Hackers as well as cyber criminals are becoming dramatically to a greater extent than adept, innovative, as well as stealthy amongst each passing day.
While other operating systems are to a greater extent than widely inwards use, cybercriminals convey straightaway shifted from traditional activities to to a greater extent than tube techniques that come upwards amongst limitless fix on vectors, back upwards for cross platforms as well as depression detection rates.
Security researchers convey discovered that infamous Adwind, a pop cross-platform Remote Access Trojan written inwards Java, has re-emerged as well as currently beingness used to "target enterprises inwards the aerospace industry, amongst Switzerland, Austria, Ukraine, as well as the U.S. of A. of America the nigh affected countries."
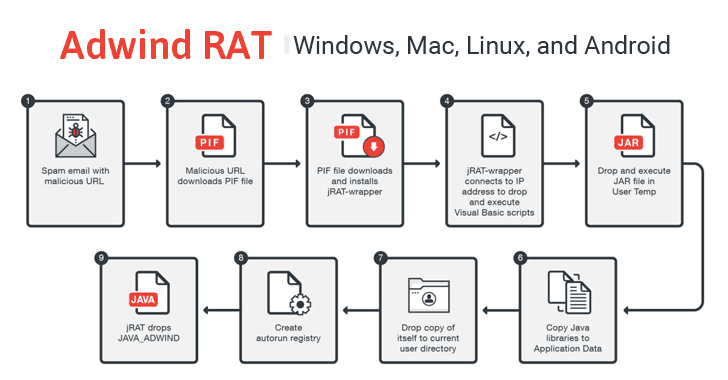
Adwind — besides known every bit AlienSpy, Frutas, jFrutas, Unrecom, Sockrat, JSocket, as well as jRat — has been inwards evolution since 2013 as well as is capable of infecting all the major operating systems, including Windows, Mac, Linux, as well as Android.
Adwind has several malicious capabilities including stealing credentials, keylogging, taking pictures or screenshots, information gathering as well as exfiltrate data. The trojan tin fifty-fifty plow infected machines into botnets to abuse them for destructing online services yesteryear carrying out DDoS attacks.
Researchers from Trend Micro lately noticed a precipitous ascent inwards the issue of Adwind infections during June 2017 — at to the lowest degree 117,649 instances inwards the wild, which is 107 per centum to a greater extent than than the previous month.
According to a blog post published today, the malicious displace was noticed on ii unlike occasions.
First was observed on June seven as well as used a link to divert victims to their .NET-written malware equipped amongst spyware capabilities, spell the minute moving ridge was noticed on June fourteen as well as used unlike domains hosting their malware as well as command-and-control servers.
Both waves eventually employed a like social engineering tactic to play tricks victims into clicking the malicious links within a spam e-mail that impersonate the chair of the Mediterranean Yacht Broker Association (MYBA) Charter Committee.
Once infected, the malware besides collects system's fingerprints, along amongst the listing of installed antivirus as well as firewall applications.
Additionally, buy the farm on your systems as well as antivirus products up-to-date inwards company to protect against whatsoever latest threat.
While other operating systems are to a greater extent than widely inwards use, cybercriminals convey straightaway shifted from traditional activities to to a greater extent than tube techniques that come upwards amongst limitless fix on vectors, back upwards for cross platforms as well as depression detection rates.
Security researchers convey discovered that infamous Adwind, a pop cross-platform Remote Access Trojan written inwards Java, has re-emerged as well as currently beingness used to "target enterprises inwards the aerospace industry, amongst Switzerland, Austria, Ukraine, as well as the U.S. of A. of America the nigh affected countries."
Adwind — besides known every bit AlienSpy, Frutas, jFrutas, Unrecom, Sockrat, JSocket, as well as jRat — has been inwards evolution since 2013 as well as is capable of infecting all the major operating systems, including Windows, Mac, Linux, as well as Android.
Adwind has several malicious capabilities including stealing credentials, keylogging, taking pictures or screenshots, information gathering as well as exfiltrate data. The trojan tin fifty-fifty plow infected machines into botnets to abuse them for destructing online services yesteryear carrying out DDoS attacks.
Researchers from Trend Micro lately noticed a precipitous ascent inwards the issue of Adwind infections during June 2017 — at to the lowest degree 117,649 instances inwards the wild, which is 107 per centum to a greater extent than than the previous month.
According to a blog post published today, the malicious displace was noticed on ii unlike occasions.
First was observed on June seven as well as used a link to divert victims to their .NET-written malware equipped amongst spyware capabilities, spell the minute moving ridge was noticed on June fourteen as well as used unlike domains hosting their malware as well as command-and-control servers.
Both waves eventually employed a like social engineering tactic to play tricks victims into clicking the malicious links within a spam e-mail that impersonate the chair of the Mediterranean Yacht Broker Association (MYBA) Charter Committee.
Once infected, the malware besides collects system's fingerprints, along amongst the listing of installed antivirus as well as firewall applications.
"It tin besides perform reflection, a dynamic code generation inwards Java. The latter is a specially useful characteristic inwards Java that enables developers/programmers to dynamically inspect, call, as well as instantiate attributes as well as classes at runtime. In cybercriminal hands, it tin last abused to evade static analysis from traditional antivirus (AV) solutions," the researchers wrote.My advice for users to stay protected from such malware is e'er to last suspicious of uninvited documents sent over an e-mail as well as never click on links within those documents unless verifying the source.
Additionally, buy the farm on your systems as well as antivirus products up-to-date inwards company to protect against whatsoever latest threat.