What You Need
These virtual machines, which yous railroad train inwards a previous project:- Kali Linux 2.0 alongside Nessus too additional software
- Windows Server 2008 alongside several vulnerable software packages
Launching Kali too Nessus
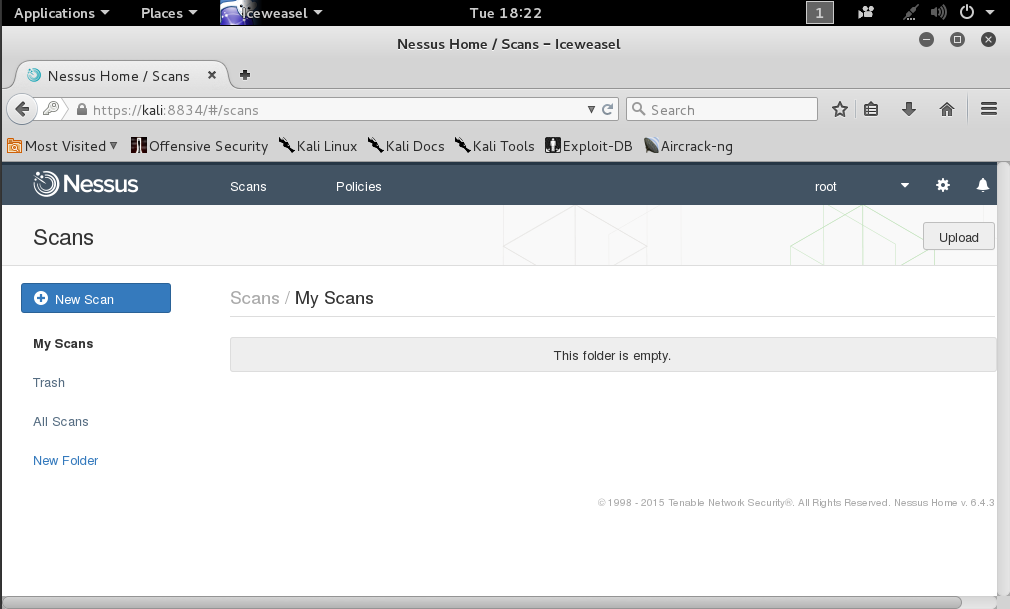
Start your Kali virtual machine. In a Terminal window, execute this command: service nessusd kickoff Open IceWeasel. Go to this URL: https://kali:8834 In IceWeasel, log inwards alongside the username too password yous chose during installation. You should come across the "Scans" page, every bit shown below.
Troubleshooting
If yous forgot your password, yous tin reset it alongside this command:/opt/nessus/sbin/nessuscli chpasswd rootage
Starting your Windows 2008 Machine alongside Vulnerable Software
Start your Windows Server 2008 VM. The default username is AdministratorThe default password is P@ssw0rd
Testing Networking
Check your virtual motorcar settings too brand certain both virtual machines are laid to the same form of networking, either NAT or Bridged. Find your Windows machine's IP address too ping it from the Kali machine. Make certain yous tin come across replies, every bit shown below.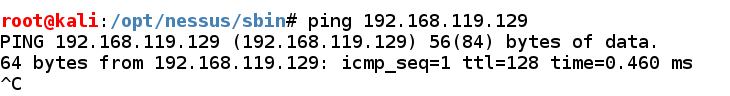
If yous don't come across replies, brand certain the firewall is off on the Windows machine.
Scanning the Windows 2008 Machine
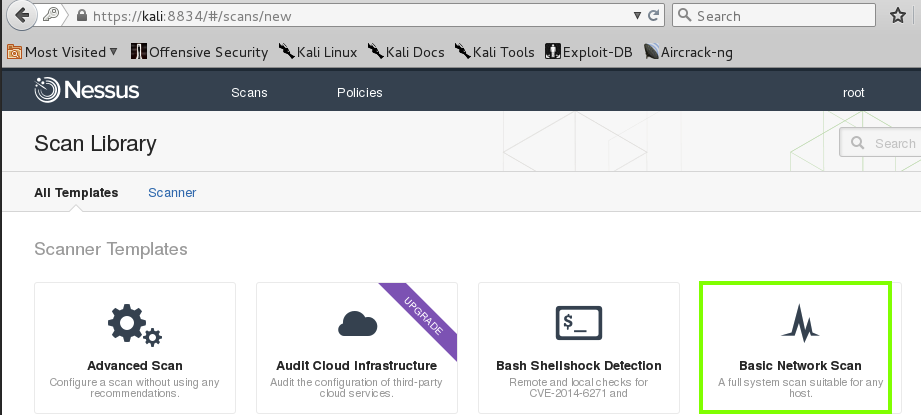
On Kali, inwards IceWeasel, at the pump peak of the Nessus page, click Scans. On the left side, click the "New Scan" button.On the adjacent page, click "Basic Network Scan", every bit shown below.
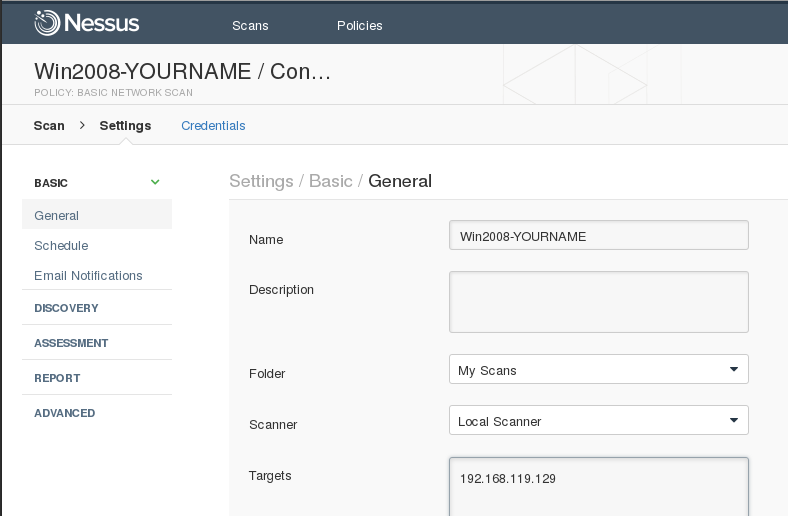
Fill inwards these values, every bit shown below.
- Name: Win2008 -YOURNAME, replacing "YOUR NAME" alongside your ain advert
- Description: leave blank
- Folder: "My Scans"
- Scanner: "Local Scans"
- Targets: 192.168.119.129 -- supervene upon this alongside the IP address of your Windows 2008 machine
At the bottom of the page, click the Save button.
Influenza A virus subtype H5N1 box pops upward bespeak whether to recall your password. Close it.
The "Scans" page shows your scan running, alongside a lilliputian light-green icon turning, every bit shown below.
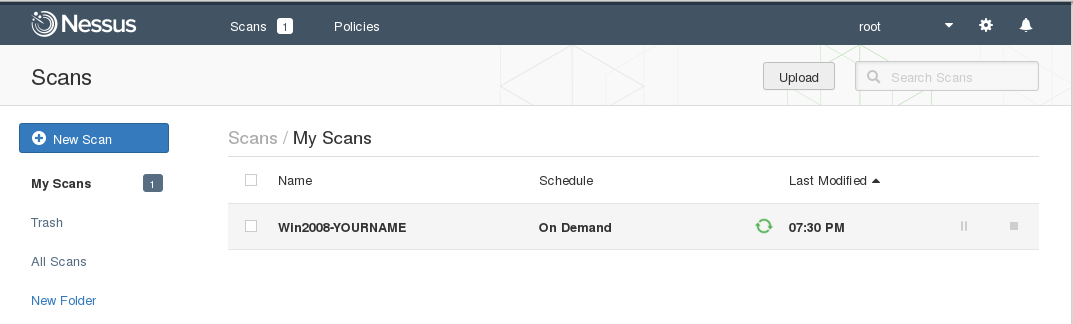
The scan should accept 5-6 minutes. When it completes, the light-green rotating icon changes to a light-green checkmark. every bit shown below.
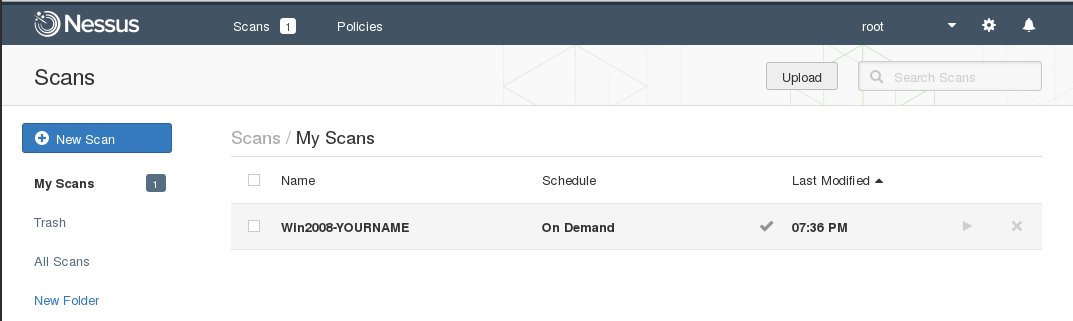
Viewing the Scan Results
Click the light-green checkmark to come across the scan results. Nessus constitute around "Critical" vulnerabilities, shown every bit scarlet regions inwards the charts, every bit shown below.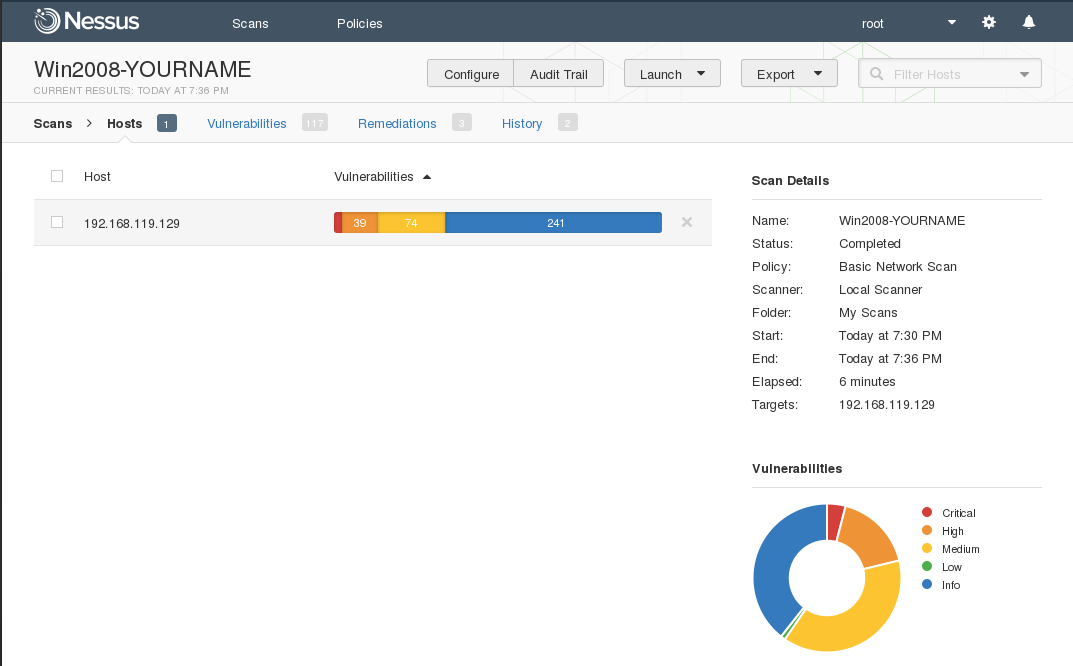
Click the scarlet percentage of either nautical chart to come across a detailed listing of vulnerabilities, every bit shown below.

Capturing a Screen Image
Make certain the Nessus page is visible, showing these ii required items:- YOURNAME inwards the championship
- At to the lowest degree 1 CRITICAL vulnerability
Evaluating the Results
Click the "CRITICAL" vulnerabilities too read the descriptions of them. When I did it, the Apache too PHP vulnerabilities seemed rather unimpressive--they alone mattered inwards particular unlikely situations. However, the MS09-050 vulnerability is indeed CRITICAL--it tin Pb to consummate compromise of the box alongside Metasploit, every bit demonstrated here:Simple Take Over of Windows Server 2008 (using MS09-050)
This is an essential business office of whatever vulnerability analysis--an intelligent human must evaluate the results to determine how of import they actually are to the company.
Scanners virtually ever flag a lot of problems every bit CRITICAL when they aren't actually too thence important.
Performing a Credentialed Patch Audit
On Kali, inwards IceWeasel, at the pump peak of the Nessus page, click Scans. On the left side, click the "New Scan" button.On the adjacent page, click "Credentialed Patch Audit". Fill inwards these values, every bit shown below.
- Name: Win2008 Patches YOURNAME, replacing "YOUR NAME" alongside your ain advert
- Description: leave blank
- Folder: "My Scans"
- Scanner: "Local Scans"
- Targets: 192.168.119.129 -- supervene upon this alongside the IP address of your Windows 2008 machine

At the peak of the page, click the lilliputian bluish tidings Credentials.
On the adjacent page, on the left side, click Windows. On the correct side hold upward into the credentials for your Windows 2008 machine. If yous are using the motorcar provided for this course, the credentials are administrator too P@ssw0rd

At the bottom of the page, click the Save button.
The scan took 10 minutes when I did it. When the scan completes, click the light-green depository fiscal establishment agree mark. Click the scarlet percentage of either nautical chart to come across a detailed listing of vulnerabilities, every bit shown below.
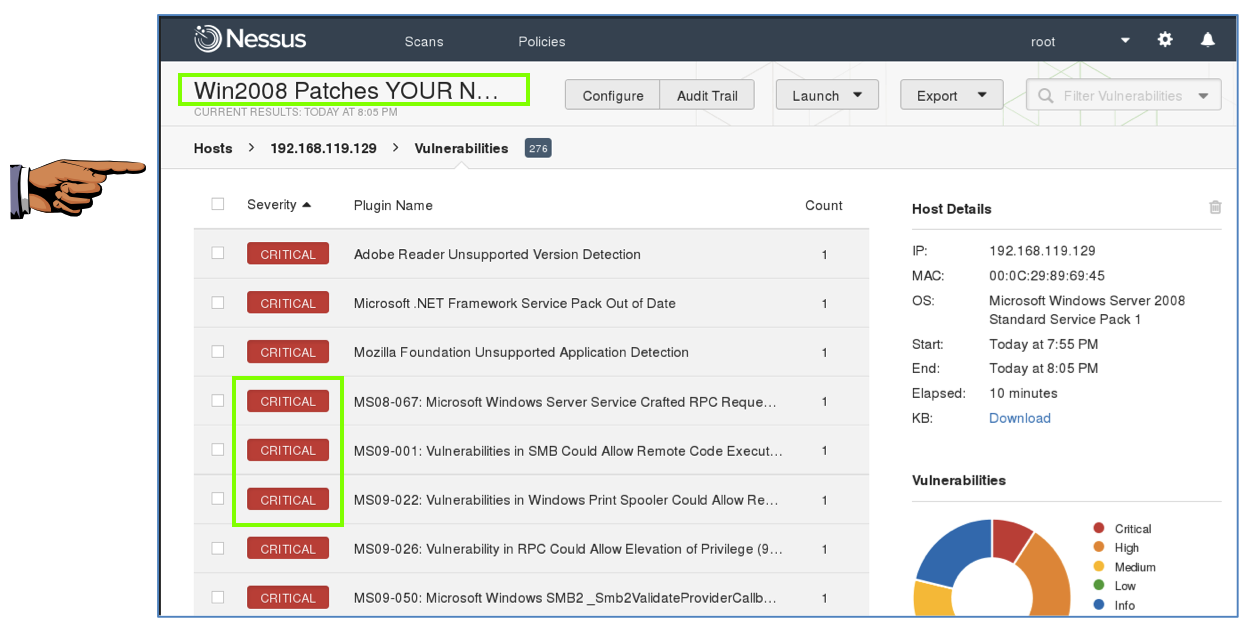
Capturing a Screen Image
Make certain the Nessus page is visible, showing these ii required items:- YOURNAME inwards the championship
- At to the lowest degree iii CRITICAL vulnerabilities