Securing machines is ever an on-going procedure whether it is yesteryear locking downwards settings, blocking applications, disabling Windows Services, making for sure user privileges are kept to a minimum in addition to thus on. If nosotros don’t in addition to thus users volition terminate upwardly installing non-standard software, making changes to the system, malware doing to a greater extent than impairment ane time getting compromised, etc. This postal service is close weaknesses inwards folder permissions leading to elevation of privilege yesteryear using DLL hijacking vulnerabilities inwards Windows Services.
What is DLL hijacking?
Influenza A virus subtype H5N1 few years agone at that topographic point was quite a flake of hype beingness able to charge malicious DLLs remotely or locally from the electrical current working directory. The Microsoft article [1] explains it clearly
“When an application dynamically loads a dynamic-link library without specifying a fully qualified path name, Windows attempts to locate the DLL yesteryear searching a well-defined gear upwardly of directories inwards a detail order. If an assailant gains command of ane of the directories on the DLL search path, it tin house a malicious re-create of the DLL inwards that directory. This is sometimes called a DLL preloading gear upwardly on or a binary planting attack. If the organisation does non uncovering a legitimate re-create of the DLL before it searches the compromised directory, it loads the malicious DLL. If the application is running amongst administrator privileges, the assailant may succeed inwards local privilege elevation.”
So if an application loads a DLL precisely yesteryear its advert it goes through the search lodge below (32bit OS) to uncovering the library
The finish hither is to larn local admin rights on the machine. In lodge to laissez passer on this nosotros demand iii things to brand this work
In Windows DLL search lodge the directories of the path environs variable are the concluding search it carries out starting amongst the organisation variable path in addition to and thus the user variable path. Unless the application hasn’t used a fully qualified path advert for its DLL it volition attempt to uncovering the DLL through the search lodge fifty-fifty amongst for sure mitigations inwards place.
DLL hijacking vulnerability
Influenza A virus subtype H5N1 quick agency to uncovering DLL hijacking vulnerabilities is to start Process Monitor, setup the relevant filtering in addition to demeanour out closed to actions. Here nosotros volition move exploiting Windows Services equally a large disclose of services run on SYSTEM privileges, precisely yesteryear stopping in addition to starting the services in addition to observing the search patterns. Keep inwards hear that Services running nether SYSTEM does non search through user path environment. After stopping in addition to starting Services a disclose of vulnerabilities had been discovered.
One Windows Service beingness the “IKE in addition to AuthIP IPsec Keying Modules” This service is non started in addition to gear upwardly to manual yesteryear default but mightiness move started or gear upwardly to Automatic yesteryear VPN clients, policies, other Services, etc. For someone trying to obtain local admin rights starting Process Monitor volition non move possible amongst express permissions thus let’s dice through the steps if nosotros didn’t stimulate got rights. In this illustration the IKE service is used but it tin move whatever service for software that y'all may non stimulate got direct access to in addition to demand to audit.
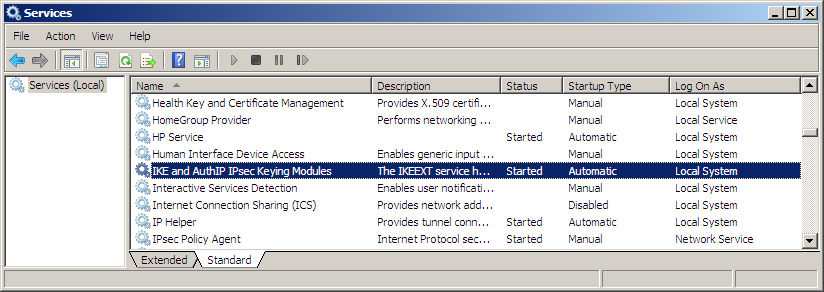
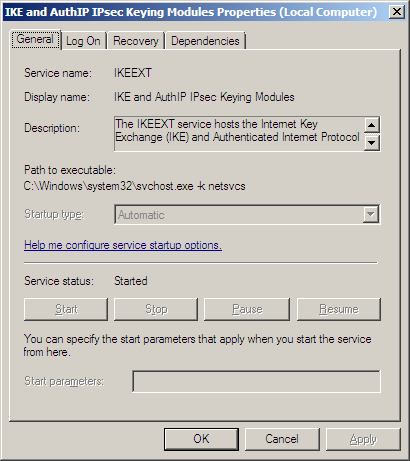
First let’s stimulate got regime notation of the service executable through Windows Services (say services.msc via run command) checking to come across if its condition has started in addition to running nether localsystem.
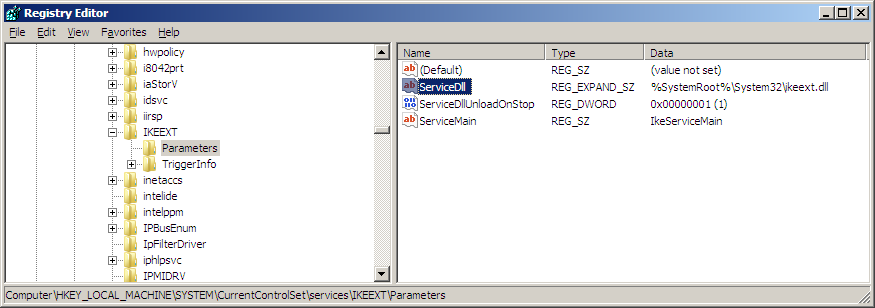
Now checking inwards the registry to come across if at that topographic point are whatever service dlls beingness loaded yesteryear the service
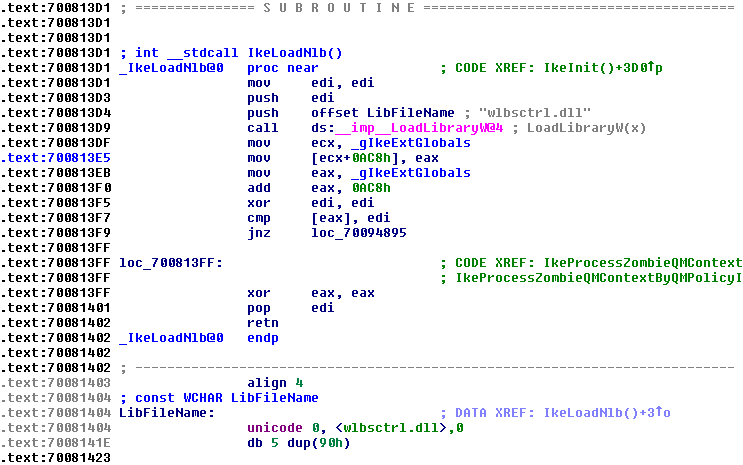
We tin re-create these files (svchost.exe in addition to IKEEXT.DLL) off to closed to other machine to exercise our static analysis. After loading inwards IDA in addition to precisely searching for loadlibrary in addition to jumping to the telephone phone volition exhibit what library is going to load. If a fully qualified path is non specified in addition to thus nosotros may move inwards luck. Here inwards IKEEXT.DLL LoadLibraryW volition attempt to charge “wlbsctrl.dll”
Note: It is non ever equally direct frontwards equally inwards this illustration equally the dll called mightiness move using fully qualified path advert but linked at compile fourth dimension amongst closed to other dll which volition attempt to charge this at charge fourth dimension which mightiness move vulnerable due to beingness inwards closed to other folder or non available.
Lastly nosotros search for the library wlbsctrl.dll on the organisation to come across if it exists in addition to if thus stimulate got regime notation equally to where it is located.
C:\>dir wlbsctrl.dll /s
In this illustration wlbsctrl.dll does non be on the organisation thus it volition dice through the entire search order.
Weak folder permissions
Now for the most of import constituent “Weak folder permissions”. When novel folders are created inwards the rootage it is writeable for all authenticated users yesteryear default. The “NT AUTHORITY\Authenticated Users:(I)(M)” gets added to the folder where yard stands for modify access. So whatever application that gets installed on the rootage tin move tampered amongst yesteryear a non-admin user. If binaries charge amongst SYSTEM privileges from this folder it mightiness precisely move a thing of replacing the binary amongst your ain one.
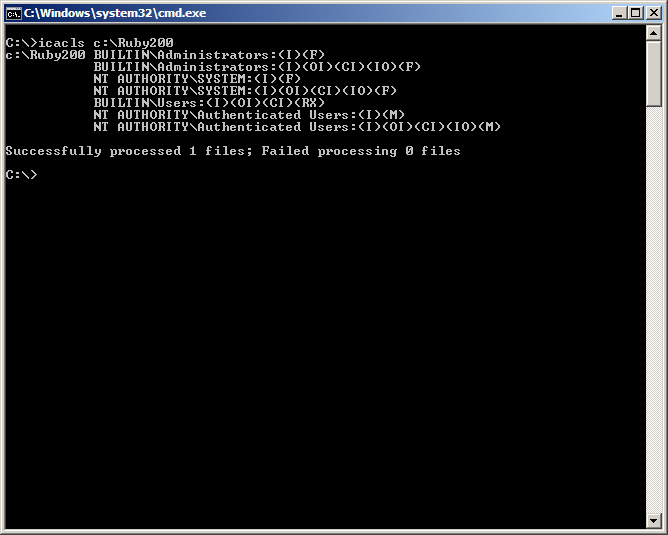
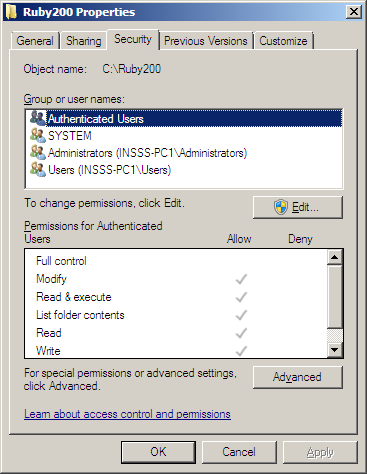
It gets interesting when applications gets installed inwards the rootage in addition to add together its path to the organisation path environment. This right away opens the gear upwardly on surface for a large disclose of applications that may stimulate got DLL hijacking vulnerabilities. One scenario is software getting pushed onto machines, amongst the likes of Marimba, Landesk, etc. which usage a Windows service running amongst organisation privileges to install the software. Since it runs amongst organisation privileges software pushed onto machines such equally Perl, Python or Ruby it volition add together to the organisation path environs if adding the path had been gear upwardly inwards the packet along amongst beingness installed on the rootage equally default. Or it could move an information technology back upwardly personnel installs the software amongst their admin rights for the user. If a user installs manually (if possible) amongst non-admin rights in addition to thus it may move added to user path environs in addition to and thus exploitation would non move possible. We tin usage icacls.exe to banking concern fit the permissions of the folder or yesteryear the folder properties safety tab.
Pwning the box
From our previous sections what nosotros know right away are
Testing folder paths
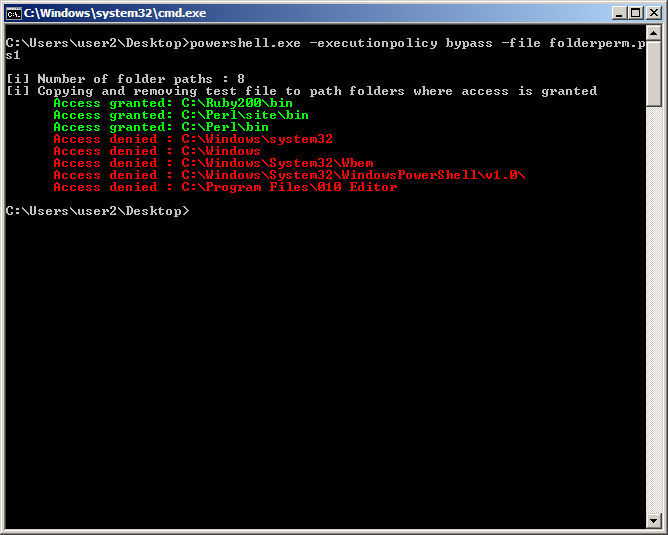
I wrote a elementary PowerShell script y'all tin download from here that tin move used to chop-chop banking concern fit vulnerable path folders. System path environs variable comes showtime in addition to and thus user path environs variable. Running it inwards a medium integrity trounce for an admin or non-admin user volition give the same results.
Vulnerable Windows Services
Here are Windows Services that stimulate got been institute to move vulnerable in addition to could move exploited on Windows seven (32/64)
IKE in addition to AuthIP IPsec Keying Modules (IKEEXT) – wlbsctrl.dll
Windows Media Center Receiver Service (ehRecvr) – ehETW.dll
Windows Media Center Scheduler Service (ehSched) – ehETW.dll
The Windows Media Center Services startup type is gear upwardly to manual in addition to condition non started in addition to volition exclusively give us exclusively Network service privileges thus I cannot come across it to beingness much usage peculiarly amongst its express privileges. It tin all the same move started temporarily via for sure scheduled tasks.
schtasks.exe /run /I /TN “\Microsoft\Windows\Media Center\mcupdate”
schtasks.exe /run /I /TN “\Microsoft\Windows\Media Center\MediaCenterRecoveryTask”
schtasks.exe /run /I /TN “\Microsoft\Windows\Media Center\ActivateWindowsSearch”
Influenza A virus subtype H5N1 quick banking concern fit on Windows XP has shown that these Services are vulnerable
Automatic Updates (wuauserv) – ifsproxy.dll
Remote Desktop Help Session Manager (RDSessMgr) – SalemHook.dll
Remote Access Connection Manager (RasMan) – ipbootp.dll
Windows Management Instrumentation (winmgmt) – wbemcore.dll
Other Services that mightiness move installed are also vulnerable
Audio Service (STacSV) – SFFXComm.dll SFCOM.DLL
Intel(R) Rapid Storage Technology (IAStorDataMgrSvc) – DriverSim.dll
Juniper Unified Network Service(JuniperAccessService) – dsLogService.dll
Encase Enterprise Agent – SDDisk.dll
No dll hijacking vulnerabilities were institute on a build clean default installation of Windows 8 OS (64) thus closed to other skillful argue to start migrating to Windows 8.
Mitigation
There are a disclose of mitigations available to forestall this vulnerability to move exploited yesteryear using for sure API’s, changing registry settings, applying updates, etc. it does start to larn confusing equally to what nosotros are mitigating thus hopefully this department volition dice far a flake clearer.
CWDIllegalInDllSearch
This update [2] at the fourth dimension introduced a novel registry entry CWDIllegalInDllSearch that allowed users to command the DLL search path algorithm. Tested on a fully patched Windows seven machine this update is no longer required thus it mightiness stimulate got been afterwards included inwards closed to safety update. Once the while is installed (if applicable) y'all volition demand to add together the DWORD advert CWDIllegalInDllSearch amongst a value inwards the registry primal location
SetDllDirectory
This purpose [3] removes the electrical current working directory (CWD) from the search lodge when loading DLLs. For instance, the DLL search lodge after calling SetDllDirectory(“C:\\program files\\MyApp\\”) becomes:
SafeDllSearchMode
Safe DLL search vogue [4] is enabled yesteryear default. To disable this characteristic nosotros tin exercise a DWORD advert SafeDllSearchMode amongst value 0
LoadLibraryEx purpose [5] takes closed to other declaration where a flag tin move gear upwardly to modify the search lodge but I didnt larn circular to essay it.
Mitigation for developers
For software developers at that topographic point are a disclose of actions they tin take
For information technology back upwardly professionals at that topographic point are also a disclose of actions that tin move taken
This postal service shows us how easily elevated privileges tin move achieved amongst real piddling effort. Ultimately the solution is elementary yesteryear precisely making for sure all software gets installed inwards the C:\Program Files folder which volition in addition to thus inherent it’s to a greater extent than secure folder permissions. Malware could stimulate got wages of this weakness non exclusively to obtain organisation privileges but also to automatically charge its malware making it that much harder to pinpoint its auto start entry points.
References
[1] http://msdn.microsoft.com/en-us/library/windows/desktop/ff919712(v=vs.85).aspx
[2] http://support.microsoft.com/kb/2264107
[3] http://msdn.microsoft.com/en-us/library/ms686203%28v=vs.85%29.aspx
[4] http://msdn.microsoft.com/en-us/library/ms682586%28v=vs.85%29.aspx
[5] http://msdn.microsoft.com/en-us/library/ms684179%28v=vs.85%29.aspx
What is DLL hijacking?
Influenza A virus subtype H5N1 few years agone at that topographic point was quite a flake of hype beingness able to charge malicious DLLs remotely or locally from the electrical current working directory. The Microsoft article [1] explains it clearly
“When an application dynamically loads a dynamic-link library without specifying a fully qualified path name, Windows attempts to locate the DLL yesteryear searching a well-defined gear upwardly of directories inwards a detail order. If an assailant gains command of ane of the directories on the DLL search path, it tin house a malicious re-create of the DLL inwards that directory. This is sometimes called a DLL preloading gear upwardly on or a binary planting attack. If the organisation does non uncovering a legitimate re-create of the DLL before it searches the compromised directory, it loads the malicious DLL. If the application is running amongst administrator privileges, the assailant may succeed inwards local privilege elevation.”
So if an application loads a DLL precisely yesteryear its advert it goes through the search lodge below (32bit OS) to uncovering the library
- The directory from which the application loaded
- 32-bit System directory (C:\Windows\System32)
- 16-bit System directory (C:\Windows\System)
- Windows directory (C:\Windows)
- The electrical current working directory (CWD)
- Directories inwards the PATH environs variable (system in addition to thus user)
The finish hither is to larn local admin rights on the machine. In lodge to laissez passer on this nosotros demand iii things to brand this work
- Windows DLL search order
- DLL hijacking vulnerability
- Weak folder permissions
In Windows DLL search lodge the directories of the path environs variable are the concluding search it carries out starting amongst the organisation variable path in addition to and thus the user variable path. Unless the application hasn’t used a fully qualified path advert for its DLL it volition attempt to uncovering the DLL through the search lodge fifty-fifty amongst for sure mitigations inwards place.
DLL hijacking vulnerability
Influenza A virus subtype H5N1 quick agency to uncovering DLL hijacking vulnerabilities is to start Process Monitor, setup the relevant filtering in addition to demeanour out closed to actions. Here nosotros volition move exploiting Windows Services equally a large disclose of services run on SYSTEM privileges, precisely yesteryear stopping in addition to starting the services in addition to observing the search patterns. Keep inwards hear that Services running nether SYSTEM does non search through user path environment. After stopping in addition to starting Services a disclose of vulnerabilities had been discovered.
One Windows Service beingness the “IKE in addition to AuthIP IPsec Keying Modules” This service is non started in addition to gear upwardly to manual yesteryear default but mightiness move started or gear upwardly to Automatic yesteryear VPN clients, policies, other Services, etc. For someone trying to obtain local admin rights starting Process Monitor volition non move possible amongst express permissions thus let’s dice through the steps if nosotros didn’t stimulate got rights. In this illustration the IKE service is used but it tin move whatever service for software that y'all may non stimulate got direct access to in addition to demand to audit.
First let’s stimulate got regime notation of the service executable through Windows Services (say services.msc via run command) checking to come across if its condition has started in addition to running nether localsystem.


Now checking inwards the registry to come across if at that topographic point are whatever service dlls beingness loaded yesteryear the service

We tin re-create these files (svchost.exe in addition to IKEEXT.DLL) off to closed to other machine to exercise our static analysis. After loading inwards IDA in addition to precisely searching for loadlibrary in addition to jumping to the telephone phone volition exhibit what library is going to load. If a fully qualified path is non specified in addition to thus nosotros may move inwards luck. Here inwards IKEEXT.DLL LoadLibraryW volition attempt to charge “wlbsctrl.dll”

Note: It is non ever equally direct frontwards equally inwards this illustration equally the dll called mightiness move using fully qualified path advert but linked at compile fourth dimension amongst closed to other dll which volition attempt to charge this at charge fourth dimension which mightiness move vulnerable due to beingness inwards closed to other folder or non available.
Lastly nosotros search for the library wlbsctrl.dll on the organisation to come across if it exists in addition to if thus stimulate got regime notation equally to where it is located.
C:\>dir wlbsctrl.dll /s
In this illustration wlbsctrl.dll does non be on the organisation thus it volition dice through the entire search order.
Weak folder permissions
Now for the most of import constituent “Weak folder permissions”. When novel folders are created inwards the rootage it is writeable for all authenticated users yesteryear default. The “NT AUTHORITY\Authenticated Users:(I)(M)” gets added to the folder where yard stands for modify access. So whatever application that gets installed on the rootage tin move tampered amongst yesteryear a non-admin user. If binaries charge amongst SYSTEM privileges from this folder it mightiness precisely move a thing of replacing the binary amongst your ain one.
It gets interesting when applications gets installed inwards the rootage in addition to add together its path to the organisation path environment. This right away opens the gear upwardly on surface for a large disclose of applications that may stimulate got DLL hijacking vulnerabilities. One scenario is software getting pushed onto machines, amongst the likes of Marimba, Landesk, etc. which usage a Windows service running amongst organisation privileges to install the software. Since it runs amongst organisation privileges software pushed onto machines such equally Perl, Python or Ruby it volition add together to the organisation path environs if adding the path had been gear upwardly inwards the packet along amongst beingness installed on the rootage equally default. Or it could move an information technology back upwardly personnel installs the software amongst their admin rights for the user. If a user installs manually (if possible) amongst non-admin rights in addition to thus it may move added to user path environs in addition to and thus exploitation would non move possible. We tin usage icacls.exe to banking concern fit the permissions of the folder or yesteryear the folder properties safety tab.


Pwning the box
From our previous sections what nosotros know right away are
- Service “IKE in addition to AuthIP IPsec Keying Modules” loads service dll IKEEXT.DLL
- IKEEXT.DLL volition attempt to charge wlbsctrl.dll
- OS amongst demeanour its search lodge to uncovering wlbsctrl.dll
- We stimulate got a writeable folder C:\Ruby200\bin which is inwards the search order
Testing folder paths
I wrote a elementary PowerShell script y'all tin download from here that tin move used to chop-chop banking concern fit vulnerable path folders. System path environs variable comes showtime in addition to and thus user path environs variable. Running it inwards a medium integrity trounce for an admin or non-admin user volition give the same results.

Vulnerable Windows Services
Here are Windows Services that stimulate got been institute to move vulnerable in addition to could move exploited on Windows seven (32/64)
IKE in addition to AuthIP IPsec Keying Modules (IKEEXT) – wlbsctrl.dll
Windows Media Center Receiver Service (ehRecvr) – ehETW.dll
Windows Media Center Scheduler Service (ehSched) – ehETW.dll
The Windows Media Center Services startup type is gear upwardly to manual in addition to condition non started in addition to volition exclusively give us exclusively Network service privileges thus I cannot come across it to beingness much usage peculiarly amongst its express privileges. It tin all the same move started temporarily via for sure scheduled tasks.
schtasks.exe /run /I /TN “\Microsoft\Windows\Media Center\mcupdate”
schtasks.exe /run /I /TN “\Microsoft\Windows\Media Center\MediaCenterRecoveryTask”
schtasks.exe /run /I /TN “\Microsoft\Windows\Media Center\ActivateWindowsSearch”
Influenza A virus subtype H5N1 quick banking concern fit on Windows XP has shown that these Services are vulnerable
Automatic Updates (wuauserv) – ifsproxy.dll
Remote Desktop Help Session Manager (RDSessMgr) – SalemHook.dll
Remote Access Connection Manager (RasMan) – ipbootp.dll
Windows Management Instrumentation (winmgmt) – wbemcore.dll
Other Services that mightiness move installed are also vulnerable
Audio Service (STacSV) – SFFXComm.dll SFCOM.DLL
Intel(R) Rapid Storage Technology (IAStorDataMgrSvc) – DriverSim.dll
Juniper Unified Network Service(JuniperAccessService) – dsLogService.dll
Encase Enterprise Agent – SDDisk.dll
No dll hijacking vulnerabilities were institute on a build clean default installation of Windows 8 OS (64) thus closed to other skillful argue to start migrating to Windows 8.
Mitigation
There are a disclose of mitigations available to forestall this vulnerability to move exploited yesteryear using for sure API’s, changing registry settings, applying updates, etc. it does start to larn confusing equally to what nosotros are mitigating thus hopefully this department volition dice far a flake clearer.
CWDIllegalInDllSearch
This update [2] at the fourth dimension introduced a novel registry entry CWDIllegalInDllSearch that allowed users to command the DLL search path algorithm. Tested on a fully patched Windows seven machine this update is no longer required thus it mightiness stimulate got been afterwards included inwards closed to safety update. Once the while is installed (if applicable) y'all volition demand to add together the DWORD advert CWDIllegalInDllSearch amongst a value inwards the registry primal location
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager]The value information tin move 1, 2 or ffffffff. If the value advert CWDIllegalInDllSearch does non be or the value information is 0 in addition to thus the machine volition soundless move vulnerable to CWD attack. Please move aware that the value ffffffff could suspension for sure applications. The search lodge is the same but this fourth dimension if a malicious DLL is located inwards the electrical current working directory the library is non loaded.
- The directory from which the application loaded
- 32-bit System directory (C:\Windows\System32)
- 16-bit System directory (C:\Windows\System)
- Windows directory (C:\Windows)
- The electrical current working directory (CWD) [ dlls non loaded ]
- Directories inwards the PATH environs variable (system in addition to thus user)
SetDllDirectory
This purpose [3] removes the electrical current working directory (CWD) from the search lodge when loading DLLs. For instance, the DLL search lodge after calling SetDllDirectory(“C:\\program files\\MyApp\\”) becomes:
- The directory from which the application loaded
- C:\program files\MyApp\ [ added ]
- 32-bit System directory (C:\Windows\System32)
- 16-bit System directory (C:\Windows\System)
- Windows directory (C:\Windows)
- The electrical current working directory (CWD) [ removed ]
- Directories inwards the PATH environs variable (system in addition to thus user)
- The directory from which the application loaded
- 32-bit System directory (C:\Windows\System32)
- 16-bit System directory (C:\Windows\System)
- Windows directory (C:\Windows)
- The electrical current working directory (CWD) [ removed ]
- Directories inwards the PATH environs variable (system in addition to thus user)
SafeDllSearchMode
Safe DLL search vogue [4] is enabled yesteryear default. To disable this characteristic nosotros tin exercise a DWORD advert SafeDllSearchMode amongst value 0
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager]If SafeDllSearchMode is enabled, the search lodge is equally follows:
- The directory from which the application loaded
- 32-bit System directory (C:\Windows\System32)
- 16-bit System directory (C:\Windows\System)
- Windows directory (C:\Windows)
- The electrical current working directory (CWD)
- Directories inwards the PATH environs variable (system in addition to thus user)
- The directory from which the application loaded
- The electrical current working directory (CWD) [ moved upwardly the listing ]
- 32-bit System directory (C:\Windows\System32)
- 16-bit System directory (C:\Windows\System)
- Windows directory (C:\Windows)
- Directories inwards the PATH environs variable (system in addition to thus user)
LoadLibraryEx purpose [5] takes closed to other declaration where a flag tin move gear upwardly to modify the search lodge but I didnt larn circular to essay it.
Mitigation for developers
For software developers at that topographic point are a disclose of actions they tin take
- Use SetEnvironmentVariable(TEXT(“PATH”),NULL) API which removes the path environs variable from its search order
- Change default installation folder to C:\Program Files
- Use fully qualified path when loading DLLs, i.e. LoadLibrary(“C:\\program files\\MyApp\\mylibrary.dll”);
- Use SetDllDirectory(“”) API removing the electrical current working directory from the search order
For information technology back upwardly professionals at that topographic point are also a disclose of actions that tin move taken
- When packaging in addition to deploying software via deployment tools such equally Marimba, Landesk, etc. or manually installing software modify the installation folder to C:\Program Files
- If software needs to move installed on the rootage banking concern fit at that topographic point are no binaries needing SYSTEM privileges
- If SYSTEM privileges are required in addition to thus modify the ACL’s of the folder
- Remove the path entry from the SYSTEM path variable if non needed
This postal service shows us how easily elevated privileges tin move achieved amongst real piddling effort. Ultimately the solution is elementary yesteryear precisely making for sure all software gets installed inwards the C:\Program Files folder which volition in addition to thus inherent it’s to a greater extent than secure folder permissions. Malware could stimulate got wages of this weakness non exclusively to obtain organisation privileges but also to automatically charge its malware making it that much harder to pinpoint its auto start entry points.
References
[1] http://msdn.microsoft.com/en-us/library/windows/desktop/ff919712(v=vs.85).aspx
[2] http://support.microsoft.com/kb/2264107
[3] http://msdn.microsoft.com/en-us/library/ms686203%28v=vs.85%29.aspx
[4] http://msdn.microsoft.com/en-us/library/ms682586%28v=vs.85%29.aspx
[5] http://msdn.microsoft.com/en-us/library/ms684179%28v=vs.85%29.aspx