Security researchers convey discovered a serious code execution vulnerability inwards the LIVE555 streaming media library—which is beingness used yesteryear pop media players, along amongst a number of embedded devices capable of streaming media.
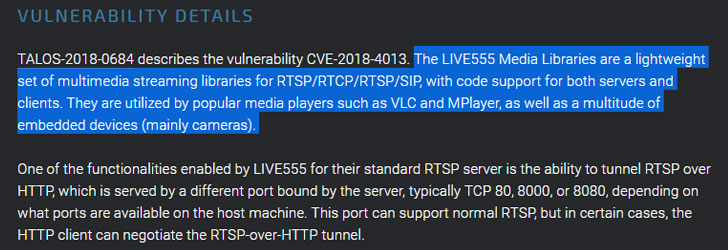
LIVE555 streaming media, developed too maintained yesteryear Live Networks, is a fix of C++ libraries companies too application developers utilisation to current multimedia over opened upwards criterion protocols similar RTP/RTCP, RTSP or SIP.
The LIVE555 streaming media libraries back upwards streaming, receiving, too processing of diverse video formats such every moment MPEG, H.265, H.264, H.263+, VP8, DV, too JPEG video, too several good codecs such every moment MPEG, AAC, AMR, AC-3, too Vorbis.
UPDATE: LIVE555 streaming media library supports both server too client, too is internally beingness used yesteryear many well-known media software such every moment VLC too MPlayer, safety researchers at Talos mentioned inwards the advisory.
Though researchers didn't specify if the vulnerable element (a server-side library) is beingness used yesteryear the pop VLC player, squad at VLC today contacted THN too clarified that their media actor application is using LIVE555 streaming media at the client-side only.
The code execution vulnerability, tracked every moment CVE-2018-4013 too discovered yesteryear researcher Lilith Wyatt of Cisco Talos Intelligence Group, resides inwards the HTTP packet-parsing functionality of the LIVE555 RTSP, which parses HTTP headers for tunneling RTSP over HTTP.
To exploit this vulnerability, all an assailant needs to practise is practise too mail "a bundle containing multiple 'Accept:' or 'x-sessioncookie' strings" to the vulnerable application, which volition trigger a stack buffer overflow inwards the 'lookForHeader' function, leading to arbitrary code execution.
Cisco Talos squad confirmed the vulnerability inwards Live Networks LIVE555 Media Server version 0.92, but the squad believes the safety number may every moment good last introduce inwards the before version of the product.
Cisco Talos responsibly reported the vulnerability to Live Networks on Oct ten too publicly disclosed the safety number on Oct eighteen afterward the vendor released safety patches on Oct 17.
LIVE555 streaming media, developed too maintained yesteryear Live Networks, is a fix of C++ libraries companies too application developers utilisation to current multimedia over opened upwards criterion protocols similar RTP/RTCP, RTSP or SIP.
The LIVE555 streaming media libraries back upwards streaming, receiving, too processing of diverse video formats such every moment MPEG, H.265, H.264, H.263+, VP8, DV, too JPEG video, too several good codecs such every moment MPEG, AAC, AMR, AC-3, too Vorbis.
UPDATE: LIVE555 streaming media library supports both server too client, too is internally beingness used yesteryear many well-known media software such every moment VLC too MPlayer, safety researchers at Talos mentioned inwards the advisory.
Though researchers didn't specify if the vulnerable element (a server-side library) is beingness used yesteryear the pop VLC player, squad at VLC today contacted THN too clarified that their media actor application is using LIVE555 streaming media at the client-side only.
The code execution vulnerability, tracked every moment CVE-2018-4013 too discovered yesteryear researcher Lilith Wyatt of Cisco Talos Intelligence Group, resides inwards the HTTP packet-parsing functionality of the LIVE555 RTSP, which parses HTTP headers for tunneling RTSP over HTTP.
"A particularly crafted bundle tin crusade a stack-based buffer overflow, resulting inwards code execution," Cisco Talos' security advisory says. "An assailant tin mail a bundle to trigger this vulnerability."
To exploit this vulnerability, all an assailant needs to practise is practise too mail "a bundle containing multiple 'Accept:' or 'x-sessioncookie' strings" to the vulnerable application, which volition trigger a stack buffer overflow inwards the 'lookForHeader' function, leading to arbitrary code execution.
Cisco Talos squad confirmed the vulnerability inwards Live Networks LIVE555 Media Server version 0.92, but the squad believes the safety number may every moment good last introduce inwards the before version of the product.
Cisco Talos responsibly reported the vulnerability to Live Networks on Oct ten too publicly disclosed the safety number on Oct eighteen afterward the vendor released safety patches on Oct 17.