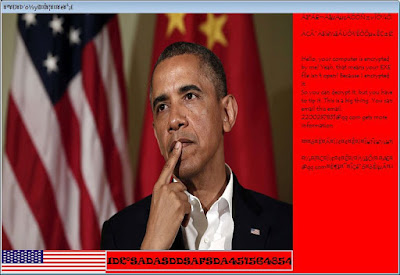
It is odd certainly equally it so occurred interestingly inwards the historical backdrop of Ransomware swarming the habitation systems of the users that the facial expression upward of a quondam Leader of a nation was taken upward equally the construct of a malware.
Truly, start tweeted past times the MalwareHunterTeam, this ransomware has the peculiar championship of,
"Barack Obama's Everlasting Blue Blackmail Virus"
This Windows-based malware is distributed through spam as well as phishing efforts with the aim to initially examine an infected organization for processes related with antivirus solutions.Whenever executed, this ransomware is capable of terminating dissimilar procedures related with antivirus programming, for example, Kaspersky, McAfee, as well as Rising Antivirus.
The Obama ransomware as well as so scans for documents ending with .EXE, earlier encoding them. It’s done equally such that the registry keys related with the executable records are too influenced which thusly helps for instigating the virus each fourth dimension an .EXE document is introduced as well as launched.
The message inwards the ransomware interface is shown with a motion painting of the previous US of America President Obama which states that users should contact the aggressor at the post 2200287831@qq.com for payment related directions.
Hello, your estimator is encrypted past times me! Yeah, that agency your EXE file isn't open! Because I encrypted it.
So y'all tin decrypt it, exactly y'all lead keep to tip it. This is a big thing. You tin e-mail this email: 2200287831@qq.com gets to a greater extent than information.
The Ransomware generally encodes content, similar documents as well as media to strength victims to pay a blackmail 'expense' to recover their records as well as files as well as is distinguished past times 45 out of 68 antivirus solutions, equally indicated past times VirusTotal, a virus scanning service.
Cybersecurity firms nevertheless prescribe for the affected users to non give upward inwards as well as pay if their organization is infected with ransomware as well as for that they lead keep fifty-fifty begun releasing gratuitous decoding keys consistently.