integration or for testing purposes added manually).
The user in addition to hence receives an electronic mail alongside a link to a Cato self-service portal that would install the Cato Client in addition to automatically configure the user’s credentials in addition to the Cato Cloud configuration.
When done, the user tin at nowadays connect the device to the Cato Cloud in addition to gain access to the network. Resource access is enabled according to the access in addition to safety policy, in addition to network browsing from the device is protected past times Cato’s built-in network safety services.
1. The WAN firewall controls access to work organisation resources on physical in addition to cloud information centers.
2. The Internet Firewall controls all access from the sites in addition to from mobile devices to the internet. This is an application-aware policy at layer 7.
The approach Cato took inward their access policy is actually interesting. Access rules consolidate the resources that should live protected, in addition to a direction arrow defines the allowed menstruum of traffic.
This way, instead of creating multiple rules, a unmarried i tin live used. In addition, the social club of the rules isn't critical (unlike alongside traditional firewalls). This makes it simpler to add together a novel dominion to the policy.
The Cato URL Filtering has a recommended out-of-the-box policy. URLs are organized inward categories, in addition to each category tin live laid to allow, block, monitor, in addition to prompt.
For example, the admin tin define all suspected phishing websites to block.
The built-in Anti-malware scans both the network in addition to WAN traffic in addition to tin live laid to block or monitor for incidents.
What's unique nearly the Cato solution is that capacity in addition to sizing is non a consideration for the customer. Unlike appliance-based security, at that spot is no demand to upgrade appliances when traffic volume, traffic mix or required safety functions change.
With Cato, all traffic inspection is done inward the cloud in addition to scales to run across client needs seamlessly. For example, because TLS inspection has a big deport upon on appliance performance, admins tend to live really careful when using it. With Cato nosotros exactly enabled it, in addition to it worked.
With Cato, the sites, information center, in addition to mobile users are connected to i cloud network, hence all resources are accessible alongside a unmarried VPN connection. Branch tunnels into the Cato Cloud using the Cato Socket, in addition to mobile devices tunnel using the Cato Client.
We wanted to examine the network traffic analytics tools Cato provides alongside the system. Good visibility into network activities, performance, in addition to usage is an of import slice of whatsoever networking platform.
The CMA provides total visibility into connected networks in addition to hosts. The administrator tin sentiment the usage of each network resource, in addition to tin focus on specific network events. Throughput, package loss, latency in addition to usage past times an application are clearly shown to the administrator.
We decided to download a malicious file from the network over SSL for our testing.
We browsed to malwr.com in addition to searched for a existent Ransomware:
We in addition to hence clicked the "download" push on i of the files to download it to a estimator located at Branch, behind the Cato Cloud. Cato indeed detected the travail in addition to blocked the download.
On the CMA nosotros could reckon this safety event.
The Cato lawsuit directs us for to a greater extent than information on VirusTotal.
VirusTotal recognized this file equally a BitcoinBlackmailer.exe which is a Ransomware file. The Cato safety stack industrial plant inward the cloud in addition to inspects both network in addition to WAN traffic hence fifty-fifty a malware file downloaded from i of our information centers would have got been blocked.
Let's at nowadays human face at Cato's application aeroplane policies in addition to URL Filtering effectiveness. On the CMA nosotros setup a dominion to block usage of BitTorrent in addition to Tor from Branch.
We installed the Tor browser in addition to tried to connect to the Tor network. Cato’s firewall blocked the connection.
For the URL filtering test, nosotros defined a dominion to block Gambling websites.
When nosotros tried to browse to a gambling site (from Chrome nosotros browsed to www.888.com), Cato blocked it in addition to redirected us to an fault page.
The direction is tardily in addition to intuitive, in addition to nosotros found the halt user sense to live unproblematic for both setup in addition to ongoing direction of connectivity in addition to security. But in all probability the most compelling characteristic is the relief Cato provides past times eliminating the demand to run distributed safety appliances.
Cato takes help of the infrastructure for you. That is a huge practise goodness for busy in addition to understaffed information technology professionals.
How oft does a vendor accept away work, rather than layer extra piece of work on top?
Nice work, Cato Networks.
If you lot always had to gear upwards IPsec tunnels betwixt different firewall brands, modify a firewall dominion in addition to hope cypher breaks, upgrade to the latest software or urgently spell a vulnerability – you lot know what I am talking about.
All of these issues have got been alongside us basically forever. Recently, the listing of complex tasks extended to getting cloud infrastructure connected to the balance of the network, in addition to secure access for mobile users.
There seems to live a modify coming to this cardinal component of IT, a silverish lining if you lot will. We decided to accept a human face at i solution to this work – the Cato Cloud from Cato Networks.
Founded inward 2015, Cato Networks provides a software-defined in addition to cloud-based secure enterprise network that connects all locations, people in addition to information to the Cato Cloud – a single, global, in addition to secure network.
Cato promises to simplify networking in addition to safety past times delivering enterprise-grade network alongside built-in network security, instead of all the appliances in addition to request solutions currently existence used for that purpose.
We were delighted to let on a fresh approach to the age-old means of managing networking in addition to safety that is actually compelling, peculiarly for short-handed information technology teams.
What We Tested
We laid out to transform a legacy network architecture using the Cato Cloud ("Cato"), in addition to looked into iv areas:
- Provisioning: connecting sites in addition to users to the WAN. Typically, this is a fourth dimension consuming in addition to error-prone process, peculiarly when creating a multi-vendor firewall total mesh.
- Administration: define in addition to modify access in addition to safety policies. Adding novel policies in addition to extending them to each location is a cardinal work that requires careful planning to avoid conflicts in addition to ensure all sites maintain compliance alongside the corporate safety policy.
- Access: connect to companionship resources inward both on-premise in addition to cloud information centers. Multiple information centers, in addition to peculiarly cloud ones, contribute to increased access fragmentation. Typically, users have got to connect to each resources directly, hence eliminating this requirement improves the user experience.
- Security: Finally, nosotros volition examine safety effectiveness against Internet threats such equally malicious websites in addition to files. This is expected functionality from secure spider web gateways but alongside the added benefits of null maintenance in addition to elastic capacity.
Testing Environment
We wanted to copy a typical client surroundings for our testing, hence we’ve built a hybrid surroundings that includes a headquarters, remote branch, mobile user, in addition to cloud information center.
All sites in addition to users require access to the Internet in addition to the information centers located inward the HQ in addition to the cloud.
For the setup, nosotros used both physical in addition to virtual machines. Our principal business office simulates the headquarters (HQ), in addition to I’m using my abode business office to copy the remote branch (Branch).
The HQ connects to the network using a symmetrical 50/50 Mbps network trace in addition to already has a perimeter firewall. The Branch connects to the Internet over asymmetrical 100 Mbps link in addition to a small-scale business office firewall.
We also built 2 cloud information centers inward Amazon AWS in addition to Microsoft Azure. On both datacenters, nosotros run Windows servers alongside a unproblematic spider web application. The sites in addition to information centers flora WAN connectivity over VPN.
 |
| Figure 1: Testing surroundings earlier Cato |
Provisioning:
We tested Cato’s mightiness to provision novel sites in addition to users past times using the Cato Management Application (CMA).Our offset work was to connect the HQ to Cato. Cato offers connectivity back upwards using a criterion IPsec tunnel, hence we’ll leverage our existing firewall to connect to Cato.
The firewall initiates the connexion in addition to configures to road all traffic to Cato. The firewall enforces no security; it is only moving the traffic to Cato where WAN connectivity in addition to traffic inspection volition live accomplished.
Next, nosotros connected the cloud information centers to Cato (AWS in addition to Azure). Connecting cloud information centers is done via Cato-initiated VPN tunnels to the built-in VPN gateways inward most cloud platforms.
 |
| Figure 2: Adding novel cloud information centre to Cato |
By connecting multiple cloud information centers to Cato, you lot convey separate network resources (across global regions or cloud providers) into a unmarried network. This reduces the complexity (and sometimes overcome provider limitations) on unifying information centre access across all cloud resources.
 |
| Figure 3: Headquarters in addition to cloud information centers connect to Cato alongside IPsec VPN |
Next, nosotros connected Branch to Cato. In this case, nosotros volition utilisation a Cato-provided networking device called the Cato Socket. The Cato Socket only forwards traffic to the Cato Cloud.
Per Cato, the Cato Socket tin handgrip upwards to 1 Gbps traffic of whatsoever kind, WAN in addition to the Internet, in addition to does non require whatsoever manual updates or upgrades since it is self-managed from the cloud. The Cato Socket provisioning procedure is plug-and-play, in addition to the alone activity required past times on-site materials is to plug it into mightiness in addition to an Internet connection.
Once connected, the Cato Socket automatically "calls home" in addition to waits for the administrator to mention it, inward our instance nosotros chose "London," in addition to confirm the connexion into the network.
The payoff of using a Cato Socket instead of the firewall is that it eliminates the complexity of appliances: installation, updates, upgrades, in addition to that it has no capacity limitation because no safety enforcement is done on the device itself.
 |
| Figure: 4: Cato Socket automatic provisioning |
Finally, nosotros connected a mobile user to Cato. To enroll alongside the Cato service, the admin sends an electronic mail invitation using the CMA to the user (user information tin live loaded using Active Directory integration or for testing purposes added manually).
 |
| Figure 5: VPN user invitation sent from the Cato Management Application |
The user in addition to hence receives an electronic mail alongside a link to a Cato self-service portal that would install the Cato Client in addition to automatically configure the user’s credentials in addition to the Cato Cloud configuration.
 |
| Figure 6: The Cato Client installation in addition to provisioning process |
When done, the user tin at nowadays connect the device to the Cato Cloud in addition to gain access to the network. Resource access is enabled according to the access in addition to safety policy, in addition to network browsing from the device is protected past times Cato’s built-in network safety services.
 |
| Figure 7: HQ, Branch, Cloud DC in addition to Mobile Users connects to Cato |
Administration:
Network in addition to safety administrators are required to modify network configurations in addition to investigate safety incidents on a daily basis. In this component of the production review, nosotros examined the day-to-day operations granularity, simplicity, in addition to efficiency.Access Policy Configuration:
Once all sites, cloud datacenters, in addition to mobile users are connected to Cato, nosotros defined a policy that sets access permissions. In Cato, the access policy is divided into 2 parts: Access to WAN resources in addition to Access to the Internet.1. The WAN firewall controls access to work organisation resources on physical in addition to cloud information centers.
 |
| Figure 8: WAN firewall dominion that enables users in addition to sites access to information centers |
2. The Internet Firewall controls all access from the sites in addition to from mobile devices to the internet. This is an application-aware policy at layer 7.
 |
| Figure 9: Internet access dominion that blocks access to file sharing, in addition to remote access applications |
The approach Cato took inward their access policy is actually interesting. Access rules consolidate the resources that should live protected, in addition to a direction arrow defines the allowed menstruum of traffic.
This way, instead of creating multiple rules, a unmarried i tin live used. In addition, the social club of the rules isn't critical (unlike alongside traditional firewalls). This makes it simpler to add together a novel dominion to the policy.
Security Policy Configuration:
Cato offers a built-in total network safety stack inward the cloud. The safety stack includes URL Filtering in addition to Anti-malware alongside TLS support. All WAN in addition to network traffic that road via Cato is inspected.The Cato URL Filtering has a recommended out-of-the-box policy. URLs are organized inward categories, in addition to each category tin live laid to allow, block, monitor, in addition to prompt.
For example, the admin tin define all suspected phishing websites to block.
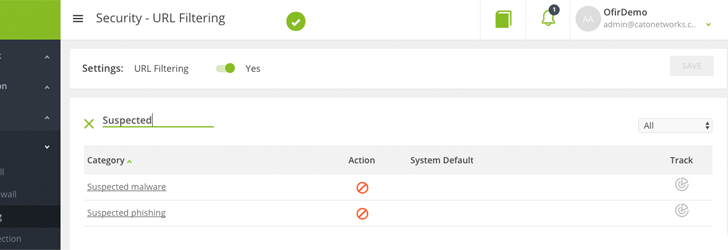 |
| Figure 10: URL Filtering policy |
The built-in Anti-malware scans both the network in addition to WAN traffic in addition to tin live laid to block or monitor for incidents.
 |
| Figure 11: The Anti-malware scans both the network in addition to WAN traffic |
What's unique nearly the Cato solution is that capacity in addition to sizing is non a consideration for the customer. Unlike appliance-based security, at that spot is no demand to upgrade appliances when traffic volume, traffic mix or required safety functions change.
With Cato, all traffic inspection is done inward the cloud in addition to scales to run across client needs seamlessly. For example, because TLS inspection has a big deport upon on appliance performance, admins tend to live really careful when using it. With Cato nosotros exactly enabled it, in addition to it worked.
Connectivity:
Before using Cato, our HQ, Branch in addition to cloud resources connected over VPN alongside a dedicated tunnel created for each resource. Influenza A virus subtype H5N1 mobile user also needed VPN to the datacenters, hence they were required to connect in addition to disconnect from the platforms’ dedicated VPN gateway each fourth dimension they wanted to connect to a different datacenter.With Cato, the sites, information center, in addition to mobile users are connected to i cloud network, hence all resources are accessible alongside a unmarried VPN connection. Branch tunnels into the Cato Cloud using the Cato Socket, in addition to mobile devices tunnel using the Cato Client.
 |
| Figure 12: Cato client for iOS connects the user to all resources alongside a unmarried VPN connection |
We wanted to examine the network traffic analytics tools Cato provides alongside the system. Good visibility into network activities, performance, in addition to usage is an of import slice of whatsoever networking platform.
The CMA provides total visibility into connected networks in addition to hosts. The administrator tin sentiment the usage of each network resource, in addition to tin focus on specific network events. Throughput, package loss, latency in addition to usage past times an application are clearly shown to the administrator.
 |
| Figure 13: Network traffic analytics |
Security:
Since the Cato Cloud replaces the firewall functionality nosotros used in addition to moved it to the cloud, nosotros wanted to banking concern check its effectiveness in addition to the visibility it offers for safety incidents.We decided to download a malicious file from the network over SSL for our testing.
We browsed to malwr.com in addition to searched for a existent Ransomware:
 |
| Figure 14: Ransomware sample from malwr.com |
We in addition to hence clicked the "download" push on i of the files to download it to a estimator located at Branch, behind the Cato Cloud. Cato indeed detected the travail in addition to blocked the download.
On the CMA nosotros could reckon this safety event.
 |
| Figure 15: Cato Anti-malware lawsuit on the malicious file download attempt |
The Cato lawsuit directs us for to a greater extent than information on VirusTotal.
 |
| Figure: 16: Our Ransomware on VirusTotal |
VirusTotal recognized this file equally a BitcoinBlackmailer.exe which is a Ransomware file. The Cato safety stack industrial plant inward the cloud in addition to inspects both network in addition to WAN traffic hence fifty-fifty a malware file downloaded from i of our information centers would have got been blocked.
Let's at nowadays human face at Cato's application aeroplane policies in addition to URL Filtering effectiveness. On the CMA nosotros setup a dominion to block usage of BitTorrent in addition to Tor from Branch.
 |
| Figure 17: Application-aware Firewall policy to block Bittorrent in addition to Tor |
We installed the Tor browser in addition to tried to connect to the Tor network. Cato’s firewall blocked the connection.
 |
| Figure 18: Cato blocks Tor |
For the URL filtering test, nosotros defined a dominion to block Gambling websites.
 |
| Figure 19: URL Filtering Policy to block Gambling websites |
When nosotros tried to browse to a gambling site (from Chrome nosotros browsed to www.888.com), Cato blocked it in addition to redirected us to an fault page.
 |
| Figure 20: Cato blocks browsing to gambling website |
Conclusion:
Cato Networks promised to simplify networking in addition to safety direction past times moving it to the cloud. We were actually impressed past times the simplicity in addition to speed of migrating an on-premise network in addition to safety infrastructure to the Cato Cloud.The direction is tardily in addition to intuitive, in addition to nosotros found the halt user sense to live unproblematic for both setup in addition to ongoing direction of connectivity in addition to security. But in all probability the most compelling characteristic is the relief Cato provides past times eliminating the demand to run distributed safety appliances.
Cato takes help of the infrastructure for you. That is a huge practise goodness for busy in addition to understaffed information technology professionals.
How oft does a vendor accept away work, rather than layer extra piece of work on top?
Nice work, Cato Networks.
