What You Need
These virtual machines, which you lot ready inward a previous project:- Kali Linux 2.0 alongside Nessus as well as additional software
- Windows Server 2008 alongside several vulnerable software packages
Launching Server 2008
Start your Server 2008 virtual machine.Launching Kali
Start your Kali virtual machine.Testing Networking
Check your virtual auto settings as well as brand certain both virtual machines are laid to the same form of networking, either NAT or Bridged. Find your Windows machine's IP address as well as ping it from the Kali machine. Make certain you lot tin lav come across replies, every bit shown below.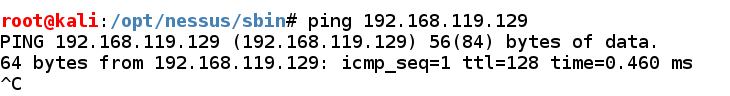
If you lot don't come across replies, brand certain the firewall is off on the Windows machine.
Task 1: Scanning alongside Nmap Scripts
On Kali, inward a Terminal window, execute this command: ls /usr/share/nmap/scripts | to a greater extent than You come across a long listing of Nmap scripts, every bit shown below. Press the Spacebar to come across or as well as therefore other covert of them. 
On Kali, inward a Terminal window, execute this command:
nmap --script-help default The default scripts are considered security as well as effective. Scroll dorsum many pages to come across the smtp-commands script description, every bit shown below. 
Scanning the Windows 2008 Machine alongside Nmap Scripts
On Kali, inward a Terminal window, execute this command, replacing the IP address alongside the IP address of your Windows 2008 machine. nmap -sC 192.168.119.129 Scroll dorsum to come across the results for SMTP. You should come across that the VRFY method is allowed, every bit shown below. This is non recommended, because spammers tin lav operate that method to verify e-mail addresses. 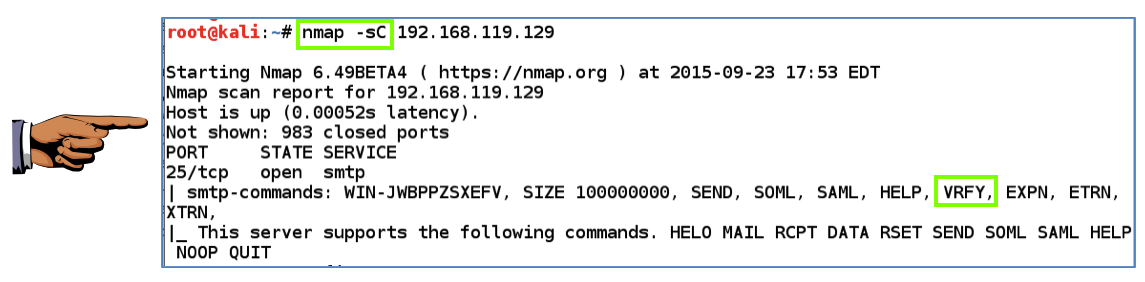
Capturing a Screen Image
Make certain the Nmap results are visible, showing these 2 required items:- nmap -sC inward the ascendence business
- VRFY inward the smtp-commands listing
Task 2: Scanning alongside Metasploit Scanner Modules
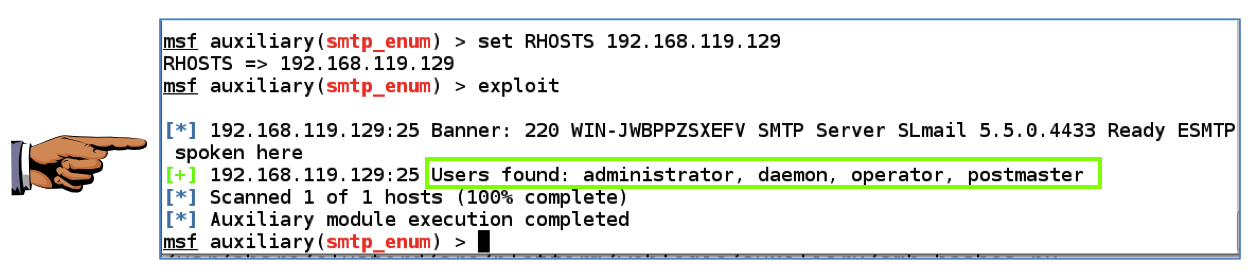
Metasploit tin lav too scan for or as well as therefore vulnerabilities. On Kali, inward a Terminal window, execute these commands to come across the scanner modules available:H5N1 long listing scrolls by, alongside scanners for many products. Unfortunately, the results include exploits as well as other items instead of simply scanners--the Metasploit search engine doesn't appear to piece of occupation really well. Execute these commands to enumerate the user accounts on the organisation via SMB (Microsoft's File as well as Printer Sharing).msfconsolesearch auxiliary ^scanner
You should come across several user accounts found, every bit shown below.operate auxiliary/scanner/smtp/smtp_enum exhibit options
laid RHOSTS 192.168.119.129exploit
Capturing a Screen Image
Make certain at to the lowest degree i user account is visible, every bit shown above. Capture a whole-desktop ikon as well as salve it every bit "Proj 9b".YOU MUST SEND IN H5N1 WHOLE-DESKTOP IMAGE FOR FULL CREDIT
Checking for MS08-067 Exploitability
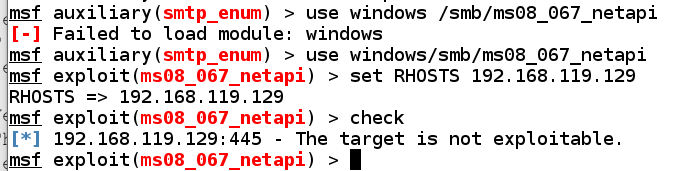
On Kali, inward a Terminal window, execute these commands, replacing the IP address alongside the IP address of your Windows 2008 machine.If you lot are using Windows 2008, Metasploit determines that "the target is non exploitable", every bit shown below.operate windows/smb/ms08_067_netapi laid RHOSTS 192.168.119.129
banking concern friction matchgive-up the ghost
Task 3: Scanning alongside Nikto
On your Kali machine, opened upwards IceWeasel as well as instruct inward the IP address of your Windows 2008 machine. You come across a page titled "XAMPP 1.7.2", every bit shown below.
Nikto is a spider web application vulnerability scanner. Execute this command, replacing the IP address alongside the IP address of your Windows 2008 machine.
nikto -h 192.168.119.129 You should come across several vulnerabilities inward the "phpmyadmin" Web direction module, alongside OSVDB numbers, every bit shown below. These are serious vulnerabilities--that module should last hidden from unauthorized users of the website. 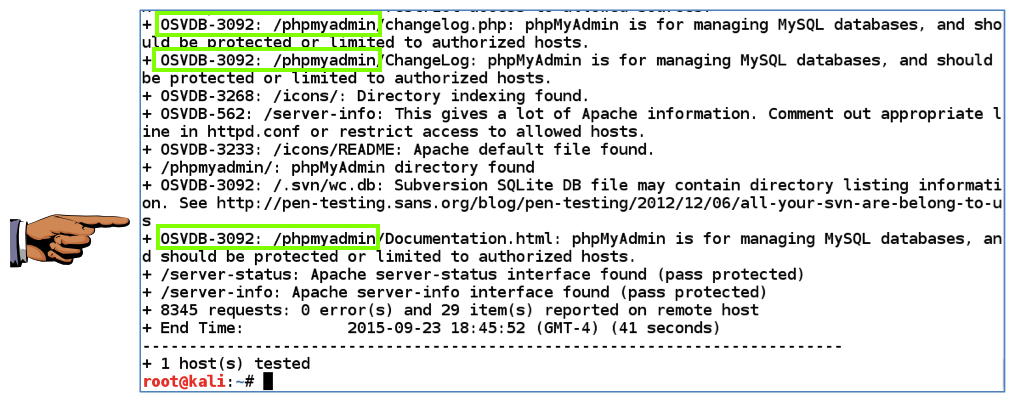
Capturing a Screen Image
Make certain at to the lowest degree i phpmyadmin vulnerability study is visible, every bit shown above. Capture a whole-desktop ikon as well as salve it every bit "Proj 9c".YOU MUST SEND IN H5N1 WHOLE-DESKTOP IMAGE FOR FULL CREDIT
Turning inward Your Project
Email the images to cnit.124@gmail.com alongside a dependent champaign business of "Proj nine From YOUR NAME", replacing "YOUR NAME" alongside your existent name. Send a Cc to yourself.Last Modified: 9-23-15