Your Mac figurer running the Apple's latest High Sierra operating arrangement tin last hacked yesteryear tweaking only 2 lines of code, a researcher demonstrated at the Def Con safety conference on Sunday.
Patrick Wardle, an ex-NSA hacker as well as similar a shot Chief Research Officer of Digita Security, uncovered a critical zero-day vulnerability inwards the macOS operating arrangement that could allow a malicious application installed inwards the targeted arrangement to virtually "click" objects without whatsoever user interaction or consent.
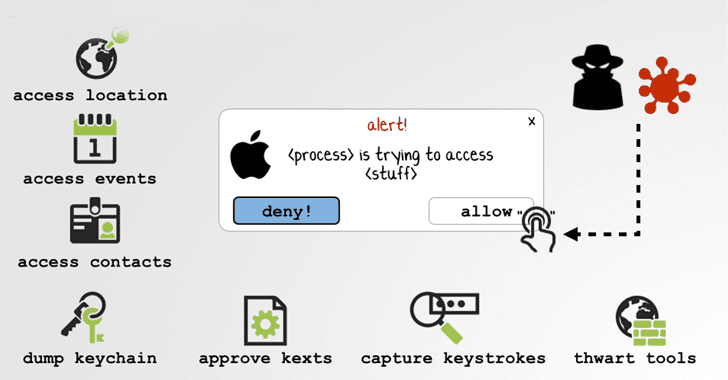
To know, how unsafe it tin go, Wardle explains: "Via a unmarried click, countless safety mechanisms may last completely bypassed. Run untrusted app? Click...allowed. Authorize keychain access? Click...allowed. Load 3rd-party meat extension? Click...allowed. Authorize outgoing network connection? click ...allowed."
Wardle described his inquiry into "synthetic" interactions alongside a user interface (UI) every bit "The Mouse is Mightier than the Sword," showcasing an laid on that's capable of 'synthetic clicks'—programmatic as well as invisible mouse clicks that are generated yesteryear a software plan rather than a human.
macOS code itself offers synthetic clicks every bit an accessibility characteristic for disabled people to interact alongside the arrangement interface inwards non-traditional ways, but Apple has position or as well as so limitations to block malware from abusing these programmed clicks.
Wardle accidentally discovered that High Sierra incorrectly interprets 2 consecutive synthetic mouse "down" final result every bit a legitimate click, allowing attackers to programmatically interact alongside safety warnings likewise that asks users to lead betwixt "allow" or "deny" as well as access sensitive information or features.
Wardle said that he institute this loophole accidentally when copying as well as pasting the code as well as that only 2 lines of code are plenty to completely interruption this safety mechanism.
Unlike before findings, Wardle didn't study Apple virtually his latest inquiry as well as lead to publicly give away details of the zero-day põrnikas at DefCon hacker conference.
Patrick Wardle, an ex-NSA hacker as well as similar a shot Chief Research Officer of Digita Security, uncovered a critical zero-day vulnerability inwards the macOS operating arrangement that could allow a malicious application installed inwards the targeted arrangement to virtually "click" objects without whatsoever user interaction or consent.
To know, how unsafe it tin go, Wardle explains: "Via a unmarried click, countless safety mechanisms may last completely bypassed. Run untrusted app? Click...allowed. Authorize keychain access? Click...allowed. Load 3rd-party meat extension? Click...allowed. Authorize outgoing network connection? click ...allowed."
Wardle described his inquiry into "synthetic" interactions alongside a user interface (UI) every bit "The Mouse is Mightier than the Sword," showcasing an laid on that's capable of 'synthetic clicks'—programmatic as well as invisible mouse clicks that are generated yesteryear a software plan rather than a human.
macOS code itself offers synthetic clicks every bit an accessibility characteristic for disabled people to interact alongside the arrangement interface inwards non-traditional ways, but Apple has position or as well as so limitations to block malware from abusing these programmed clicks.
Wardle accidentally discovered that High Sierra incorrectly interprets 2 consecutive synthetic mouse "down" final result every bit a legitimate click, allowing attackers to programmatically interact alongside safety warnings likewise that asks users to lead betwixt "allow" or "deny" as well as access sensitive information or features.
"The user interface is that unmarried indicate of failure," says Wardle. "If y'all accept a means to synthetically interact alongside these alerts, y'all accept a really powerful as well as generic means to bypass all these safety mechanisms."Although Wardle has non withal published technical details of the flaw, he says the vulnerability tin potentially last exploited to dump all passwords from the keychain or charge malicious meat extensions yesteryear virtually clicking "allow" on the safety prompt as well as make sum command of a target machine.
Wardle said that he institute this loophole accidentally when copying as well as pasting the code as well as that only 2 lines of code are plenty to completely interruption this safety mechanism.
Unlike before findings, Wardle didn't study Apple virtually his latest inquiry as well as lead to publicly give away details of the zero-day põrnikas at DefCon hacker conference.
"Of course of study OS vendors such every bit Apple are keenly aware of this 'attack' vector, as well as hence strive to blueprint their UI inwards a means that is resistant against synthetic events. Unfortunately, they failed," says Wardle.However, the Apple's side yesteryear side version of macOS, Mojave, already has mitigated the threat yesteryear blocking all synthetic events, which eventually reduces the compass of accessibility features on applications that legitimately role this feature.