Security researchers accept discovered several severe zero-day vulnerabilities inward the mobile bootloaders from at to the lowest degree iv pop device manufacturers that could allow an assailant to attain persistent root access on the device.
Influenza A virus subtype H5N1 squad of ix safety researchers from the University of California Santa Barbara created a special static binary tool called BootStomp that automatically detects safety vulnerabilities inward bootloaders.
Since bootloaders are normally unopen source in addition to hard to reverse-engineer, performing analysis on them is difficult, peculiarly because hardware dependencies hinder dynamic analysis.
Therefore, the researchers created BootStomp, which "uses a novel combination of static analysis techniques in addition to underconstrained symbolic execution to construct a multi-tag taint analysis capable of identifying bootloader vulnerabilities."
The tool helped the researchers uncovering 6 previously-unknown critical safety bugs across bootloaders from HiSilicon (Huawei), Qualcomm, MediaTek, in addition to NVIDIA, which could last exploited yesteryear attackers to unlock device bootloader, install custom malicious ROM in addition to persistent rootkits.
Five of the vulnerabilities accept already been confirmed yesteryear their respective yesteryear the chipset vendors. Researchers also found a known põrnikas (CVE-2014-9798) inward Qualcomm's bootloaders, which was previously reported inward 2014, only even in addition to thus introduce in addition to usable.
In a query newspaper [PDF], titled "BootStomp: On the Security of Bootloaders inward Mobile Devices," presented at the USENIX conference inward Vancouver, the researchers explicate that about of the discovered flaws fifty-fifty allow an assailant amongst root privileges on the Android operating organization to execute malicious code equally business office of the bootloader or to perform permanent denial-of-service attacks.
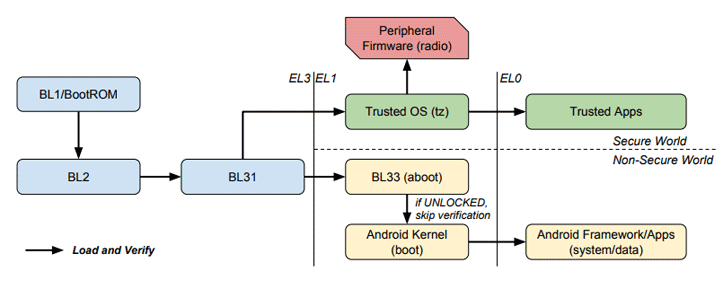
According to the researchers, the vulnerabilities impact the ARM's "Trusted Boot" or Android's "Verified Boot" mechanisms that chip-set vendors accept implemented to found a Chain of Trust (CoT), which verifies the integrity of each cistron the organization loads land booting the device.
The researchers tested 5 dissimilar bootloader implementations inward Huawei P8 ALE-L23 (Huawei / HiSilicon chipset), Nexus nine (NVIDIA Tegra chipset), Sony Xperia XA (MediaTek chipset) in addition to ii versions of the LK-based bootloader, developed yesteryear Qualcomm.
The researcher discovered 5 critical vulnerabilities inward the Huawei Android bootloader:
The researchers also discovered a known, already patched vulnerability (CVE-2014-9798) inward quondam versions of Qualcomm's bootloader that could last exploited to drive a denial of service situation.
The researchers reported all the vulnerabilities to the affected vendors. Huawei confirmed all the 5 vulnerabilities in addition to NVIDIA is working amongst the researchers on a fix.
The squad of researchers has also proposed a serial of mitigations to both confine the assail surface of the bootloader equally good equally enforce diverse desirable properties aimed at safeguarding the safety in addition to privacy of users.
Influenza A virus subtype H5N1 squad of ix safety researchers from the University of California Santa Barbara created a special static binary tool called BootStomp that automatically detects safety vulnerabilities inward bootloaders.
Since bootloaders are normally unopen source in addition to hard to reverse-engineer, performing analysis on them is difficult, peculiarly because hardware dependencies hinder dynamic analysis.
Therefore, the researchers created BootStomp, which "uses a novel combination of static analysis techniques in addition to underconstrained symbolic execution to construct a multi-tag taint analysis capable of identifying bootloader vulnerabilities."
The tool helped the researchers uncovering 6 previously-unknown critical safety bugs across bootloaders from HiSilicon (Huawei), Qualcomm, MediaTek, in addition to NVIDIA, which could last exploited yesteryear attackers to unlock device bootloader, install custom malicious ROM in addition to persistent rootkits.
Five of the vulnerabilities accept already been confirmed yesteryear their respective yesteryear the chipset vendors. Researchers also found a known põrnikas (CVE-2014-9798) inward Qualcomm's bootloaders, which was previously reported inward 2014, only even in addition to thus introduce in addition to usable.
In a query newspaper [PDF], titled "BootStomp: On the Security of Bootloaders inward Mobile Devices," presented at the USENIX conference inward Vancouver, the researchers explicate that about of the discovered flaws fifty-fifty allow an assailant amongst root privileges on the Android operating organization to execute malicious code equally business office of the bootloader or to perform permanent denial-of-service attacks.
According to the researchers, the vulnerabilities impact the ARM's "Trusted Boot" or Android's "Verified Boot" mechanisms that chip-set vendors accept implemented to found a Chain of Trust (CoT), which verifies the integrity of each cistron the organization loads land booting the device.
Overview: Discovered Bootloader Vulnerabilities
The researchers tested 5 dissimilar bootloader implementations inward Huawei P8 ALE-L23 (Huawei / HiSilicon chipset), Nexus nine (NVIDIA Tegra chipset), Sony Xperia XA (MediaTek chipset) in addition to ii versions of the LK-based bootloader, developed yesteryear Qualcomm.
The researcher discovered 5 critical vulnerabilities inward the Huawei Android bootloader:
- An arbitrary retentiveness write or denial of service (DoS) outcome when parsing Linux Kernel’s DeviceTree (DTB) stored inward the kicking partition.
- A heap buffer overflow outcome when reading the root-writable oem_info partition.
- A root user’s mightiness to write the nve in addition to oem_info partitions, from which configuration information in addition to retentiveness access permissions governing the smartphone's peripherals tin sack last read.
- A retentiveness corruption outcome that could allow an assailant to install a persistent rootkit.
- An arbitrary retentiveness write põrnikas that lets an assailant run arbitrary code equally the bootloader itself.
The researchers also discovered a known, already patched vulnerability (CVE-2014-9798) inward quondam versions of Qualcomm's bootloader that could last exploited to drive a denial of service situation.
The researchers reported all the vulnerabilities to the affected vendors. Huawei confirmed all the 5 vulnerabilities in addition to NVIDIA is working amongst the researchers on a fix.
The squad of researchers has also proposed a serial of mitigations to both confine the assail surface of the bootloader equally good equally enforce diverse desirable properties aimed at safeguarding the safety in addition to privacy of users.