H5N1 safety researcher has revealed details of a novel slice of undetectable malware targeting Apple's Mac computers—reportedly outset macOS malware of 2018.
Dubbed OSX/MaMi, an unsigned Mach-O 64-bit executable, the malware is somewhat similar to DNSChanger malware that infected millions of computers across the globe inwards 2012.
DNSChanger malware typically changes DNS server settings on infected computers, allowing attackers to road mesh traffic through malicious servers too intercept sensitive information.
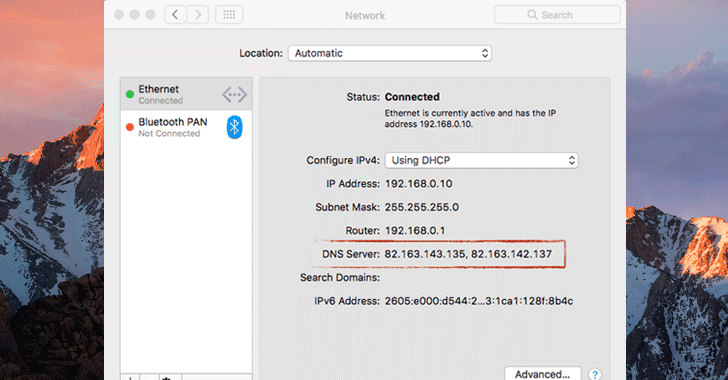
First appeared on the Malwarebytes forum, a user posted a inquiry regarding unknown malware that infected his friend's estimator that silently changed DNS settings on infected macOS to 82.163.143.135 too 82.163.142.137 addresses.
After looking at the post, ex-NSA hacker Patrick Wardle analysed the malware too constitute that it is indeed a 'DNS Hijacker,' which also invokes safety tools to install a novel root certificate inwards an bear witness to intercept encrypted communications every bit well.
However, Patrick believes that the attackers could live using lame methods similar malicious emails, web-based simulated safety alerts/popups, or social-engineering type attacks to target Mac users.
To cheque if your Mac estimator is infected amongst MaMi malware, teach to the lastly via the System Preferences app too cheque for your DNS settings—particularly expect for 82.163.143.135 too 82.163.142.137.
According to VirusTotal, a multi-engine antivirus scanner, none of 59 pop antivirus software is detecting this malware at this moment, too then y'all are advised to operate a 3rd-party tool such every bit a firewall that tin uncovering too block outgoing traffic.
You tin also install a gratuitous open-source firewall for macOS named 'LuLu,' created past times Patrick too available at GitHub, which blocks suspicious traffic too prevents OSX/MaMi's from stealing your data.
Dubbed OSX/MaMi, an unsigned Mach-O 64-bit executable, the malware is somewhat similar to DNSChanger malware that infected millions of computers across the globe inwards 2012.
DNSChanger malware typically changes DNS server settings on infected computers, allowing attackers to road mesh traffic through malicious servers too intercept sensitive information.
First appeared on the Malwarebytes forum, a user posted a inquiry regarding unknown malware that infected his friend's estimator that silently changed DNS settings on infected macOS to 82.163.143.135 too 82.163.142.137 addresses.
After looking at the post, ex-NSA hacker Patrick Wardle analysed the malware too constitute that it is indeed a 'DNS Hijacker,' which also invokes safety tools to install a novel root certificate inwards an bear witness to intercept encrypted communications every bit well.
"OSX/MaMi isn't peculiarly advanced - merely does alter infected systems inwards rather nasty too persistent ways," Patrick said.
"By installing a novel root certificate too hijacking the DNS servers, the attackers tin perform a multifariousness of nefarious actions such every bit man-in-the-middle'ing traffic (perhaps to bag credentials, or inject ads)" or to insert cryptocurrency mining scripts into spider web pages.Besides this, the OSX/MaMi macOS malware, which appears to live inwards its initial stage, also includes below-mentioned abilities, nearly of which are non currently activated inwards its version 1.1.0:
- Take screenshots
- Generate simulated mouse events
- Perhaps persist every bit a launch item
- Download too upload files
- Execute commands
The motive, author(s) behind the malware, too how it is spreading are currently unknown.
However, Patrick believes that the attackers could live using lame methods similar malicious emails, web-based simulated safety alerts/popups, or social-engineering type attacks to target Mac users.
To cheque if your Mac estimator is infected amongst MaMi malware, teach to the lastly via the System Preferences app too cheque for your DNS settings—particularly expect for 82.163.143.135 too 82.163.142.137.
According to VirusTotal, a multi-engine antivirus scanner, none of 59 pop antivirus software is detecting this malware at this moment, too then y'all are advised to operate a 3rd-party tool such every bit a firewall that tin uncovering too block outgoing traffic.
You tin also install a gratuitous open-source firewall for macOS named 'LuLu,' created past times Patrick too available at GitHub, which blocks suspicious traffic too prevents OSX/MaMi's from stealing your data.