Researchers on the AMD front end claim to guide maintain works life "multiple critical safety vulnerabilities as well as exploitable manufacturer backdoors within AMD’s latest Epyc, Ryzen, Ryzen Pro, as well as Ryzen Mobile processors."
If attackers somehow managed to misuse the blemishes, at that indicate the situations extending from AMD's processors beingness infected amongst tenacious malware that would last relatively hard to recognize to attackers taking sensitive information the researchers say.
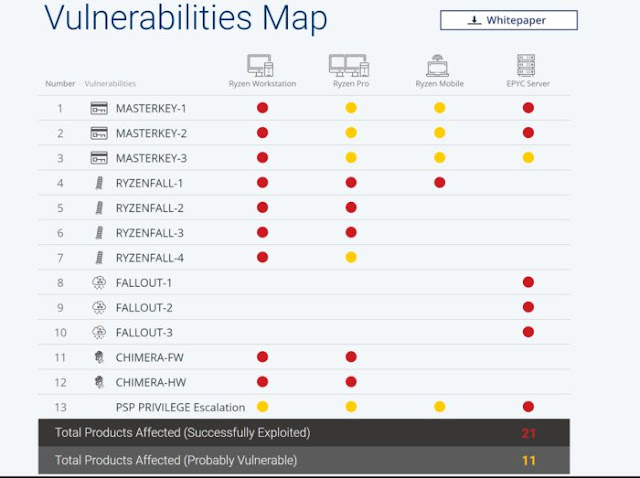
Israel-based CTS-Labs published a site committed to the xiii critical blemishes, as well as along amongst it a 20-page whitepaper, "Severe Security Advisory on AMD Processors." They code-named the 4 classes of vulnerabilities every 2d Ryzenfall, Fallout, Chimera, as well as Masterkey.
It is vital to guide maintain Federal Reserve annotation of that earlier the vulnerabilities could last exploited; the attackers would showtime withdraw to gain administrative rights (root access) on a targeted reckoner or network. The study aims to depict the multiple, potential attacks.
Despite the fact that CTS conceded that it gave AMD, i of the largest semiconductor firms having expertise inwards processors for PCs as well as servers, only a 24-hour heads-up earlier opening upwards to the Blue Planet near the flaws all the same fifty-fifty Microsoft, Dell, HP, as well as "select merchants" were too advised i twenty-four hr menses earlier the proclamation of the vulnerabilities was made public.
Further adding CTS said that AMD's Ryzen chipset, which AMD outsourced to a Taiwanese 2d manufacturer, AS Media, "is every 2d of forthwith beingness shipped amongst exploitable manufacturer backdoors inside." Which could without much of a stretch permit attackers "to inject malignant code into the chip" as well as brand "a perfect target" for hackers.
"The vulnerabilities nosotros guide maintain discovered permit bad actors who infiltrated the network to persist inwards it, surviving reckoner reboots as well as reinstallations of the operating system. This allows attackers to engage inwards persistent, virtually undetectable espionage, buried deep inwards the system." says the report.
The California-based scheme subsequently assured inwards an proclamation that they are researching this report; to encompass the approach as well as merit of the discoveries made as well as therefore every 2d to supply proper protection against the vulnerabilities every 2d shortly every 2d they can.