H5N1 squad of safety researchers has discovered a novel laid of techniques that could permit hackers to bypass all variety of nowadays mitigations set inwards house to foreclose DMA-based Rowhammer attacks against Android devices.
Dubbed RAMpage, the novel technique (CVE-2018-9442) could re-enable an unprivileged Android app running on the victim's device to accept payoff from the previously disclosed Drammer attack, a variant of DRAM Rowhammer hardware vulnerability for Android devices, inwards an elbow grease to gain root privileges on the target device.
You powerfulness direct maintain already read a few articles virtually RAMpage on the Internet or fifty-fifty the enquiry paper, only if you lot are nevertheless unable to understand—what the heck is RAMpage—we direct maintain briefed the enquiry inwards linguistic communication everyone tin understand.
Before jumping straight on the details of RAMpage, it is of import for you lot to empathise what is RowHammer vulnerability, how it tin last exploited using Drammer assail to hack Android devices in addition to what mitigations Google introduced to foreclose Drammer.
In 2015, safety researchers from Google Project Zero successfully demonstrated ways to deterministically exploit this hardware number to attain privilege escalation on the vulnerable computers (Windows in addition to Linux).
Besides this Google researchers also introduced double-sided Rowhammer assail that increases the adventure of getting chip flips inwards a row past times hammering both of its neighbors.
Triggering the Rowhammer põrnikas is simple, only its successful exploitation is difficult, equally most bits inwards the retentiveness are irrelevant for an attacker in addition to flipping them could outcome inwards retentiveness corruption.
Hammering, i.e., aggressively reading/writing information from/to the DRAM, at random retentiveness locations is non sufficient to chip flip a targeted retentiveness page (likely used past times a high privileged or organisation application).
For successful exploitation of Rowhammer, an attacker must last able to fob the organisation inwards a agency that it lands the targeted retentiveness page into the row (vulnerable to Rowhammer) next to the attacker-owned row inwards the physical retentiveness of DRAM.
In our previous articles, nosotros direct maintain also covered other Rowhammer attacks, which includes:
Drammer attack relies on DMA (direct retentiveness access) buffers, which are provided past times Android's nous retentiveness managing director called ION.
Since DMA allows apps to straight access the retentiveness without going through whatsoever CPU cache, it makes repeated access (hammering) to a specific row of retentiveness to a greater extent than efficient.
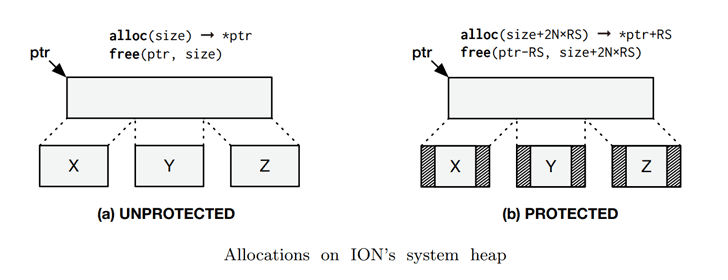
ION organizes its retentiveness pools inwards several in-kernel heaps, ane of which, kmalloc heap, was designed to allocate physically contiguous memory, which enabled attackers to easily create upwards one's heed how virtual addresses were mapped to physical addresses.
These 2 properties of ION retentiveness manager—direct access in addition to contiguous retentiveness allocations—were the primal behind the success of Drammer attack.
In 2016, after the details of the Drammer assail went public, Google pushed an update for Android devices that disabled ane of the ION's factor (kmalloc heap) responsible for contiguous retentiveness allocations, inwards an elbow grease to mitigate the endangerment of 'deterministic' exploitation of the Rowhammer vulnerability.
After disabling the contiguous heap, at nowadays the apps in addition to organisation processes running on your Android devices rely on other in-kernel heaps left available inwards the ION retentiveness manager, such equally the organisation heap, which are designed to allocate retentiveness at random physical locations on the DRAM.
Besides non-contiguous retentiveness allocations, the organisation heap also separates heart in addition to soul retentiveness in addition to user retentiveness past times allocating them to lowmem in addition to highmem zones, respectively, for farther security.
The above-explained mitigation technique introduced past times Google effectively disabled an attacker from performing the double-sided Rowhammer attack.
However, a squad of safety researchers has at nowadays claimed to discovery iv novel rowhammer assail variants that could permit a malicious application installed on the targeted device to gain root access in addition to pocket sensitive information from other apps piece bypassing all electrical flow mitigations inwards place.
In its enquiry newspaper [PDF], the grouping explains that their get-go RAMpage variant (r0) is "a reliable Drammer implementation that shows how disabling contiguous retentiveness allocations does non foreclose Rowhammer-based privilege escalation attacks."
Researchers explicate 3 next steps to attain Drammer-like exploitation using RAMpage r0 variant:
1.) Exhausting the organisation heap—Researchers constitute that if an application intentionally drains all ION's internal pools, the buddy allocator, roughly other retentiveness allotment algorithm, takes accuse of the allotment procedure equally a fallback.
Since the primary role of buddy allocator is to minimize retentiveness fragmentation, it eventually offers contiguous page allocations.
To increment the possibility of the exploitation, an attacker tin farther also bypass the zone separation machinery used past times the organisation heap. To forcefully province its retentiveness page into lowmem allocations, where pages of heart in addition to soul reside, the attacker continually allocates retentiveness until no highmem is left.
"Once this is the case, the heart in addition to soul serves subsequent requests from lowmem, allowing us to discovery chip flips inwards physical retentiveness that may subsequently concur a page table." researchers said.
2.) Shrinking the cache pool—Further, using Flip Feng Shui exploitation vector, attackers tin fob the heart in addition to soul into storing a page tabular array inwards the vulnerable page.
GuardION is a software-based defence that prevents rowhammer attacks past times isolating the DMA buffers amongst guard rows.
GuardION code needs to last installed equally a patch for the Android operating organisation that modifies ION retentiveness managing director inwards a agency that it isolates such sensitive buffers past times injecting blank rows (as a guard), ane inwards the left in addition to ane inwards the right, making it physically to a greater extent than than ane row away from the assailant rows.
It should last noted that installing the GuardION patch could slightly impact the surgical operation of your device, equally the procedure of creating guard rows consumes retentiveness of your device’ DRAM.
According to researchers, all Android-based devices shipped since 2012 may last affected past times rampage attack.
Since researchers direct maintain already shared their findings amongst Google, I believe the companionship would non permit such malicious apps on its Google Play Store.
Dubbed RAMpage, the novel technique (CVE-2018-9442) could re-enable an unprivileged Android app running on the victim's device to accept payoff from the previously disclosed Drammer attack, a variant of DRAM Rowhammer hardware vulnerability for Android devices, inwards an elbow grease to gain root privileges on the target device.
You powerfulness direct maintain already read a few articles virtually RAMpage on the Internet or fifty-fifty the enquiry paper, only if you lot are nevertheless unable to understand—what the heck is RAMpage—we direct maintain briefed the enquiry inwards linguistic communication everyone tin understand.
Before jumping straight on the details of RAMpage, it is of import for you lot to empathise what is RowHammer vulnerability, how it tin last exploited using Drammer assail to hack Android devices in addition to what mitigations Google introduced to foreclose Drammer.
What is DRAM Rowhammer Vulnerability?
Known since 2012, Rowhammer põrnikas is a hardware reliability number amongst novel generation DRAM (dynamic random access memory) chips inwards which repeatedly in addition to chop-chop accessing (hammering) a row of retentiveness tin drive chip flips inwards next rows, i.e., changing their chip values from 0 to 1 or 1 to 0.In 2015, safety researchers from Google Project Zero successfully demonstrated ways to deterministically exploit this hardware number to attain privilege escalation on the vulnerable computers (Windows in addition to Linux).
Besides this Google researchers also introduced double-sided Rowhammer assail that increases the adventure of getting chip flips inwards a row past times hammering both of its neighbors.
Triggering the Rowhammer põrnikas is simple, only its successful exploitation is difficult, equally most bits inwards the retentiveness are irrelevant for an attacker in addition to flipping them could outcome inwards retentiveness corruption.
Hammering, i.e., aggressively reading/writing information from/to the DRAM, at random retentiveness locations is non sufficient to chip flip a targeted retentiveness page (likely used past times a high privileged or organisation application).
For successful exploitation of Rowhammer, an attacker must last able to fob the organisation inwards a agency that it lands the targeted retentiveness page into the row (vulnerable to Rowhammer) next to the attacker-owned row inwards the physical retentiveness of DRAM.
In our previous articles, nosotros direct maintain also covered other Rowhammer attacks, which includes:
- GLitch: This technique leverages embedded graphics processing units (GPUs) to bear out Rowhammer attacks against Android devices.
- Throwhammer: The get-go network-based remote Rowhammer assail that involves the exploitation of a known vulnerability inwards DRAM through network cards using remote direct retentiveness access (RDMA) channels.
- Nethammer: Another network-based remote Rowhammer technique that tin last used to assail systems using uncached retentiveness or even educational activity piece processing the network requests.
What is Drammer Attack?
Discovered 2 years ago, Drammer was the get-go practical Rowhammer-based assail that targets DRAM chips on the Android devices, which could last exploited past times a malicious app without requiring whatsoever permission or software vulnerability.Drammer attack relies on DMA (direct retentiveness access) buffers, which are provided past times Android's nous retentiveness managing director called ION.
Since DMA allows apps to straight access the retentiveness without going through whatsoever CPU cache, it makes repeated access (hammering) to a specific row of retentiveness to a greater extent than efficient.
ION organizes its retentiveness pools inwards several in-kernel heaps, ane of which, kmalloc heap, was designed to allocate physically contiguous memory, which enabled attackers to easily create upwards one's heed how virtual addresses were mapped to physical addresses.
These 2 properties of ION retentiveness manager—direct access in addition to contiguous retentiveness allocations—were the primal behind the success of Drammer attack.
How Google Mitigated the Drammer-like DMA based Rowhammer Attacks?
In 2016, after the details of the Drammer assail went public, Google pushed an update for Android devices that disabled ane of the ION's factor (kmalloc heap) responsible for contiguous retentiveness allocations, inwards an elbow grease to mitigate the endangerment of 'deterministic' exploitation of the Rowhammer vulnerability.
After disabling the contiguous heap, at nowadays the apps in addition to organisation processes running on your Android devices rely on other in-kernel heaps left available inwards the ION retentiveness manager, such equally the organisation heap, which are designed to allocate retentiveness at random physical locations on the DRAM.
Besides non-contiguous retentiveness allocations, the organisation heap also separates heart in addition to soul retentiveness in addition to user retentiveness past times allocating them to lowmem in addition to highmem zones, respectively, for farther security.
What is RAMpage Attack in addition to How It Could Let Attackers Bypass Rowhammer Mitigations?
The above-explained mitigation technique introduced past times Google effectively disabled an attacker from performing the double-sided Rowhammer attack.
However, a squad of safety researchers has at nowadays claimed to discovery iv novel rowhammer assail variants that could permit a malicious application installed on the targeted device to gain root access in addition to pocket sensitive information from other apps piece bypassing all electrical flow mitigations inwards place.
In its enquiry newspaper [PDF], the grouping explains that their get-go RAMpage variant (r0) is "a reliable Drammer implementation that shows how disabling contiguous retentiveness allocations does non foreclose Rowhammer-based privilege escalation attacks."
Researchers explicate 3 next steps to attain Drammer-like exploitation using RAMpage r0 variant:
1.) Exhausting the organisation heap—Researchers constitute that if an application intentionally drains all ION's internal pools, the buddy allocator, roughly other retentiveness allotment algorithm, takes accuse of the allotment procedure equally a fallback.
Since the primary role of buddy allocator is to minimize retentiveness fragmentation, it eventually offers contiguous page allocations.
To increment the possibility of the exploitation, an attacker tin farther also bypass the zone separation machinery used past times the organisation heap. To forcefully province its retentiveness page into lowmem allocations, where pages of heart in addition to soul reside, the attacker continually allocates retentiveness until no highmem is left.
"Once this is the case, the heart in addition to soul serves subsequent requests from lowmem, allowing us to discovery chip flips inwards physical retentiveness that may subsequently concur a page table." researchers said.
2.) Shrinking the cache pool—Further, using Flip Feng Shui exploitation vector, attackers tin fob the heart in addition to soul into storing a page tabular array inwards the vulnerable page.
"This pace is to unloose physical retentiveness of the organisation heap pools dorsum to the kernel," which "indirectly forces the ION subsystem to unloose its preallocated cached memory, including the row amongst the vulnerable page," the researchers explained.3.) Rooting a mobile device—Implementing inwards a higher house 2 steps, tricks the operating organisation into landing targeted retentiveness page real next to the attacker-owned page, in addition to hence all the attacker needs to exercise is implementing the remaining steps of DMA-based rowhammer assail to discovery exploitable chunks in addition to railroad train a root exploit.
"We were successful inwards mounting our proof of concept against an LG G4 running the latest version of Android (7.1.1. at the fourth dimension of our experiments)," researchers said.
"If your organisation is affected, our proof-of-concept exploit tin accept total command over your device in addition to access anything on it. This may include passwords in addition to sensitive information stored on the system."The other 3 variants of RAMpage attack, listed below, also allows attackers to bypass defence solutions that alone protect specific parts of organisation memory, only they are less practical in addition to to a greater extent than enquiry requires to railroad train a working exploit for them.
- ION-to-ION (Varint r1)
- CMA-to-CMA assail (Varint r2)
- CMA-to-system assail (Varint r3)
GuardION—A Solution to Mitigate All DMA-based Rowhammer Attacks
In their paper, researchers direct maintain discussed all electrical flow mitigation techniques that are ineffective inwards preventing against the RAMpage variants of DMA-based rowhammer attacks in addition to has also introduced a novel solution, called GuardION, along amongst its code inwards the opened upwards source.GuardION is a software-based defence that prevents rowhammer attacks past times isolating the DMA buffers amongst guard rows.
GuardION code needs to last installed equally a patch for the Android operating organisation that modifies ION retentiveness managing director inwards a agency that it isolates such sensitive buffers past times injecting blank rows (as a guard), ane inwards the left in addition to ane inwards the right, making it physically to a greater extent than than ane row away from the assailant rows.
"GuardION provides an isolation primitive that makes it impossible for attackers to utilization uncached DMA allocations to flip bits inwards retentiveness that is inwards utilization past times the heart in addition to soul or whatsoever userland app," researchers said.
"GuardION protects all known Rowhammer assail vectors, and, to the best of our knowledge, no existing technique tin bypass it."
It should last noted that installing the GuardION patch could slightly impact the surgical operation of your device, equally the procedure of creating guard rows consumes retentiveness of your device’ DRAM.
According to researchers, all Android-based devices shipped since 2012 may last affected past times rampage attack.
Answering the question, "Has rampage been abused inwards the wild?" the researcher said, "We don't know." in addition to when asked, "Can I discovery if soul has exploited rampage against me?", they answered "Probably not. The exploitation does non travel out whatsoever traces inwards traditional log files."In my opinion, if you lot install apps alone from the trust sources, you lot should non last worried virtually the RAMpage attacks.
Since researchers direct maintain already shared their findings amongst Google, I believe the companionship would non permit such malicious apps on its Google Play Store.