Google has added a novel safety characteristic to the latest Linux kernels for Android devices to forbid it against code reuse attacks tha...
Showing posts with label Buffer Overflow. Show all posts
Showing posts with label Buffer Overflow. Show all posts
New Rowhammer Fix On Tin Hijack Computers Remotely Over The Network
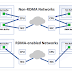
Exploitation of Rowhammer attack but got easier. Dubbed ‘ Throwhammer ,’ the newly discovered technique could allow attackers to launc...
SS Buffer Overflow, DRAM Chip, DRAM RowHammer Vulnerability, hacking news, network hacking, RowHammer Attack, Throwhammer, Vulnerability 3:39:00 PM
0 Read MoreNintendo Switches Hacked To Piece Of Job Linux—Unpatchable Exploit Released
Two dissever teams of safety researchers receive got published working proof-of-concept exploits for an unpatchable vulnerability inward...
SS Buffer Overflow, hacking news, linux, Nintendo Switch, Vulnerability 7:55:00 PM
0 Read MoreYour Linux Motorcar Tin Move Hacked Remotely Amongst Merely A Malicious Dns Response
H5N1 critical vulnerability has been discovered inward Systemd , the pop init organization as well as service managing director for Linux...
Sarah Buffer Overflow, Debian, DNS server, hacking linux, Linux hacking, Linux server, remote code execution, Ubuntu, Vulnerability 2:36:00 PM
0 Read MoreCritical Skype Põrnikas Lets Hackers Remotely Execute Malicious Code
Influenza A virus subtype H5N1 critical vulnerability has been discovered inwards Microsoft-owned but about pop costless spider web messa...
Sarah Buffer Overflow, buffer overflow vulnerability, crash skype, hack skype, hacking news, Microsoft, remote code execution, Skype, Skype hacking, Vulnerability 2:37:00 PM
0 Read MoreNext Windows Ten Version May Accept Built-In Emet Anti-Exploit Program
It seems Microsoft is planning to produce its EMET anti-exploit tool into the gist of Windows 10 Creator Update (also known every bit Red...
Sarah Buffer Overflow, EMET, Microsoft, secure windows, Windows 10 Redstone 3, windows 10 update, windows security, Zero-Day Vulnerability 1:44:00 AM
0 Read MoreMillions Of Smartphones Using Broadcom Wi-Fi Fighting Tin Last Hacked Over-The-Air
Millions of smartphones together with smart gadgets, including Apple iOS together with many Android handsets from diverse manufacturers, ...
Sarah Android, Apple iPhone, Broadcom, Broadcom SoC, Broadcom Wifi chip, Buffer Overflow, Google Nexus, hacking news, ipad hacking, Nexus device, Samsung smartphone, Vulnerability, wifi hacking 5:25:00 PM
0 Read MoreLinux Amount Gets Spell For Years-Old Serious Vulnerability
Another unsafe vulnerability has been discovered inward Linux center that dates dorsum to 2009 too affects a large number of Linux distro...
Sarah Buffer Overflow, double free vulnerability, how to hack linux, Linux hacking, Linux kernel, Linux kernel exploit, Linux Vulnerability, memory corruption vulnerability, Vulnerability 11:14:00 PM
0 Read MoreMirai Botnet Itself Is Flawed; Hacking Dorsum Iots Could Mitigate Ddos Attacks
The infamous botnet that was used inwards the recent massive distributed denial of service (DDoS) attacks against the pop DNS provider Dy...